The public cloud is everywhere
The advantages of utilizing cloud infrastructure have brought organizations of all sizes and verticals to adopt it to some extent. Public cloud adoption reached 94% in 2019 which means virtually every organization utilizes the cloud in some way. 38% of enterprises surveyed said that public cloud was their top priority for 2019.
Increasingly, central IT and security teams assume responsibility for security and governance of the public cloud infrastructure in their organizations. As organizations use the cloud for more business-critical and customer-facing applications, the security requirements and concerns associated with that infrastructure mature as well.
Public cloud security issues
Cloud security continues to be a top concern for IT organizations. While some security requirements and challenges for public cloud usage are the same as private clouds, others differ.
Challenges specific to security in the public cloud are in four key areas:
- Complexity: The flexibility and elasticity of the cloud infrastructure often enables advanced software architectures, and specifically the use of container-based infrastructure. These architectures involve a larger number of entities and services with independent lifecycles.
- Scale: With a public cloud, the number of entities and the level of legitimate internal communication paths increases significantly. Managing security for a much larger number of entities, each with its development lifecycle, becomes a complex task.
- Pace: The pace of delivery is one of the major drivers for cloud adoption. Applications delivered on the cloud tend to be subject to multiple changes and entail a very high rate of change. Each change may introduce new security vulnerabilities and blind spots, requiring security to adapt quickly.
- Visibility: By design, the underlying infrastructure is not visible and is the responsibility of the cloud provider. Other aspects, such as granting access, securing the application and the hosted OS, remain the responsibility of the cloud user. This shared responsibility model generates a change in workflow for security professionals. A high percentage of security professionals state visibility is their top concern for securing their cloud.
Top security concerns in the cloud
Cloud security professionals focus on protecting their critical data. Whether it is data loss or leakage, or breaking compliance with regards to data privacy and confidentiality, they must keep track of the threats which put at risk their data kept in the cloud. The following threats are the most prevalent and are considered to be the most urgent issues to tackle:
Misconfiguration or faulty setup of the cloud platform is the single worrisome issue. Due to the complexity, pace and scale of cloud applications, this has become the underlying cause for security incidents in cloud platforms in recent years. Misconfiguration can relate to granting access, setting policies and configuring the network.
Unauthorized access by various attacks on credentials and resulting misuse of employee credentials. This is a major concern because the impact of gaining privileged credentials in a cloud platform can be devastating.
Insecure interfaces or APIs involve both cloud infrastructure and application APIs. For example, many of the security incidents in the past few years involved an overly accessible S3 configuration. In addition, many of the cloud applications design involve heavy usage of API-based interaction, where security is often overly permissive.
Account, service or traffic hijacking may result in the ability to access data. In public cloud infrastructure, the opportunity to perform such attacks causes concern due to the shared infrastructure and the fact that if access rights are not managed well enough, the impact can be severe. Also, this is an attack vector which starts at the user which is in many cases the weakest link in the chain in terms of security.
How breach attack simulation can help
Breach and Attack Simulation enables organizations to test their security controls against simulated attacks. SafeBreach BAS platform enables BAS at a scale which is suitable to the challenges of managing cloud security.
- Testing by safely running actual attacks in production allows for understanding what really works and what may be misconfigured. Focusing on the security and impact enables improved security efficiency and faster pace.
- Focusing on security at a cloud scale requires that the most critical items are prioritized and the most impactful actions are taken. By enabling continuous, comprehensive and automated testing, one can obtain the required visibility for this to be effective.
- Continuous validation allows for keeping up with the rapidly changing cloud environment and being notified when something is broken. As with any continuous delivery and integration practice, the security must adopt the same cadence to keep up.
- Automation throughout the process allows security teams to achieve all of this effortlessly. The SafeBreach platform does not require instructions and performs testing fully autonomously. This enables performing all of the above in cloud scale.
Use cases for validating cloud native security
The use cases for validating cloud native security include cloud control plane security and container security.
Validating cloud control plane security
The cloud control plane includes capabilities that are usually exposed by the cloud IaaS provider API: access management, storage and other services and network configuration. In the shared security responsibility model, the user is responsible for these.
The cloud control plane represents a new and [for hackers] lucrative attack surface which is highly susceptible to misconfiguration and human error due to the high complexity of the environment.
SafeBreach breach attack simulation is able to interact with the cloud IaaS API and perform various operations which simulate attacker techniques and behaviors in order to validate security policies. The simulations also confirm whether controls are correctly configured to block attacker behaviors and expose where these may deviate from desired configurations.
SafeBreach simulation data can translate attack simulation data for threat or risk-based analysis, which is helpful in showing the environment posture in terms of the actual attack surface and threat exposure.
Validating container environments in cloud workload security
Container environments represent the infrastructure which enables cloud native architecture. Containers are very useful; they enable organizations to accelerate development processes and shorten software release cycles. In 2018, use of containers was up to 57 percent.
From a security perspective, the container environment behaves differently than traditional environments. Fundamentally, container environments are characterized by a large number of small entities (microservices), interacting with each other in a complex application structure. Each entity requires a different set of security settings.
Cloud native security solutions are designed to secure container environments in light of the different architecture and complexities. Such tools focus on specific core areas:
- Microsegmentation
- System configuration enforcement and validation
- Application integrity
- Memory protection
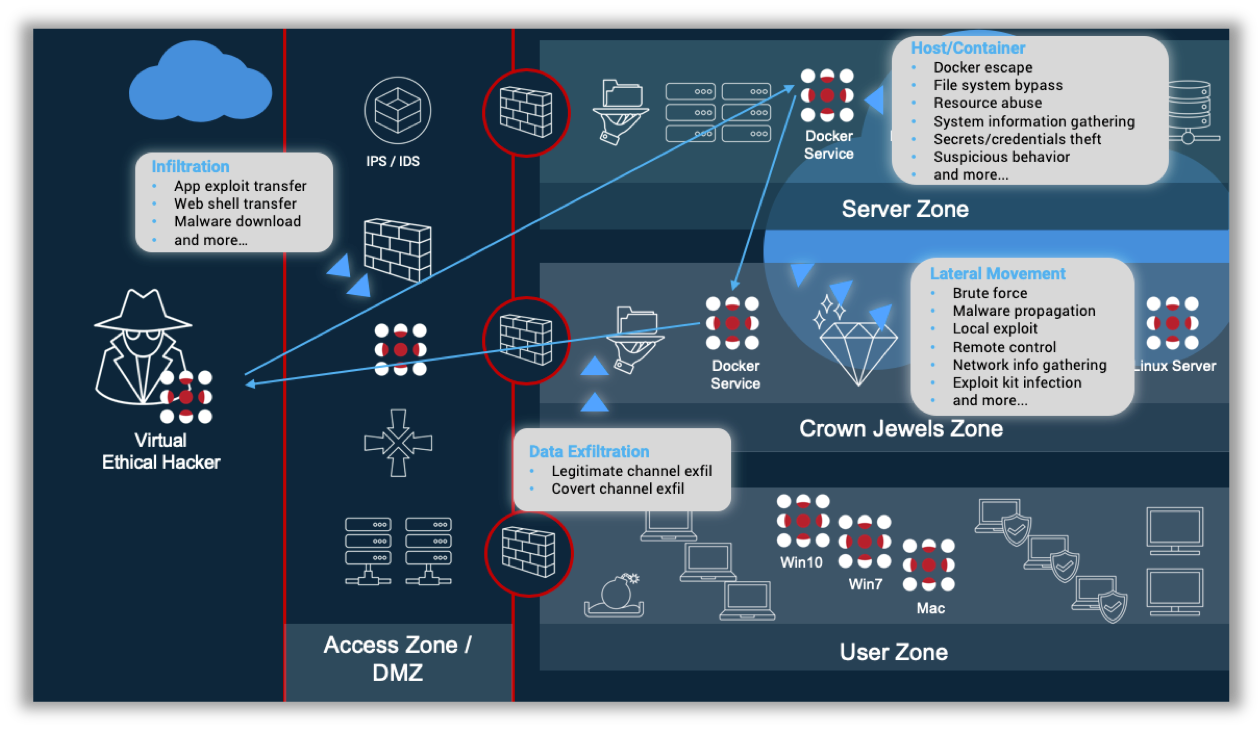
Conclusion: The entire attack surface, and the entire kill chain
Its new container security capabilities make SafeBreach the only breach attack simulation platform able to run attacks across the attack surfaces to validate configuration of the relevant security controls. SafeBeach Cloud Native Security capabilities enable users to visualize the entire kill chain of a potential attack on their applications, identify the most critical gaps and holistically remediate them.