Ensure you are safe against known & emerging threats.
The SafeBreach Hacker’s Playbook™ includes 30,000+ attack methods, enabling you to replicate a hacker’s mindset and continuously test the efficacy of your security controls against advanced attacks. When new US-CERT and FBI Flash alerts are published, our research team adds relevant content to the platform within 24 hours—guaranteed.
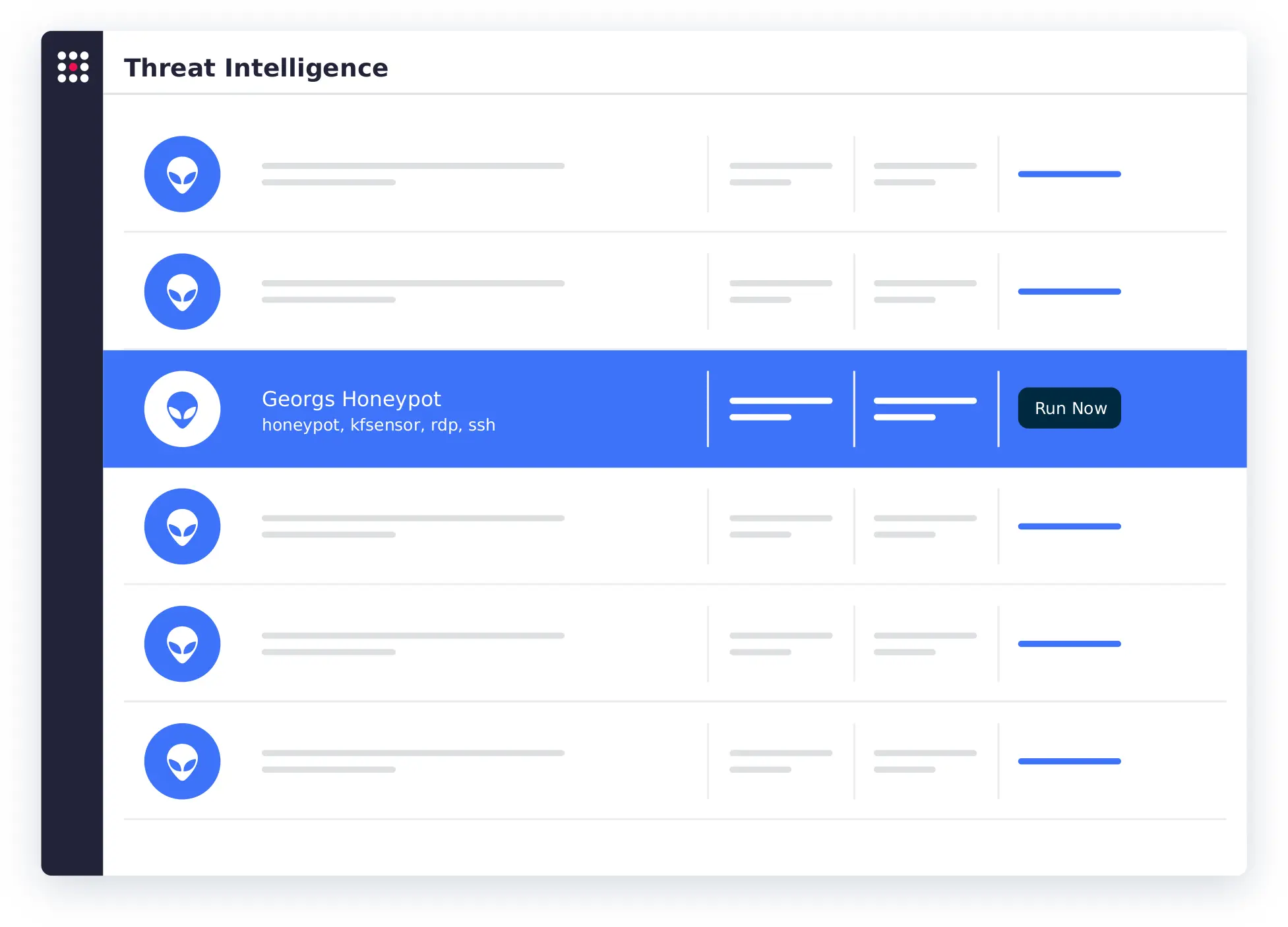
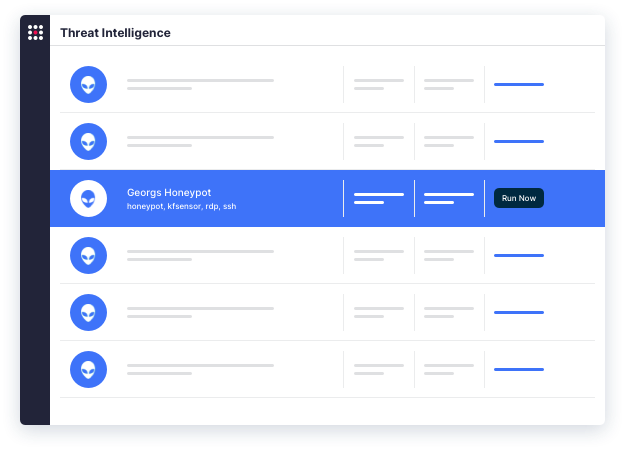
Operationalize your threat intelligence.
SafeBreach integrates with leading threat intelligence vendors—like CrowdStrike, Google, Palo Alto Networks, Recorded Future, Splunk, and ThreatConnect—so you can run simulations using TTPs and IOCs from your preferred provider.
Customize existing attacks or build new ones to replicate relevant threats and leverage threat-specific tactics—then safely put your security controls to the test with continuous, automated attack simulations.
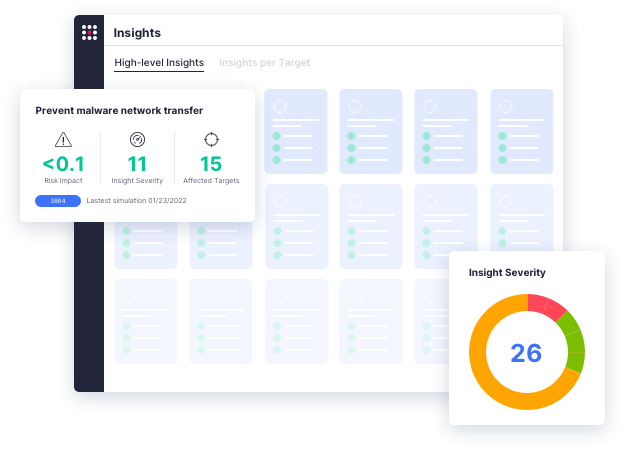
Automatically map simulation results to the MITRE ATT&CK® framework to understand how your defenses perform against specific attacker techniques and threat groups. Utilize customizable dashboards to quickly understand gaps, evaluate risks, and inform strategic planning.

Experience the Power of a Truly Proactive Defense
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.