Know how well your security investments are working.
Security teams own and operate dozens of tools, but misconfigurations or drift over time can mean those tools aren’t effectively protecting against attacks. SafeBreach validates that each security control is operating optimally, both individually and in orchestration with other tools in your stack.

Take your detection engineering program to the next level.
See how SafeBreach can help validate custom detections, alert pipelines, and incident response workflows to reduce cyber risk across your security program.
Make your security controls work for you.
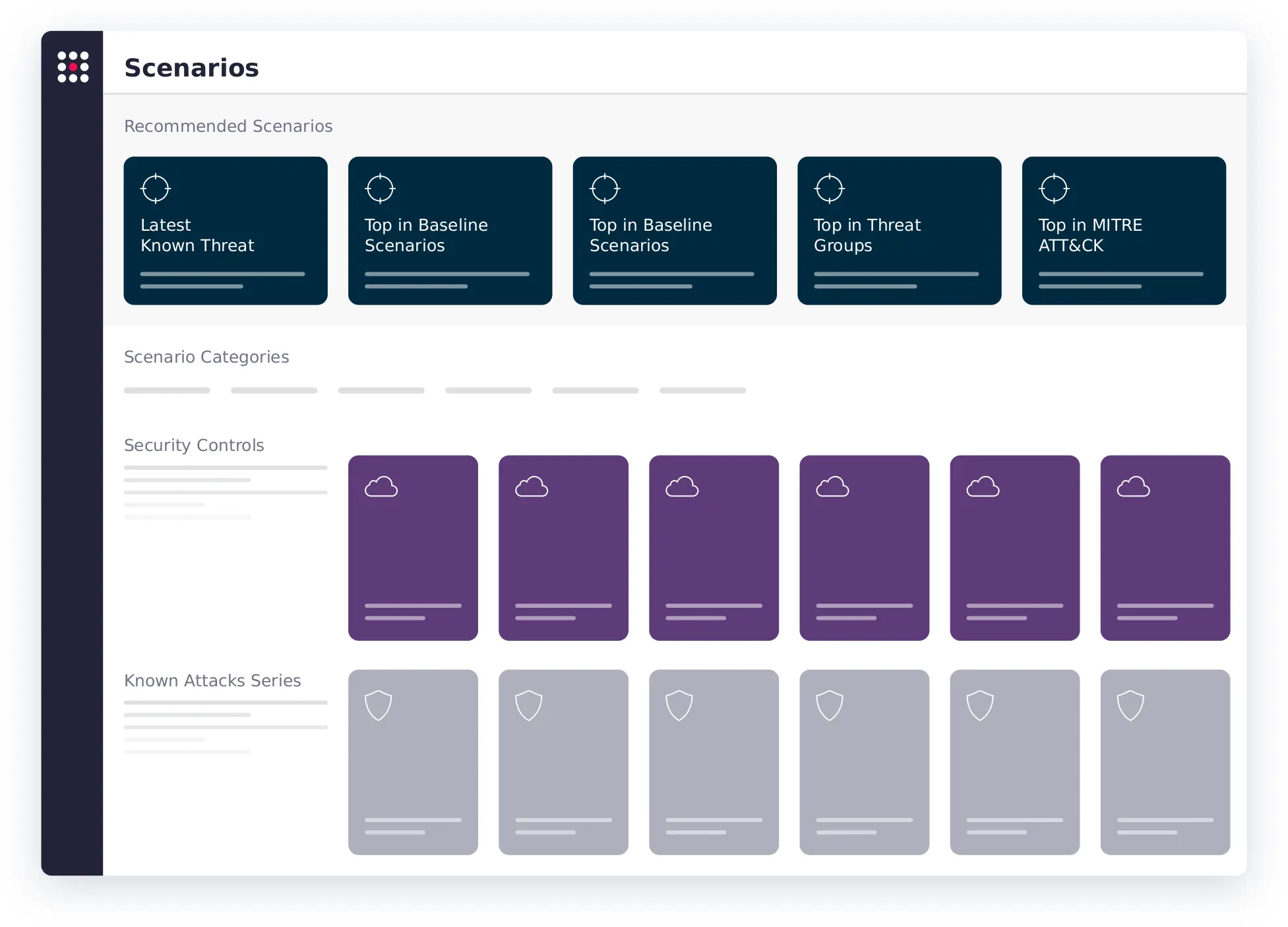
Execute continuous, automated attack simulations from the SafeBreach Hacker’s Playbook™—or build your own—across a variety of controls, including web, endpoint, email, network inspection, network access, container, and cloud.
Identify which controls blocked, detected, or missed attacks, so you can pinpoint ineffective settings, underperforming tools, and incident response gaps. Understand your overall risk score, identify the top exploited protocols and ports, and map attack simulation results to the MITRE ATT&CK® framework to visualize how your defenses performed.
Take immediate action to shore up defenses by implementing suggested remediation steps prioritized by the highest risk. Analyze overall organizational posture broken down by category, including the MITRE ATT&CK framework, known attacks, and threat groups, so your team can understand the efficacy of existing systems at a glance, inform resourcing decisions, and enhance strategic alignment.

Experience the Power of a Truly Proactive Defense
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.