
Earlier this year, SafeBreach held its first-ever Validate Summit at Levi’s Stadium in Santa Clara, California. This in-person event brought together top cybersecurity leaders and innovators to discuss the changing requirements to build and optimize a proactive security organization.
The day’s keynote, kickoff address was delivered by Srinivas “Srini” Tummalapenta, distinguished engineer and CTO of IBM Security Services. With more than 20 years of experience—and nine patents to his name—Srini takes a keen interest in transforming multi-cloud connectivity, while enhancing security and threat monitoring for comprehensive enterprise hybrid cloud infrastructure. He regularly meets with CISOs and other security leaders to help drive better industry-wide cyber outcomes.
In this first edition of our Voices from Validate series we revisit the highlights and unpack the key takeaways from Srini’s motivational presentation in which he shared his unique strategy to prepare for, protect against, and ultimately—theoretically—prevent business disruption.
The Evolving Threat Landscape
“Cybersecurity is a team sport. It’s not us against each other. It’s us versus the bad guys.” – Srinivas Tummalapenta, IBM Security Services
IBM’s annual data breach and threat intelligence reports are curated from exercises and analysis of over 4,000 IBM clients. When viewed in conjunction with Crowdstrike’s Global Threat Report, a clear picture emerges of our current threat landscape. Here are just some of the striking findings Srini presented:
- Ransomware is on the rise, representing 21% of attacks
- 41% of these attacks exploited phishing for initial access
- It takes less than 92 minutes to gain a foothold in an IT environment
- The fastest observed attack took only 18 minutes
When ransomware attacks happen, the results can be crippling on a wide scale, bringing down massive city infrastructures, hospital systems, and other vital functions. As these attacks grow more frequent, with increased variety in methods and vectors, the biggest concern is not data breach or malware—it’s disruption of an entire business’s operations.
Attackers are increasingly using AI and automation to go faster and faster after more and more targets, and today’s organizations lack the reliable controls and resources needed to keep up. Security technology is seldom configured and maintained properly. Skill retention is difficult, especially in this volatile job market, and information is siloed without enterprise-wide visibility of the entire security ecosystem, leaving many at risk for catastrophic business disruption.
Disrupting the Disruption
Srini challenged organizations to do better by rising above the reactive, detect-and-respond security approach that leaves too much to chance. To move in this direction, he proposed a proactive three-step remedy:
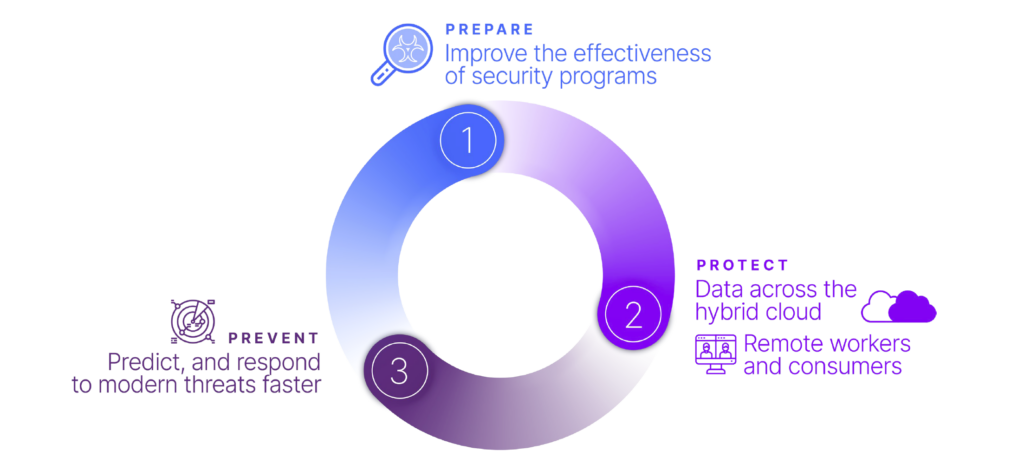
- Prepare. Improve the effectiveness of your security programs now. Focus not just on the firewalls and EDRs, but on the overall hygiene and hardening of your controls—they’re not just there for compliance.
- Protect. Identify where your data resides and catalog it to ensure it’s fully protected, from across the hybrid cloud to your remote workers and consumers.
- Prevent. Enable actual means of prediction—because you can only prevent what you can predict—so you can proactively respond to and prevent modern threats faster and more effectively.
By preparing detection and protection technologies, along with reliable analytics and well-trained analyst support, organizations can bolster their resilience to attacks. This all starts with adopting a risk-based approach for which Srini offered the following checklist:
- Harden system controls, improve detection of security drift, and automate to remediate
- Prioritize patching of the most critical weaponized exploits in your risk-based vulnerability management process, based on your environment
- Optimize protection security technology (e.g., firewall rule optimization, IPS tuning, etc.)
- Invest in continuous improvement through MITRE ATT&CK-based SIEM posture assessment and recommendations
- Automate adversarial simulation with breach and attack simulation (BAS) to proactively assess and enforce your security control ecosystem
For Srini, happy analysts equal happy clients. That’s why he highlighted the need to continuously improve the skills and expertise of security analysts through immersive education and ongoing training for the latest attacks. Leveraging the SafeBreach BAS solution has proven to be a highly effective way to make this possible, enabling analysts to get a hands-on feel for real-world threats before there’s a real-world issue in a client environment. In turn, the clients are happy because they see faster response and resolution, and once SafeBreach is also being run in their environment, they see increased value in their existing security tools and investments.
Enhanced AI & Automation
To keep up with increasingly sophisticated attackers, Srini has focused on improving security response time through AI-enabled, multilateral detection and response. He also stressed the importance of automating every step of the threat management lifecycle to enable security analyst teams to work more efficiently and effectively on behalf of their clients.
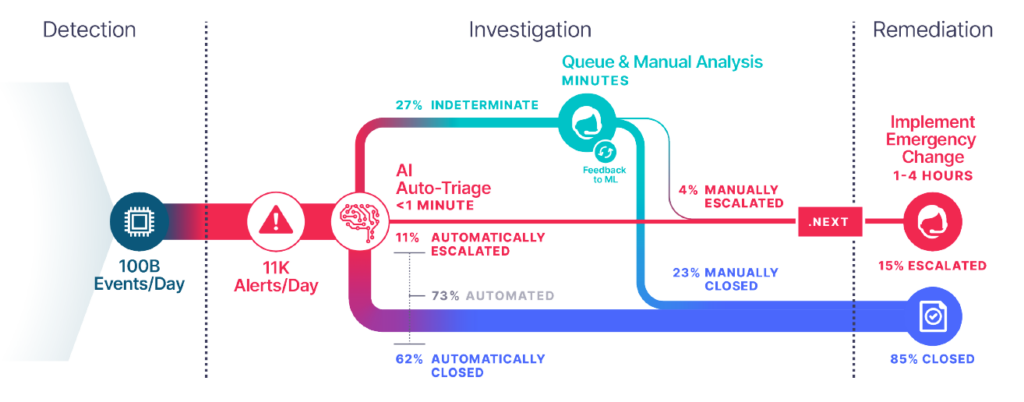
IBM Security Services processes over 100 billion network events every day, resulting in an average of 11,000 security alerts. Even with hundreds of analysts, that’s far too much for human processing power alone. Using rules-based techniques and machine-learning algorithms, based on actual analyst and simulation behavior, 73% of those alerts are currently triaged automatically—in under one minute. From there, 62% of alerts are automatically closed, drastically reducing noise for analysts and triage/investigation time so they can focus on the incoming manual analysis that truly requires their expert attention.
Using the SafeBreach BAS platform, IBM Security Services is able to empower analysts and AI systems to learn from attack-pattern behavior and simulation data, creating a robust “early-warning system.” This system curates the information analysts need, when they need it, to help them proactively assess security control posture and remediate gaps. It also brings Srini that much closer to his goal of preventing business disruption by way of accurate, actionable predictions.
To learn more about how BAS solutions help security analysts learn and implement more efficient processes, contact SafeBreach to schedule a personalized demo. And stay tuned for more Voices from Validate posts in the coming weeks as we continue to share industry-leading insights and perspectives from SafeBreach’s Validate summit.

