Breach and attack simulation (BAS) is fast emerging as an invaluable tool for overstretched security teams and proactive CISOs. For those who have adopted BAS systems, the pain of managing ever-expanding security tool portfolios is eased by the ability to automatically and continuously validate their efficacy.
As BAS implementation begins to take hold worldwide, we thought this year’s InfoSec Europe event in London would be a great opportunity to check the pulse of the industry’s evolving perspective—particularly in the UK and surrounding region. We surveyed security and IT professionals to learn how they validate their controls—if at all—how they view BAS, and how prepared they feel to face a range of potential threats.
Survey Says…
First off, we asked our security professional respondents how they currently validate their security controls:

After that diverse start, we wanted to ensure participants were qualified to answer subsequent survey questions. When asked how familiar they were with the policies, processes, and technologies their organization uses to monitor and validate its security controls, an encouraging 70.2% said they were either familiar or very familiar. This does, however, mean we lost 29.8% of respondents at this stage.
Moving forward with our more “knowledgeable” participants, we wanted to understand what they knew about BAS. 48% correctly defined it as an advanced security test, although 53.7% believed it could be considered a penetration test, and 42.6% consider it an automated security audit. So, while many have heard of BAS, there are still some misconceptions about the value the technology provides.
When asked about their frequency of running attack simulations, we found that:
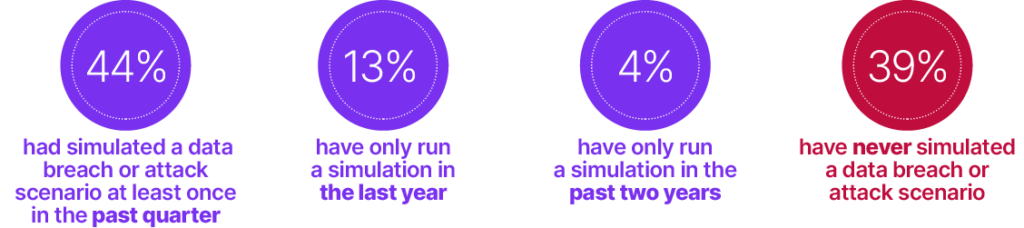
Are You Prepared for the Next Attack?
When asked which threats our respondents felt they could currently deal with in a proactive manner, the results weren’t exactly promising:
- A strong 87% felt they were at least able to deal with phishing threats
- But only 37% of respondents felt they were prepared for a data breach
- 35.2% felt they were prepared for spear phishing
- And 48.1% felt they were prepared for a malware infection
Interestingly, despite most of our respondents feeling unprepared for every threat aside from phishing, 70.4% told us they felt their organization was ready to respond to any security incident. The same number thought their organization had the proper tools to identify threats and remediate security gaps quickly and efficiently. Of those who admitted their organization was unprepared for a security incident, 36.8% felt that a lack of knowledge was the key issue, while 42.1% cited a lack of funding.
Finally, we asked our participants what metrics and data they typically provided in a report to their executive team and board of directors—because we all know who is really asking the tough questions:

What Does It All Mean?
Responses from our survey participants seem to highlight a few illuminating takeaways about enterprise security right now:
- Many organizations are relying on point-in-time validation. While it’s encouraging that the majority of those surveyed use at least one method to validate their security ecosystem, it’s concerning that so many rely on point-in-time penetration testing. While this approach to validation will provide insight into gaps and vulnerabilities, it’s often only completed annually and provides snapshot-in-time results that quickly become outdated.
- How does BAS help? BAS solutions provide ongoing, continuous security validation by safely executing breach simulations across the cyber kill chain to constantly validate security controls against the most up-to-date threats. The SafeBreach Hacker’s Playbook, for example, offers access to more than 25,000 attack methods and the industry’s only 24-hour SLA on adding US-CERT, FBI Flash, and other critical alerts, so organizations always have access to the latest coverage.
- Organizations lack the resources to adequately support preparedness. Lack of knowledge and proper funding seemed to be a leading contributor to individual’s feelings about their organization’s lack of preparedness against specific threats like malware and data breaches, a frustration our own CEO Guy Bejerano experienced himself as a former CISO.
- How does BAS help? By continuously and proactively validating security controls, BAS platforms provide reliable, accessible data about an organization’s level of preparedness against new and existing threats. This information identifies critical security gaps and helps prioritize remediation efforts before breaches occur. BAS also allows organizations to understand security control efficacy in a way that helps inform resourcing decisions, justify or secure additional budgets where needed, and formulate long-term security plans that ensure strategic alignment.
- Organizations are surprisingly overconfident. A significant number of survey participants indicated they felt underprepared for most threats, aside from phishing. Yet, a whopping 70% told us they felt their organization was ready to respond to any security incident. This contradiction fits with a general trend of overconfidence within the cybersecurity industry, where too many organizations are operating under the illusion of safety, despite access to hard data.
- How does BAS help? An enormous amount of information exists about the attack methods and vulnerabilities attackers have exploited in the past that can be used not only to ensure protection against known threats, but also to make educated predictions about future threats. BAS allows organizations to leverage this information to proactively test their defenses and receive quantifiable data about their overall security posture—continuously. In the case of the recent Cisco breach, only BAS technology could provide real-time assurance of an organization’s ability to withstand similar methods—and only SafeBreach added immediate coverage for those attacks.
Want to learn more about the unique capabilities of BAS technology? SafeBreach has you covered. Download our Four Pillars of BAS white paper or check out our ongoing BAS 101 educational blog series to learn more. Or better yet, request a demo today, and one of our cybersecurity experts will be happy to show you how it works.