On December 2nd, the Federal Bureau of Investigation (FBI) issued a flash alert to highlight ongoing malicious cyber activity by threat actors using Cuba ransomware to target and compromise at least 49 individual entities in five critical infrastructure sectors, including but not limited to the financial, government, healthcare, manufacturing, and information technology. Details of the various tactics, techniques, and procedures (TTPs) are described in FBI Flash Alert CU-000156-MW. According to the information currently available, these threat actors have demanded at least USD $74 million from their victims and have received at least USD $43.9 million in ransom payments to date.
It appears that the Cuba ransomware is distributed using Hancitor malware, a malware loader often leveraged for dropping or executing stealers, such as Remote Access Trojans (RAT) and other types of ransomware, onto the victims’ networks. Hancitor malware actors often leverage phishing emails, Microsoft Exchange vulnerabilities, compromised credentials, or legitimate Remote Desktop Protocol (RDP) tools to gain initial access to a victim’s network. The Cuba ransomware threat actors have also used legitimate Windows services—such as PowerShell, PsExec, and other unspecified services to leverage Windows Admin privileges and remotely execute their ransomware code. It was also noted that the encrypted files all have the ”.cuba” extension. Additional technical details and breakdown of the attack can be found in FBI Flash Alert CU-000156-MW.
NOTE – The SafeBreach Hacker’s Playbook has been updated to include the newly discovered tactics and techniques from this FBI Flash alert. We encourage you to test your preparedness against this ransomware variant by running the new and existing attacks listed below.
Two newly developed playbook methods related to FBI Flash Alert CU-000156-MW (Cuba Ransomware)
- #6836 – Communication with CubaRansomware using HTTP (Infiltration)
- #6837 – Communication with a real malicious CubaRansomware server using HTTP/S (Infiltration)
We would also like to highlight that current SafeBreach customers already had a certain level of protection against these attacks as the Hacker’s Playbook already included many (22) of the tactics, techniques, and procedures (TTPs) preferred by these threat actors (including the ones being reused for the current attacks). These attacks are listed below:
- #6724 – Pre-execution phase of Cuba malware
- #5762 – Pre-execution phase of CobaltStrike_Beacon malware
- #6725 – Write Cuba malware to disk
- #5763 – Write CobaltStrike_Beacon malware to disk
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #2273 – Pass the Hash over SMB using Mimikatz
- #5765 – Transfer of CobaltStrike_Beacon malware over HTTP/S
- #5767 – Email CobaltStrike_Beacon malware as a ZIP attachment
- #6577 – Remote exploitation of Microsoft Exchange ProxyShell vulnerability CVE-2021-34523
- #6726 – Transfer of Cuba malware over HTTP/S
- #6728 – Email Cuba malware as a ZIP attachment
- #1338 – Remote command execution by PSExec
- #1339 – Remote command execution by PSExec
- #3829 – Run obfuscated Mimikatz on host
- #6473 – Agentless lateral movement via RDP
- #5764 – Transfer of CobaltStrike_Beacon malware over HTTP/S
- #5766 – Email CobaltStrike_Beacon malware as a ZIP attachment
- #6727 – Transfer of Cuba malware over HTTP/S
- #6729 – Email Cuba malware as a ZIP attachment
- #794 – Extract Login Information using MimiKatz
- #5983 – Exploitation of CVE-2021-26855 external Exchange server
- #5984 – Exploitation of CVE-2021-26855 internal Exchange server
What you should do now
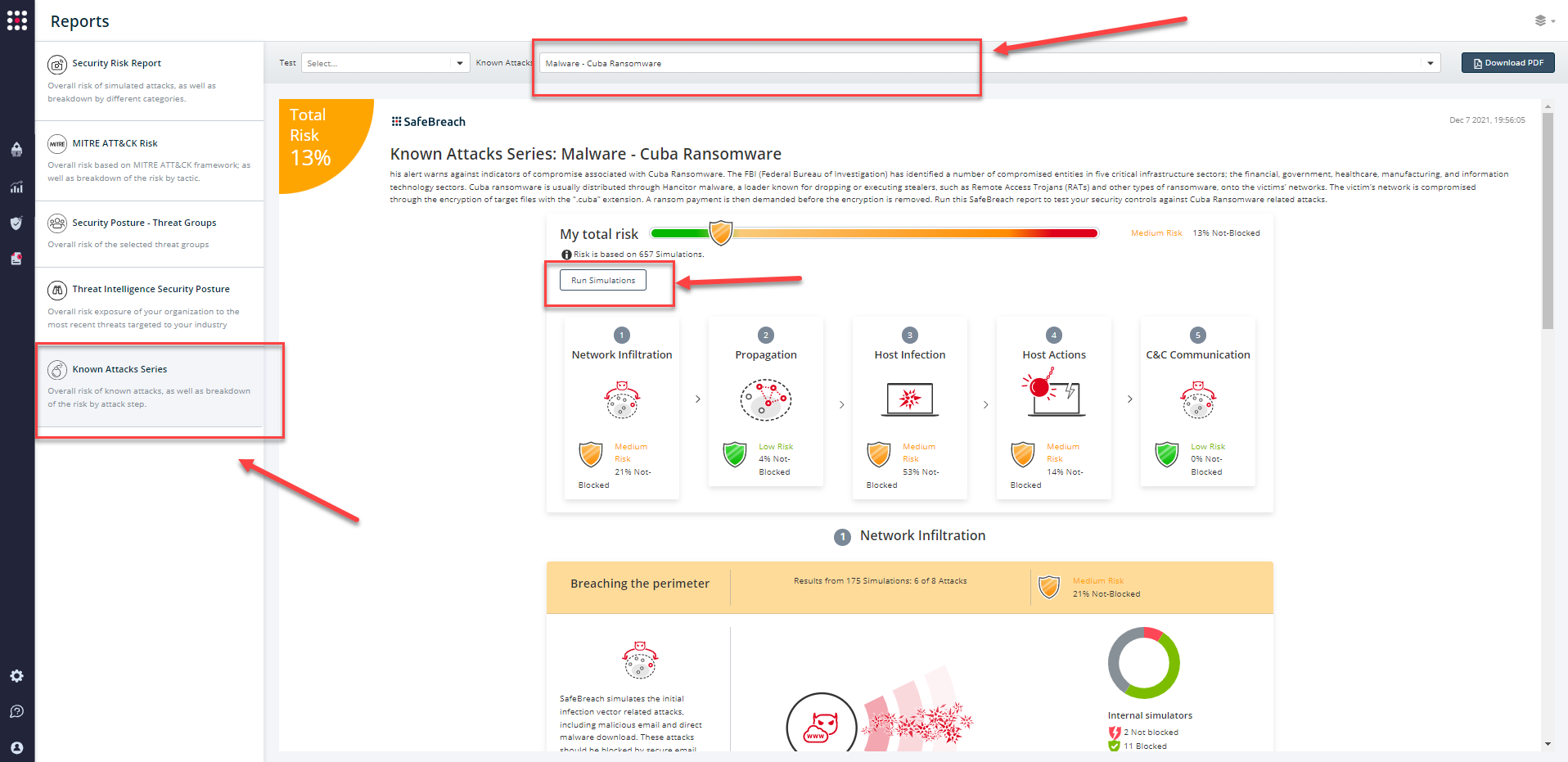
The newly updated and existing attack methods for FBI Flash Alert CU-000156-MW are already in the SafeBreach Hacker’s playbook and ready to run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this Flash alert. From the Known Attack Series report, select the Malware – Cuba Ransomware report and select Run Simulations which will run all attack methods.
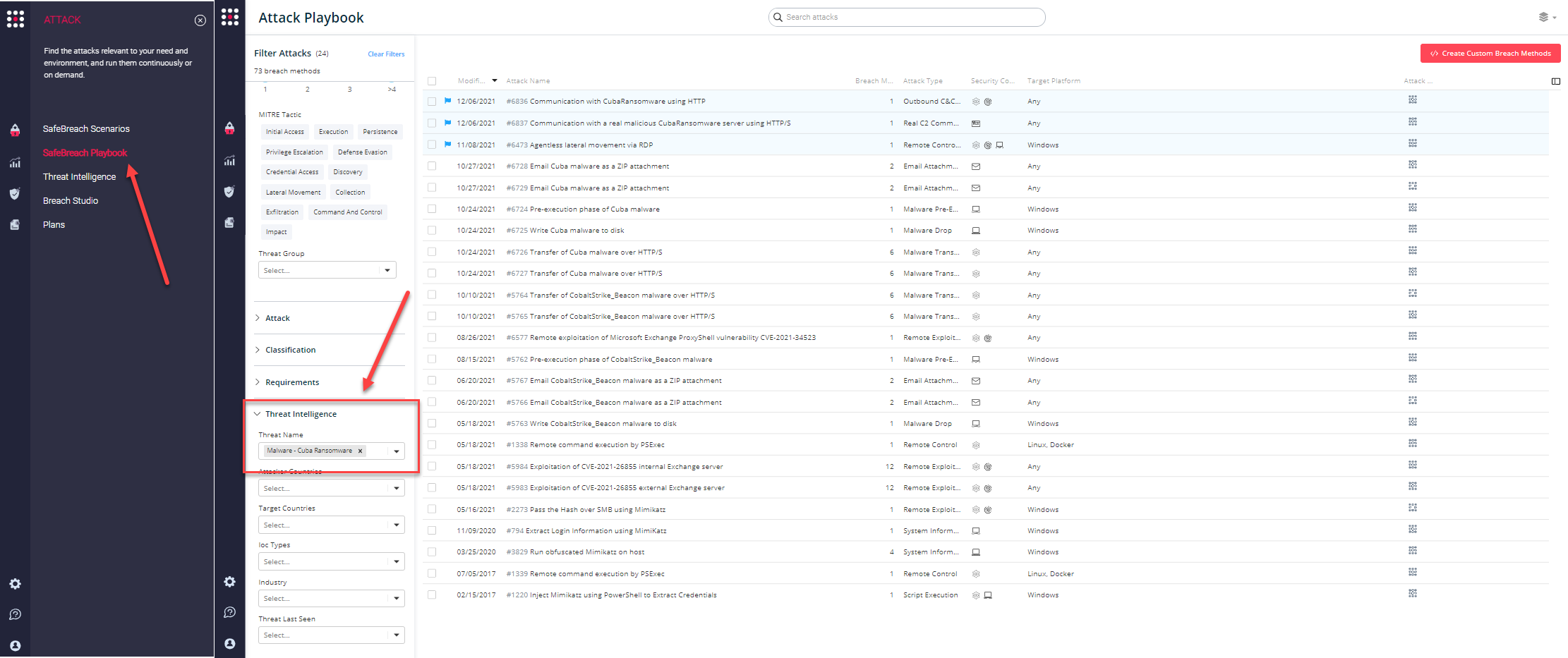
You can also select all the attacks related to FBI Flash Alert CU-000156-MW, by going to the SafeBreach Playbook and filtering by Threat Name – “Malware – Cuba Ransomware“
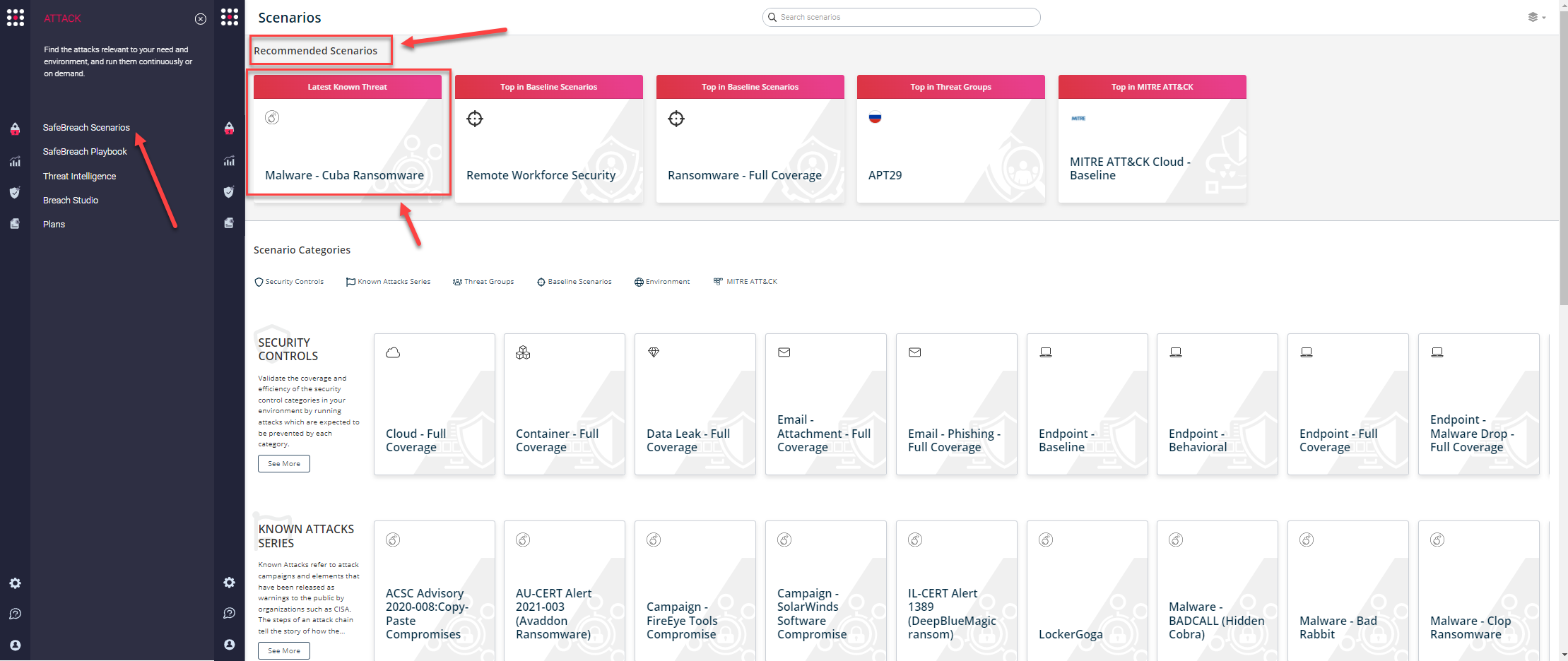
or you can go to the “SafeBreach Scenarios” page, check out the “Recommended Scenarios” and choose the Malware – Cuba Ransomware scenario from the list of available scenarios.
NOTE – The FBI also recommends the following mitigations to secure your organization against a potential Cuba Ransomware attack:
-
Require all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to have strong, unique passwords.
- Require multi-factor authentication.
- Keep all operating systems and software up to date.
- Remove unnecessary access to administrative shares, especially ADMIN$ and C$.
- Use a host-based firewall.