
Supply chain relationships are a necessity for the growth of life sciences organizations operating in today’s increasingly complex global markets. Without a technology-enabled view of the entire life sciences security infrastructure, these relationships can become weak links, exposing companies to an array of potentially catastrophic cyberattacks.
Recent attacks like the incident at CaptureRx, which is a technology and administrative services company, and the incident at MedNetworx, a medical software hosting company including the Aprima electronic health record system, are examples of how attackers can infiltrate the supply chain and gain access into the organization’s infrastructure based on third-party software components.
How Supply Chain Attacks Work
With attackers increasingly focused on supply-chain-style attacks, organizations must understand how to better protect themselves with a risk-based vulnerability management strategy.
Rather than targeting organizations directly, cybercriminals and nation-state hackers target the software makers and software service providers that work with these organizations. These attackers inject attack code into software that is then used by other organizations. They specifically target vulnerable software in development and insecure cloud configurations, or they exploit software update processes.
Following the devastating SolarWinds infiltration, federal agencies sought to help life sciences organizations and other private-sector companies better manage software supply chain risks.
The State of Supply Chains, Ransomware & Segmentation
Network segmentation is often described as the first approach to insufficient security controls. Segregating information technology (IT) assets from operational technology (OT) assets can mean the difference between a widespread catastrophic attack and a compartmentalized attack with limited damage.
Fortunately, network segmentation has proven helpful in mitigating common ransomware attacks, especially those arising from breached Internet of Things (IoT) devices, third-party vendors, and the like. Part of this has to do with the main benefits of network segmentation, which include the following:
- Segmenting networks based on functionality and sensitivity allows greater control over traffic into, and out of, these segments.
- Preventing lateral movement can prevent attackers from bypassing security controls and spreading the ransomware.
- Monitoring smaller, function-focused segments for anomalies is easier, and it helps detect intrusions faster.
- Smaller segments limit the “blast radius” of a cyberattack and assist in compartmentalizing the damage to the impacted segment.
Segmentation also helps organizations in the recovery phase. By limiting the available attack surface, the impact of any attack becomes much lower, making it easier to recover or replace lost data.
Moving Away from a Flat Network Topology
Life sciences organizations can implement network segmentation on their supply chains through a virtual local area network (VLAN), firewalls, a software-defined perimeter (SDP), or other micro-segmentation techniques. Not only that, but organizations can build even more resilient supply chains by combining these with other features such as encryption and access control.
The way organizations integrate these features is important. Experts have been saying for years to move away from a flat network approach because a strong network perimeter security is great only until an attacker breaches the perimeter. Once inside, the attacker can remain invisible for the duration of the attack. When that happens, the attacker moves laterally across the network to attack assets and eventually hold them for ransom.
Since many significant attacks to supply chains are a result of vendor mismanagement, using micro-segmentation will help organizations to implement a zero-trust architecture and leverage the principle of least privilege to protect their networks. Additionally, organizations should use automated simulation tools that can continuously validate both segmentation and security controls that effectively prevent lateral movement between network zones.
Establishing Network Borders
Protecting Devices
Organizations often forget that vulnerable devices are sitting outside the firewall, including the Internet router itself. There is usually no reason for a third-party vendor outside your network to access the devices outside your firewall. It is important to have filters on the router to prevent unauthorized users from being able to log in to the router, or to send management traffic to the router.
“For devices between the Internet router and the firewall, the easiest way to prevent access from the outside is to use a non-routed private network or computer network that uses a private address space of IP addresses (also referred to as RFC 1918 addresses). A device with private addressing can’t be reached directly from the Internet. That said, if you’re protecting a network that already has public, registered addresses on internal network equipment, it’s absolutely critical that you create access control lists (ACLs) on your Internet router preventing access from the outside to your network equipment addresses. Remember to include the firewall’s outside interface (if using public addressing on it) as well. If for some reason access to these devices is needed from an outside third-party vendor, you should permit only the specific source IP address and protocol needed.” – Kartch, (2017) Carnegie Mellon University, Best Practices for Network Border Protection
Blocking Inbound Traffic
At the Internet router, it is important to block external traffic that is sourced from an internal IP address. For example, if you have your own allocated block of addresses, you should not see external traffic sourced from one of your internal addresses. If you see traffic sourced from your own internal IP space trying to enter your network from the Internet, this suggests either someone is spoofing your addresses to try to do you harm or a routing problem has occurred. It is important to block this type of traffic at the Internet router because it is very possible that traffic allegedly sourced from your internal IP space is only subject to limited filtering once it gets to your internal network.
When it comes to network traffic, certain security tools can identify and block potential cyberattacks, such as worms spreading ransomware and intruders exploiting vulnerabilities, while permitting the flow of legitimate traffic.
Blocking Outbound Traffic
Security teams often think only to protect their private network resources from external attacks when assessing security threats. Today’s threats emanate from malware-infected endpoints, and attackers use these to collect and forward sensitive information from your network or to attack or spam other networks. Life sciences organizations are better served when network administrators are equally concerned with threats or unauthorized access associated with outbound connections.
If you don’t restrict the services that hosts in your internal networks can access, malware will inevitably find its way onto some of your hosts and may exfiltrate data to a location an attacker controls. Data exfiltration could be also unintentional, i.e., an insider might incorrectly attach sensitive information to an email message to upload it to a document-sharing service. This data exfiltration often results from configuration error: misconfigured NetBIOS, DNS, or other service traffic can leak from your trusted networks and be captured or exploited by external parties.
Without outbound traffic enforcement, logging and monitoring traffic behavior that is either authorized or prohibited makes data exfiltration more difficult to detect and mitigate.
Applications Security
Modern applications are a complex mix of proprietary and open-source code, APIs and user interfaces, application behavior, and deployment workflows. Security issues at any point in this software supply chain can expose life sciences organizations to additional risk.
On a fundamental level, supply chain security must include consideration of how to secure applications from upstream risk, and how to prevent your organization from generating downstream risk.
Open-Source Security
Open-source in today’s development landscape is everywhere. It is safe to assume that most applications are, therefore, composed of some degree of open-source risk. The abundance of open-source marks a fundamental concern when addressing supply chain security. Although open-source is no more or less risky than proprietary code, failure to adequately secure it introduces great risk to your overall organization’s security.
Since developers very likely use open-source in nearly everything they create, this translates to large portions of your applications being composed of code that you did not write. Open-source, by its very definition, comes from an uncontrolled source: developers outside of your organization. Successfully securing your supply chain means maintaining visibility into everything that applications are composed of, especially when it comes from outside your organization.
Regularly, open-source finds its way into every project, oftentimes unnoticed. The same is true for the vendors you use. Their developers both purposefully and unknowingly incorporate open-source into their projects. While this is not overly concerning, it does introduce upstream risks that find their way into your applications. Thus, it becomes your responsibility to track open-source components, licenses, vulnerabilities, and their associated risk in your supply chain.
A robust automated tool and analysis that can provide critical information will help you keep track of the open-source you’re using and how actively it is maintained, and it will provide complete visibility into the open-source dependencies your applications are built on and any associated security or licensing risk.
The Life Sciences Supply Chain
Life sciences organizations have traditionally been concerned with managing only third-party suppliers. But, due to the industry’s growing complexity, organizations now find themselves in a vast, new, risk-laden supply chain ecosystem.
This ecosystem includes the cloud services, IT providers, partners, and affiliates that define today’s modern extended enterprise. But the global life sciences supply chain is much more far-reaching and includes lab equipment suppliers, chemical suppliers, lab testing suppliers, R&D software suppliers, and more. Once a drug has been approved by the FDA, pharma companies will work with wholesalers, hospitals and clinics, government buyers, pharmacies, and many others to distribute and prescribe the drug or life-saving equipment (Exhibit 1). Therefore, it is essential to ensure that network segmentation, network borders, and applications security controls are continuously validated, and that vulnerabilities are identified and mitigated quickly, to safeguard your organization’s IT infrastructure.
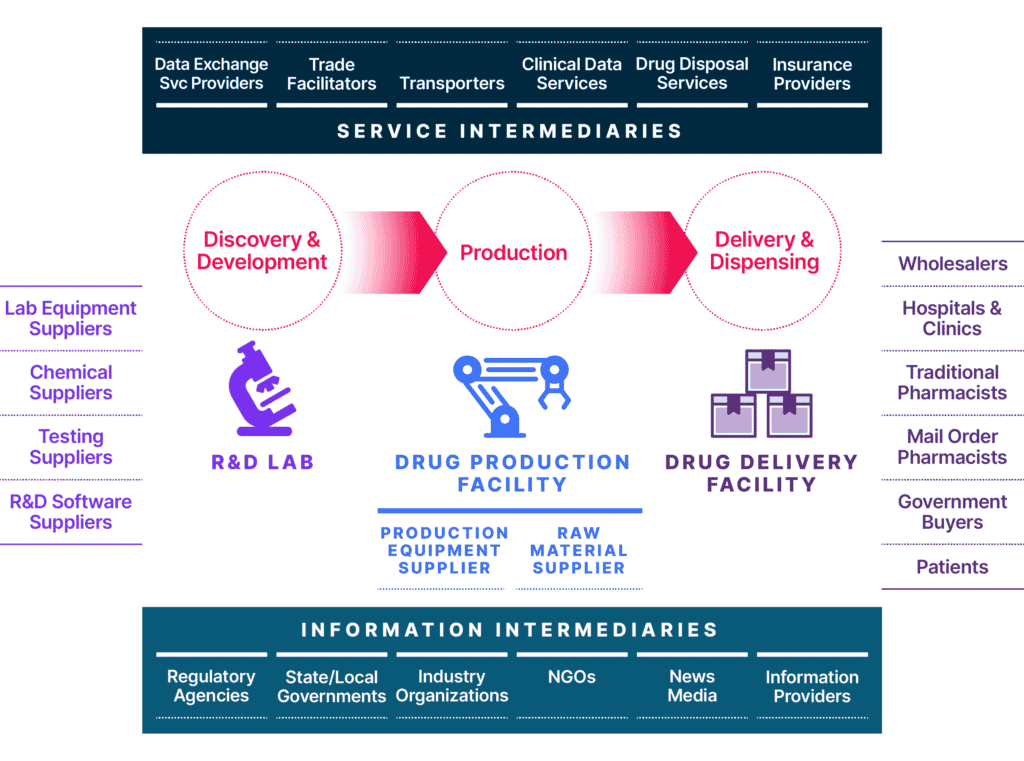
Managing Security Risk in the New Life Sciences Ecosystem
We have outlined some of the ways you can manage supply chain risk. Amid the rapid pace of both innovation and emerging threats, traditional approaches to third-party security no longer fit the new supply chain model. Like other industries, life sciences more resemble “city states,” with an extended ecosystem of manufacturer and supply chain partners trying to work together to ensure a collective and shared approach to securing data.
Although third-party risk management, monitoring, and innovation are not new challenges, gaining a precise view of your supply chain ecosystem leading into your internal security infrastructure, and identifying vulnerabilities amid the intersection of emerging risks, can seem daunting. Life sciences companies hoping to compete and thrive in the future will inevitably need to pursue a greater shared understanding of data security collaboration and security maturity.
Progress largely hinges on the critical need for technological innovation that will vastly improve both security performance and the shared use of data—via analytics, multi-functioning security platforms that provide continuous security validation and increased visibility of risk, access to real-time threat intelligence, and more. For many life sciences organizations, useful supplier and marketplace data and information exist in abundance—but insightful testing, analysis, reporting, and data sharing to generate informed decision-making on third-party risk are lacking.
As challenging as it is today, identifying risk in the supply chain ecosystem is critical to understanding potential threats to your organization.
How SafeBreach Can Help
Continuous Validation of Your Security Controls
SafeBreach offers continuous security validation powered by our breach and attack simulation (BAS) platform to help you gain visibility into your supply chain ecosystem and the associated cybersecurity risk to your organization’s infrastructure.
Attack Simulation for Network Segmentation Weaknesses
SafeBreach’s attack scenarios include lateral movement simulations that can identify locations of segmentation and access control weaknesses. Performing these types of simulations at different times during production operations and across different network segments allows life sciences organizations to gain an enterprise view of potential attack paths and to prioritize mitigation of these vulnerabilities without disruption to their business operations.
Lateral movement simulations challenge internal networks against different tactics, techniques, and procedures (TTPs) and persistent threat methodologies used by attackers to gain access, escalate privileges, and breach additional systems on a network after the initial compromise of a single system.
Security Control Validation at the Network Border
Network borders have multiple layers, and looking at the policy for network border filtering is important to permit the flow of legitimate traffic while closing security gaps in the network perimeter without impacting business operations. When it comes to network traffic, identifying and blocking potential cyberattacks is crucial.
SafeBreach offers continuous validation of the efficacy of your security controls at all layers of your network independently and at each stage of the defense process. Validating security controls and identifying gaps with firewall rules will allow you to address these proactively and mitigate the associated risk. Since networks are rarely static, with new devices and vendors being added, we recommend you validate these controls continuously.
Security Control Validation of Open-Source Applications
The SafeBreach platform offers an advanced, hybrid, multi-cloud solution to validate security controls in your cloud ecosystem to provide critical information that will help you keep track of the open-source dependencies your applications are built on, as well as the associated risk. Continuous security validation can provide this information, ensuring you have the most up-to-date and accurate picture of open-source risk.
Security Control Validation of Cloud Ecosystems
Whether it’s your native application security, runtime protection for your workloads, critical application dependencies for container security, or API governance and identity management in the control plane, SafeBreach provides continuous security validation for the full cloud kill chain in your cloud ecosystem.
We understand the risk associated with applications security, and we test your readiness in the cloud with real adversary behaviors to train your cloud immune system.
Take Proactive Measures
Leaders in life sciences need to adapt to the new reality of cyber threats and supply chain vulnerabilities. The current threat landscape demands a different mindset for identifying cybersecurity risks for third-party security controls and new practices to ensure a more secure internal environment. Life sciences organizations today view third-party risk management as a strategic priority for future competitiveness and success in a dramatically evolving world where cyberattacks and risk are untamed. But, as the digital world rapidly changes, that journey to manage risk must start now. Digital transformation and continued innovation are happening, and remaining proactive is a necessity. Advancement that manages risk in the new era will be filled with opportunities for the life sciences industry to enable new ways of thinking about third-party security and supplier relationships—while continuing to look for new ways to increase prospects for success.
Want to learn more about SafeBreach, the leader in continuous security validation and breach and attack simulation? Request a demo with one of our cybersecurity experts today.