
Cybersecurity is a sector in flux. Every year, it changes almost beyond recognition, and 2022 was no different. Chief information security officers (CISOs) and their security teams were forced to deal with the unprecedented increase in cyberattack frequency, severity, and impact that created a race against time to validate security controls, remediate misconfigurations, and patch or modify programs to improve security and performance. To win that race in 2023—or at the very least keep up—it’s imperative that organizations have the necessary information, technology, and resources to proactively prepare and defend themselves.
As a leader in the continuous security validation (CSV) market, the SafeBreach research team is uniquely positioned to provide this, as our research team has unparalleled insight into the minds’ of cybercriminals. They spend their days monitoring the hacker underground, sourcing intelligence feeds, and conducting original research. What’s more, they are constantly adding to the SafeBreach Hacker’s Playbook, which is the most comprehensive collection of attacks in the world with over 30,000 breach methods.
With this in mind, SafeBreach has put together the very first Hacker’s Yearbook, a comprehensive resource that analyzes and presents a “hacker’s view” of the last year: what cyberattacks of 2022 were most impactful and how did they work? What key takeaways can help organizations better defend against them? And, most importantly, what can each of us do moving forward to make this a more fair fight in 2023?
The first installment of the annual Hacker’s Yearbook provides:
- Primary trends and concerns from the last year, so organizations can stay up to date with the evolution of the security industry as a whole, including how:
- Ransomware and supply chain attacks rose
- Nation-state threat groups got more sophisticated
- Governments prioritized cybersecurity as a critical threat
- Cyber insurance grew more complicated and expensive
- An overview of more than 20 of the most severe threats of 2022 that organizations can use to ensure they are protected, including:
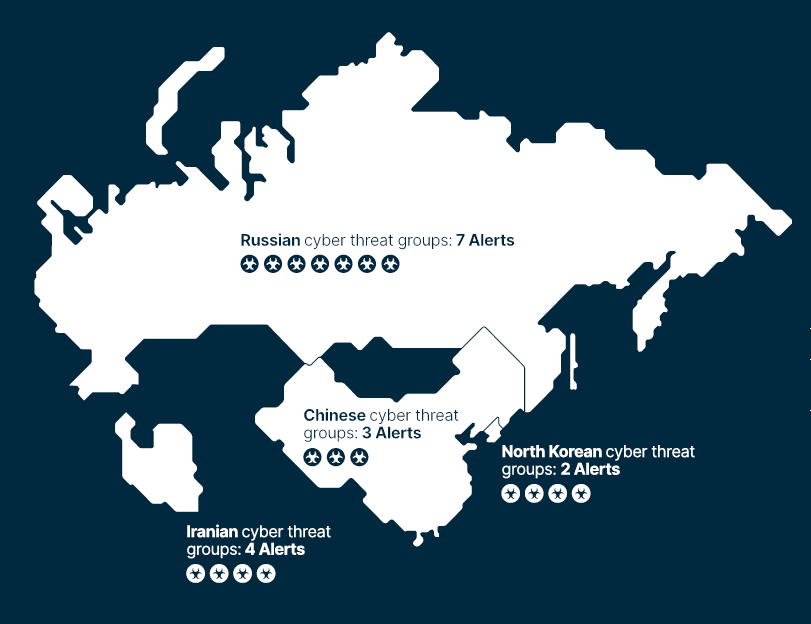
- Nation-state attacks by Russia, Iran, and North Korea
- Some of the most destructive malware and ransomware variants
- Recommendations about where organizations can focus their security efforts going forward, so they are better prepared to face the new challenges of 2023, including how to:
- Prioritize patching
- Invest in detection engineering
- Implement a continuous security validation tool
Alongside this, the Hacker’s Yearbook provides an overview of new vulnerabilities identified by our own original threat research throughout the last year, including:
- Aikido Wiper: A Next-Generation Wiper
- OopSec: The Bad, the Worst, and the Ugly of APT’s Operations Security
- The CoW (Container on Windows) Who Escaped the Silo – Isolations Are Meant to be Broken
- New, Fully Undetectable Powershell Backdoor
- CodeRAT: A New Remote Access Trojan
- Potential Generic Bypass in the Palo Alto Cortex XDR Anti-Ransomware Module
- Google VirusTotal Hacking: The Perfect Crime
The SafeBreach Hacker’s Yearbook is an invaluable resource for anyone looking to peek behind the curtain into the underworld of cyberattacks and the advanced persistent threat (APT) groups behind them. They say that those who ignore history are doomed to repeat it—we want to ensure that doesn’t happen. Fighting cyber attacks and malicious actors in 2023 requires a deep understanding of the minds, mistakes, and motivations of 2022’s worst offenders. The Hacker’s Yearbook provides just that.
Ready to see the Hacker’s Yearbook for yourself? Access a full copy here:

Interested to learn what continuous security validation is all about? Connect with a SafeBreach cybersecurity expert or request a demo of our advanced breach and attack simulation (BAS) platform today.

