Of life sciences cyber attacks seek access to IP
%
Of organizations were hit by supply chain attacks
%
The average cost of a life sciences data breach incident
$
M

Experience the Power of a Truly Proactive Defense
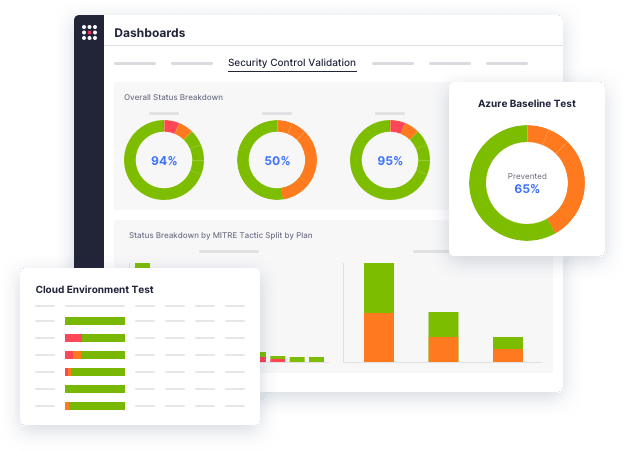
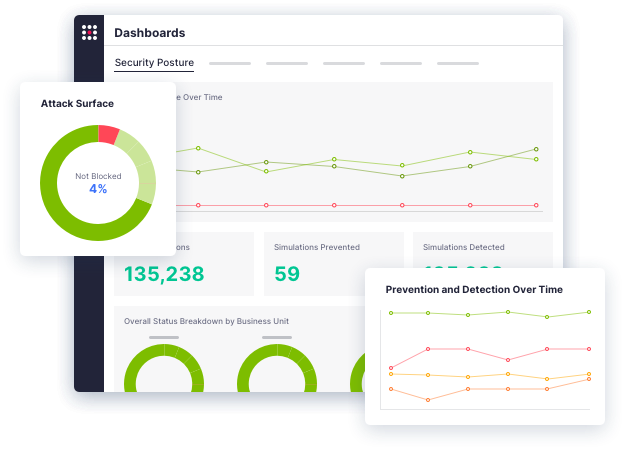
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.

Protect Your Most Valuable Assets
Continuously validate your security controls to safeguard valuable patient records, clinical trial results, and intellectual property.
Minimize Supply Chain Security Exposure
Gain greater visibility into your supply chain ecosystem to identify potential attack paths, prioritize vulnerabilities, and take mitigating action quickly.


Go Beyond Compliance Requirements
Instead of checking a box and finding security gaps later, leverage continuous validation to verify compliance and security within your environment at the same time.
Validate People, Processes & Tools
Provide real-world scenario training and test the efficacy of the tools you have in place to ensure everything—and everyone—is ready when a real attack happens.

Are you ready for the ultimate test?
The SafeBreach breach and attack simulation platform puts your security controls to the test, so you can put threats to rest.
Rediscover your defenses with a powerful BAS platform.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Execute lateral movement, infiltration, and exfiltration simulations to test and secure segmentation and access control weaknesses to reduce your attack surface.
Proactively identify firewall rules gaps and mitigate the associated risk, while permitting legitimate inbound/outbound traffic.
Validate cloud ecosystem security controls to track the open-source dependencies of your applications and identify any associated business risk.