Patient records compromised in 2021 alone
M+
Of healthcare orgs affected by ransomware globally
%
Spent on average to remediate a healthcare ransomware incident
$
M

Experience the Power of a Truly Proactive Defense
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.

Confidently Support Digital Transformation
Ensure your team can securely meet the demand for “anywhere, anytime” healthcare to grow your business and better serve patients.
Go Beyond Compliance Requirements
Gain greater visibility into security control performance to develop a holistic approach to healthcare cybersecurity that addresses compliance and the threat landscape.


Stay Ahead of the Headlines
Leverage the most comprehensive attack coverage to test your defenses, identify vulnerabilities, and stay up-to-date on malicious actors targeting the healthcare industry.
Hold Security Vendors Accountable
Test the efficacy of the tools you have in place to validate vendor commitments and identify opportunities to replace or consolidate.

Are you ready for the ultimate test?
The SafeBreach breach and attack simulation platform puts your security controls to the test, so you can put threats to rest.
Rediscover your defenses with a powerful BAS platform.
Watch our demo.
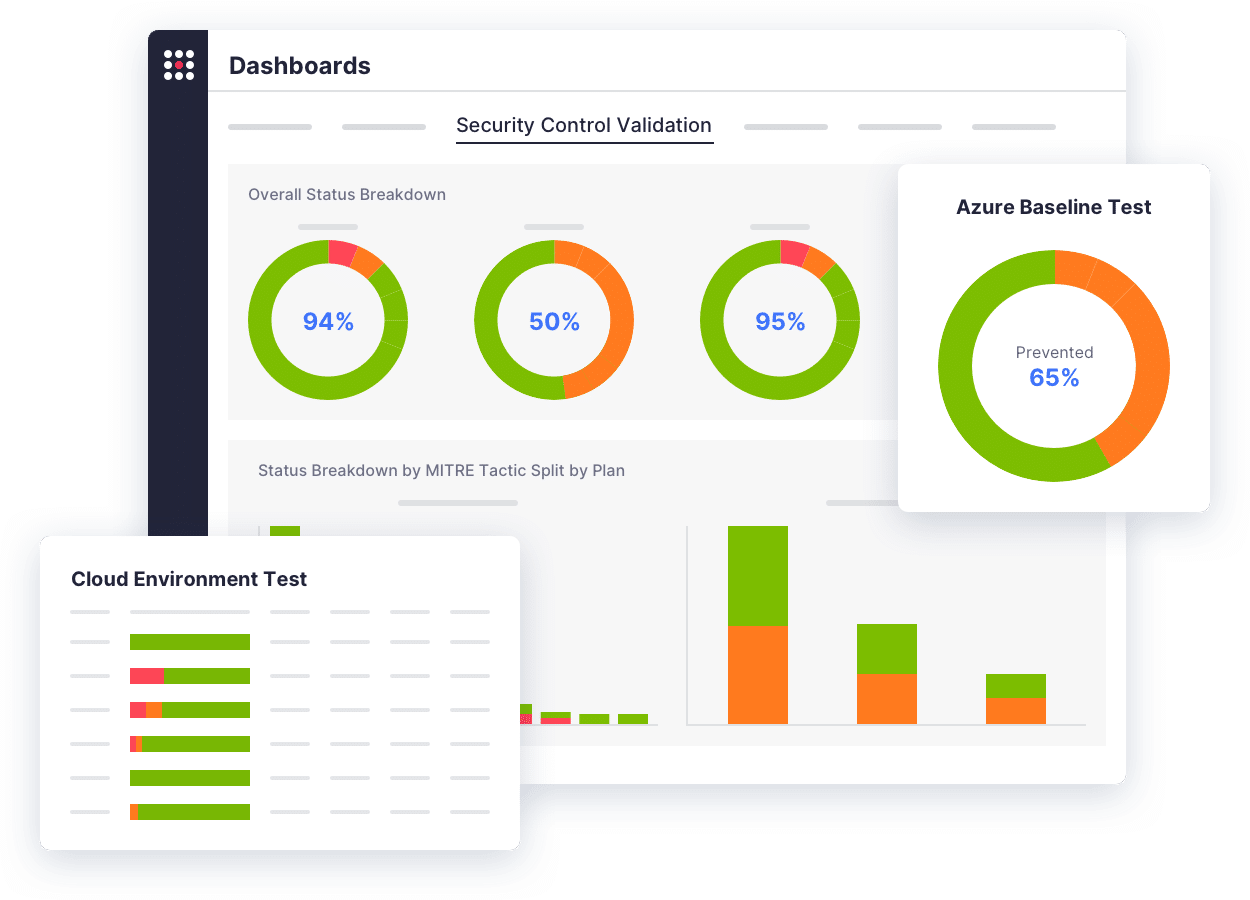
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Execute advanced, multi-stage attack simulations that include sending and opening emails, detonating payloads, and triggering simulator alarms to see how your system responds at each step.
Validate security controls in cloud ecosystems to track risk associated with application workloads before they are deployed to the cloud.
Mitigate network vulnerabilities by validating security controls associated with policy-driven network configuration and edge access to enterprise data or cloud services.
Simulate phishing attacks that malicious social engineers use to validate security control efficacy and identify potential vulnerabilities and attack pathways.