More likely to be targeted by cyberattacks than other sectors
x
Of FSIs faced a cyberattack in the past 12 months
%
Increase in ransomware attacks on financial institutions in 2021
%

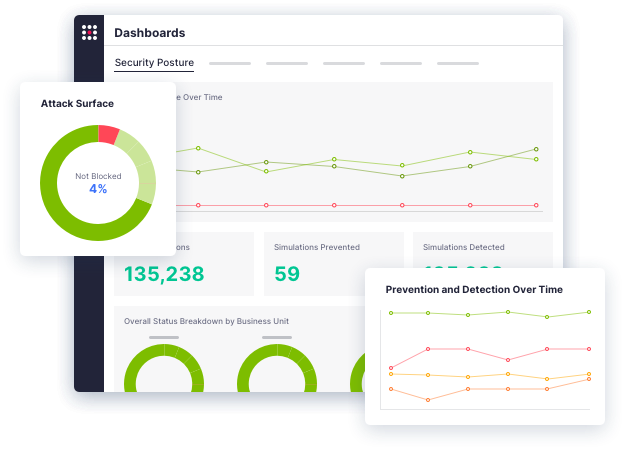
Experience the Power of a Truly Proactive Defense
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.

Confidently Support Digital Transformation
Ensure your team can securely meet the demand for new digital products and services to grow your business and better serve customers.
Go Beyond Compliance Requirements
Instead of checking a box and finding security gaps later, leverage continuous validation to verify compliance and security witihin your environment at the same time.


Minimize Third-Party Security Exposure
Before working with third parties or making an acquisition, precisely assess their cybersecurity posture to understand the potential risks and identify areas for improvement.
Grow Confidence with Stakeholders
Share automated reporting with key stakeholders to clearly communicate risk within the organization and ensure security investments are prioritized.

Are you ready for the ultimate test?
The SafeBreach breach and attack simulation platform puts your security controls to the test, so you can put threats to rest.
Rediscover your defenses with a powerful BAS platform.
Watch our demo.
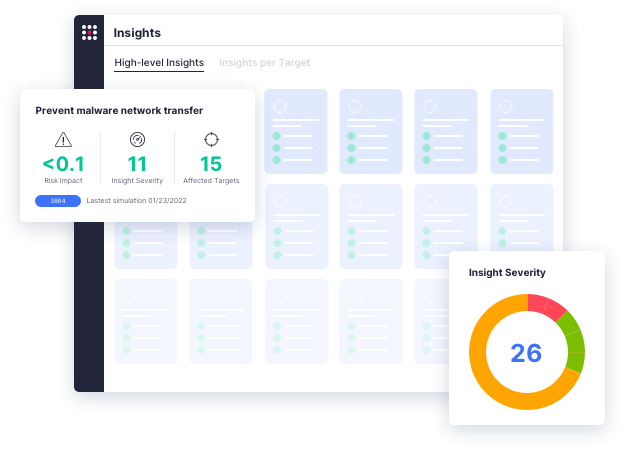
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
Watch our demo.
See how SafeBreach helps you justify your security investments, strengthen your defenses, and drive risk down with the industry’s most robust security control validation.
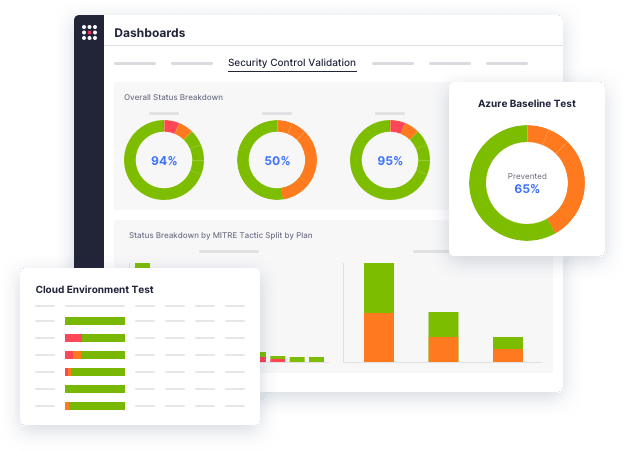
Validate security controls by running simulation techniques used by threat actors with finance-specific MITRE ATT&CK TTP attack scenarios.
Automate the execution of multi-stage attacks across the entire cloud stack, including end-user devices, networks, cloud services, and applications.
Employ known IOCs and behavioral techniques to replicate attempts to access metadata, extract configuration information, exfiltrate data, and execute server-side request forgery.
Extend attack simulations to container-based infrastructures to test the data plane, network, and API against a range of tactics, including process injection and lateral movement.