Although it is a relatively new discipline, the principles and goals behind detection engineering should be very familiar to cybersecurity teams: fine-tuning security technologies to better detect malicious activity. One of the most effective ways to validate and enhance detection engineering capabilities is through breach and attack simulation (BAS).
Below, we’ll dive into the details about what detection engineering is and how BAS can maximize its impact.

Experience the Power of a Truly Proactive Defense
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.
What Is Detection Engineering?
Detection engineering is a cyclical process that helps to create, test, and maintain a security program’s ability to identify and respond to evolving threat actor tactics, techniques, and procedures (TTPs).
The key elements of detection engineering include:
- Threat detection: Implementing tools, processes, and procedures to identify unusual or suspicious behavior that may indicate a breach or the presence of concealed threats within computer networks and systems.
- Alert generation: Creating actionable alerts based on detected threats to prompt immediate response from concerned teams.
- Response actions: Implementing workflows and processes to mitigate identified threats and ensure that mitigation has not created additional security gaps in the network.
Detection engineering has a cyclical life cycle that is comparable to that of the software development process, but specifically focused on developing detections:
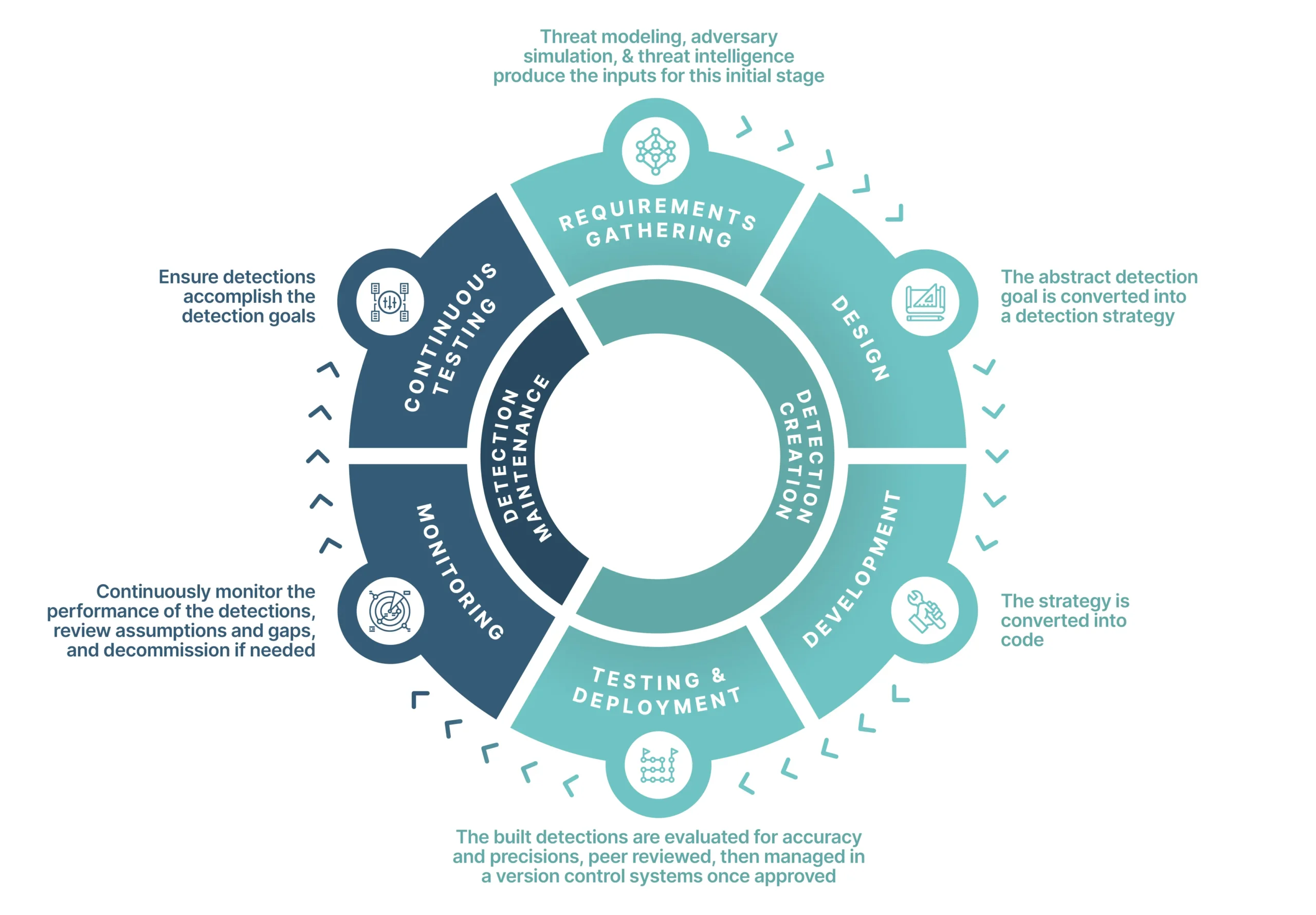
General Detection Engineering Lifecycle
During this lifecycle, detection engineers work closely with other cybersecurity experts to assess and respond to identified threats found in earlier stages.
Together, these professionals can fine-tune detection algorithms and rules, and continuously improve their company’s security posture. Specifically, they enhance the inputs and alerts coming from monitoring tools such as:
- Intrusion detection systems (IDS)
- Intrusion prevention systems (IPS)
- Security information and event management (SIEM) systems
These tools are used to sift through, prioritize, and flag system logs, network traffic, and other data sources for indications of malware, unauthorized data transfer, and other vulnerabilities.
Why Is Detection Engineering Important?
The ultimate goal of detection engineering is to reduce cyber risk and exposure to known threats.
As adversaries employ more sophisticated TTPs—such as living-off-the-land (LOTL) and fileless attacks—they have improved their ability to evade security controls like endpoint detection and response (EDR) solutions and endpoint controls. Detection engineering empowers security teams to implement additional ways to more proactively identify unusual or suspicious behavior and take action before it can cause harm.
At the same time, detection engineering can be a key enabler in helping security teams meet compliance requirements and build customer trust.
Improving Detection Engineering Processes with BAS
Leading enterprise organizations are increasingly turning to the complementary capabilities of BAS to help them optimize and enhance their existing detection engineering programs. BAS provides a more comprehensive, automated, and robust way for organizations to continuously identify weaknesses and enhance threat detection capabilities.
BAS is a highly automated solution that safely runs real-world attack simulations against an organization’s production applications and infrastructure to validate the effectiveness of its security controls.
When integrated into detection engineering processes, BAS can:
- Reduce manual effort: BAS enables detection engineers to automatically and continuously validate detections and alerts for thousands of known attack methods. Additionally, the ability to create custom detections more efficiently allows teams to focus more resources on remediation or other high-value initiatives.
- Enhance detection logic through integration: By aggregating attack performance outcomes through native integrations with other systems, BAS platforms can provide a comprehensive view of security performance that aids in refining detection logic and fortifying incident response strategies.
- Provide end-to-end visibility: BAS simulations test the entire alert lifecycle, ensuring that all components—from detection and alerting to ticketing and response—are functioning correctly and ready to respond when a security incident occurs.
- Enable consistent testing across environments: BAS allows for continuous testing in various environments, locations, and zones, ensuring consistent detection capabilities across an organization.
Resources for Further Reading
The Business Benefits of Detection Engineering
Detection engineering, complemented with a strong BAS program, offers several key benefits to businesses, including:
- Risk reduction: Proactively identify and mitigate threats to minimize the risk of data breaches and cyberattacks.
- Cost efficiency: Identify malicious activity and alert remediation teams quickly to reduce costs associated with remediation and recovery efforts or fines for non-compliance with regulatory requirements.
- Operational efficiency: Streamline security operations by automating less complex manual processes, allowing teams to focus on analyzing and mitigating the highest priority threats or at-risk systems.
- Customer trust: Build and maintain stakeholder and customer trust by demonstrating a dedication to a strong organizational security posture.
- Secure partnerships: Ensure a more secure and compliant partnership ecosystem by monitoring risks related to third-party vendors.

Learn more about this growing cybersecurity discipline and how BAS can help establish or optimize a detection engineering program.
Fortify Your Defense with SafeBreach’s BAS Platform
SafeBreach’s BAS platform allows enterprises to validate the efficacy and resilience of their security ecosystem through continuous simulation of real attack scenarios. With SafeBreach, your security team will enjoy:
- Access to the Hacker’s Playbook: SafeBreach’s BAS platform gives organizations access to the most comprehensive playbook in the industry, which includes more than 30,000 real-world attack methods. This vast library of attacks enables comprehensive testing and validation of security controls.
- 24-hour service-level agreement: We maintain a 24-hour service-level agreement to incorporate new attacks into our platform based on US-CERT and FBI alerts. This ensures our customers’ security postures remain robust against the latest threats.
- Advanced attack creation: SafeBreach enables users to design and execute sophisticated custom attack simulations that run automatically and continuously to test the limits of your security infrastructure and ensure custom detections are triggering alerts appropriately.
- Entire alert lifecycle validation: Attack simulations test every stage of the alert process—from detection to response—to ensure seamless operation and rapid response times.
- Continuous health checks: Utilize the SafeBreach platform to monitor the health and performance of your security infrastructure to identify and address potential vulnerabilities promptly. Monitor performance over time to evaluate the impact of different changes and investments while ensuring that your security measures are always up-to-date and effective.
Related Blog Posts
How Enterprises Utilize SafeBreach to Optimize Detection Engineering
When a major financial services institution (FSI) experienced challenges with its detection engineering program, it turned to SafeBreach. Notifications about potential malicious activity weren’t being delivered to their incident responders for hours at a time, significantly delaying response times and creating critical gaps that malicious actors could exploit.
To tackle this challenge, they used the SafeBreach platform to create scenarios that mimicked realistic attack techniques, including both known attacks and customized simulations. Next, they integrated both their ticketing system and security information and event management (SIEM) system with SafeBreach to establish a closed loop, where simulated attacks triggered notifications that traversed the typical alert pipeline to reach their incident responders, as they would in a real-world scenario.
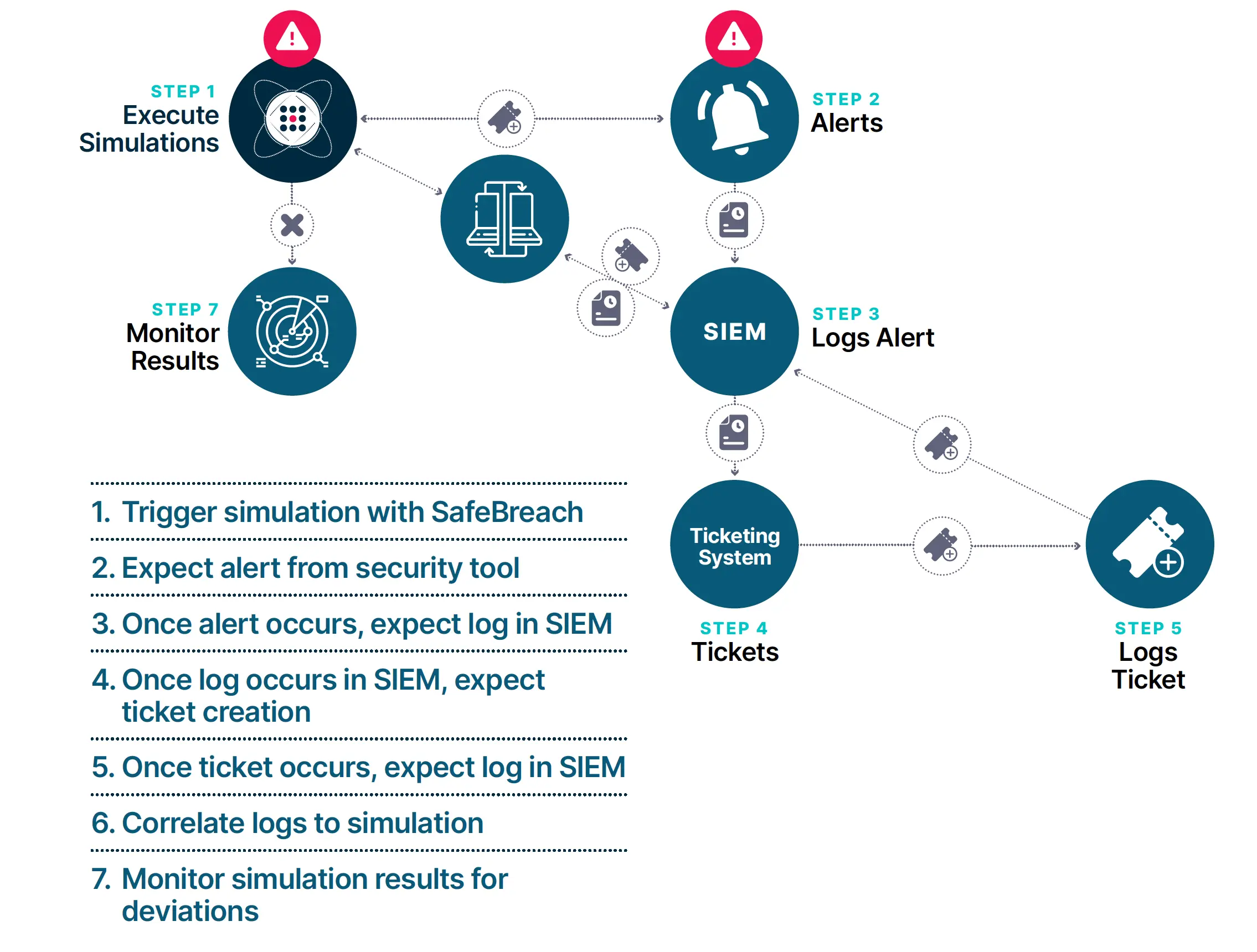
As a result, they identified a number of issues within their alert pipeline and incident response workflows that they were able to immediately fix. They also established a process to run these health checks on their detection engineer processes regularly to:
- Validate the efficacy of their security tools and detection mechanisms using customized attack scenarios that accurately simulated real-world threats.
- Proactively identify alerting issues and discrepancies early, before they became critical.
- Establish and maintain confidence in their ability to detect and respond to threats effectively.
- Create end-to-end visibility with a closed-loop approach that triggered alerts, simulated response actions, and validated outcomes.
Secure Your IT and OT Ecosystem with SafeBreach
SafeBreach is a leader in the BAS market, offering unparalleled attack simulation capabilities to complement your detection engineering program:
- Comprehensive MITRE ATT&CK coverage: We offer the widest coverage of any BAS platform.
- Enterprise-ready platform: Our platform is scalable and easy to deploy, integrating seamlessly with existing controls and business systems.
- Award-winning customer success team: Our team supports the deployment and management of your BAS program.