Know whether your cloud provider is adequately securing your environment.
As more areas of the business move to the cloud, organizations are exposed to new security challenges that increase exposure and risk. With attack scenarios for Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), multi-cloud, and cloud-hybrid environments, SafeBreach can help test your cloud control and data planes to ensure the security of your cloud operations.
Test cloud-native environments against advanced threats.
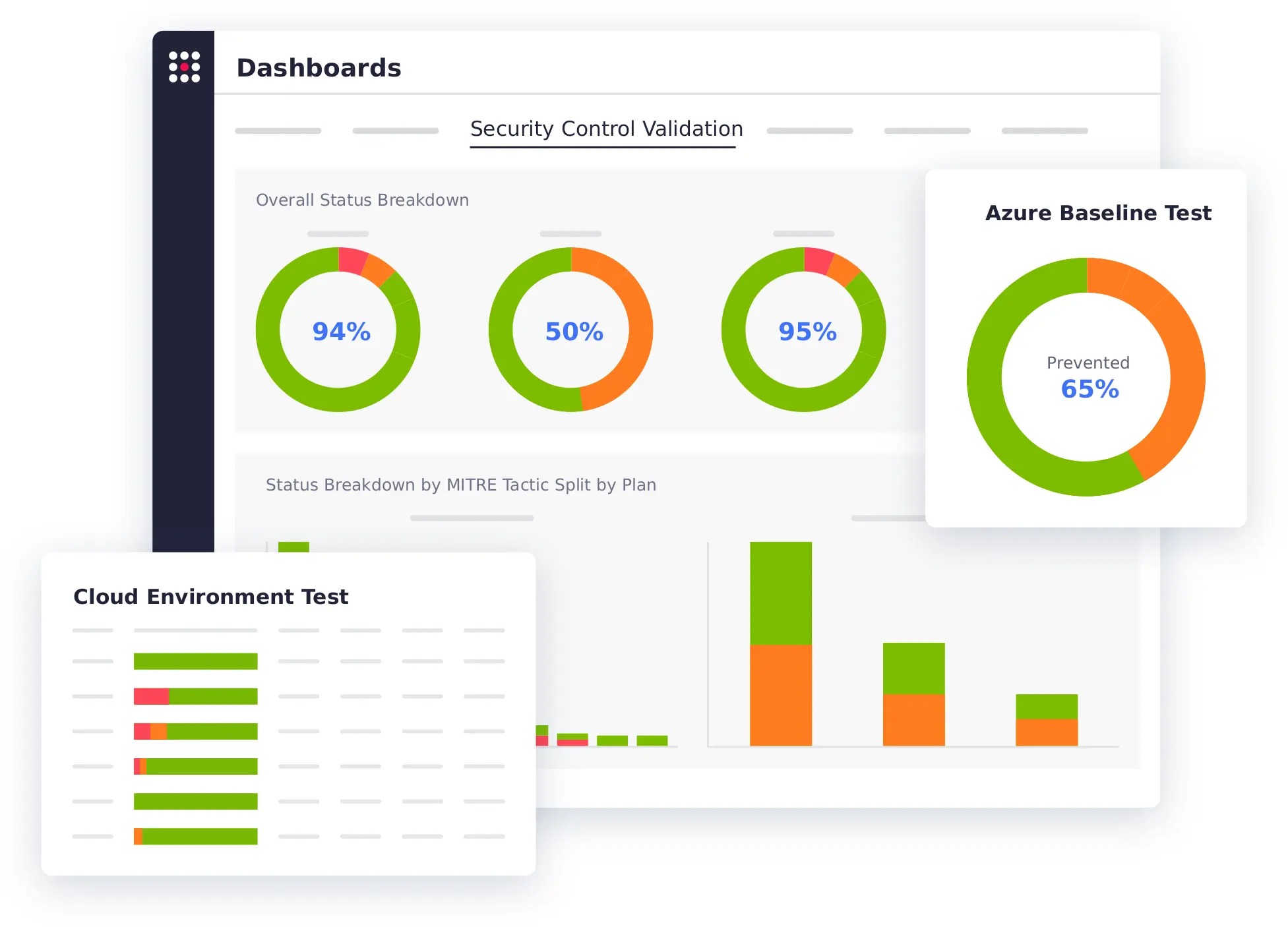
Automate the execution of multi-stage attacks across the entire cloud stack, including end-user devices, networks, cloud services, and applications. Employ known IOCs and threat-actor-behavioral techniques to replicate attempts to access metadata, extract configuration information, exfiltrate data, and execute server-side request forgery. Extend attack simulations to container-based infrastructures running Docker to test the data plane, network, and API against a range of tactics, including process injection, rogue applications, system changes, and lateral movement from container to container.
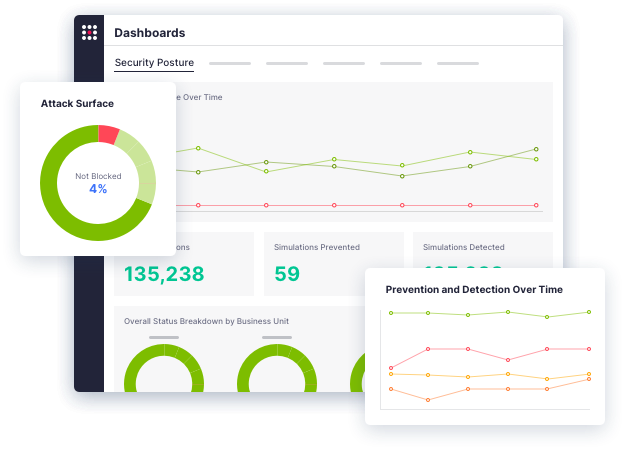
Analyze and visualize test results to quickly identify and prioritize security gaps and use remediation insights to facilitate and automate resolution. Customize dashboards to communicate status and risk level to key stakeholders. Additionally, DevOps teams can leverage contextual insights from simulated attacks to continuously assess the security and integrity of web applications at each stage of development, allowing them to identify and address vulnerabilities before releasing an application into production.

Experience the Power of a Truly Proactive Defense
The SafeBreach breach and attack simulation (BAS) platform puts your defenses toe-to-toe against over 30,000 attack methods to provide unparalleled visibility into your security posture. See why some of the largest enterprises in the world trust SafeBreach to help them proactively identify and remediate vulnerabilities.