On February 7th, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) issued an urgent advisory to warn about the possibility of People’s Republic of China (PRC)-affiliated threat actors seeking to execute disruptive or destructive attacks by positioning themselves on IT networks belonging to critical infrastructure entities. Detailed information about these activities and the associated indicators of compromise (IOCs) along with the various tactics, techniques, and procedures (TTPs) is listed in PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure.

Technical Details
This advisory is based on incident response activities conducted by CISA, NSA, FBI and their partners at critical infrastructure organizations compromised by the state-sponsored threat group Volt Typhoon (also known as Vanguard Panda, BRONZE SILHOUETTE, Dev-0391, UNC3236, Voltzite, and Insidious Taurus). The assessment has revealed that Volt Typhoon has successfully compromised IT networks in several critical infrastructure entities, primarily in the Communications, Energy, Transportation, and Water and Wastewater systems sectors across the continental and non-continental United States.
Based on the details available, Volt Typhoon’s assessed behavior indicates that their objectives were not focused on spying or gathering intelligence. Instead, the agencies believe that Volt Typhoon threat actors were essentially preparing to position themselves inside IT networks where they could inflict maximum damage on U.S. critical infrastructure in the event of hostilities between the PRC and the United States. The advisory has highlighted Volt Typhoon’s use of living off the land (LOTL) techniques when targeting critical infrastructure entities, allowing them to maintain persistence in IT networks without being detected. The agencies believe that in some cases, these threat actors had been maintaining access to IT networks for at least 5 years. Volt Typhoon actors are known to conduct extensive pre-exploitation reconnaissance to learn about their target organization and its environment. They leverage gathered information to customize their TTPs for each target and then continue maintaining their presence on victim networks to further understand their network behavior over time.
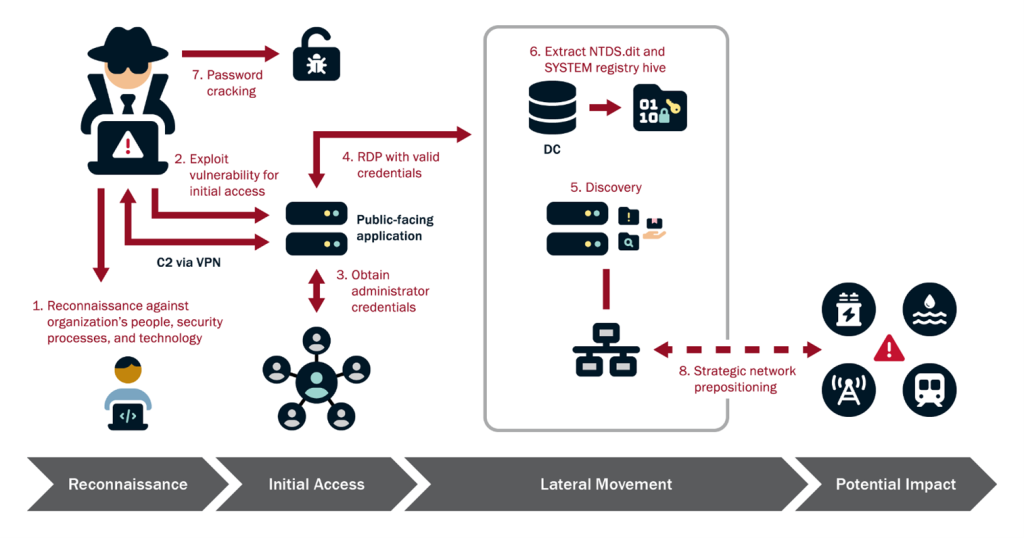
While TTPs may have been customized for each target, the agencies also noticed a similar pattern of behavior across all the identified intrusions. Volt Typhoon’s typical attack activity can be summarized below (also seen in the image).
- Conduct extensive pre-compromise reconnaissance to learn about the target organization’s network architecture and operational protocols.
- Gain initial access to the IT network by exploiting known or zero-day vulnerabilities in public-facing network appliances (including those from Fortinet, Ivanti, NETGEAR, Cisco, and Citrix).
- Attempt to obtain administrator credentials within the network by exploiting privilege escalation vulnerabilities in the operating system or network services. The use of Mimikatz and Impacket was also observed to harvest credentials and manipulate network protocols.
- Leverage harvested credentials to move laterally to the domain controller (DC) and other devices via remote access services such as Remote Desktop Protocol (RDP).
- Conduct discovery in the victim’s network, leveraging LOTL binaries for stealth.
- Achieve full domain compromise by extracting the Active Directory (AD) database (NTDS.dit) from the domain controller. The NTDS.dit file contains AD data including user account passwords (hashed) and other sensitive information.
- Use offline password-cracking techniques to decipher hashes and gain elevated access to perform further infiltration and network manipulation.
- Use elevated credentials to perform further network discovery to gain access to organizational OT assets. This access can allow them to manipulate heating, ventilation, and air conditioning (HVAC) systems in server rooms or disrupt critical energy and water controls, leading to significant infrastructure failures.
Important Note for SafeBreach Customers – Coverage for AA24-038A (Volt Typhoon)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers were already protected against several of the IOC-based attacks identified in the advisory. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
NEW IOC-Based Attacks Related to CERT Alert
- #9508 – Write ScanLine (7ff9d0) hacktool to disk
- #9509 – Pre-execution phase of ScanLine (7ff9d0) hacktool (Windows)
- #9510 – Transfer of ScanLine (7ff9d0) hacktool over HTTP/S
- #9511 – Transfer of ScanLine (7ff9d0) hacktool over HTTP/S
- #9512 – Email ScanLine (7ff9d0) hacktool as a compressed attachment
- #9513 – Email ScanLine (7ff9d0) hacktool as a compressed attachment
Existing IOC-based Attacks Mapped to the CERT Alert
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #7223 – NTDS.dit dump using ntdsutil
- #1527 – Remote command execution by WMIC (information gathering)
- #1693 – Collect Windows system data using CMD
- #2153 – Rundll32
- #2174 – Extract users and groups using net.exe (Windows)
- #2188 – Extract Process List using Windows Commands
- #2194 – Extract Credentials from the Registry using System Commands
- #2217 – Discover the system time using net time command (Windows)
- #2245 – Indicator Removal on Host (Windows)
- #2266 – Collect Google Chrome Bookmarks
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #2273 – Pass the Hash over SMB using Mimikatz
- #3829 – Run obfuscated Mimikatz on host
- #6411 – Screen Capture (Windows)
- #6473 – Agentless lateral movement via RDP
- #6580 – Discover domain groups using LDAP method
- #6807 – Extract credentials from ntds.dit file using volume shadow copy
- #6909 – RDP Connection Between 2 Simulators
- #6910 – RDP Tunneling
- #7554 – Clear Windows Event Logs
- #794 – Extract Login Information using MimiKatz
- #8004 – Capture Screen using Powershell
- #8016 – Application Window Discovery (Windows)
- #8020 – Port scanning of local subnet network
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
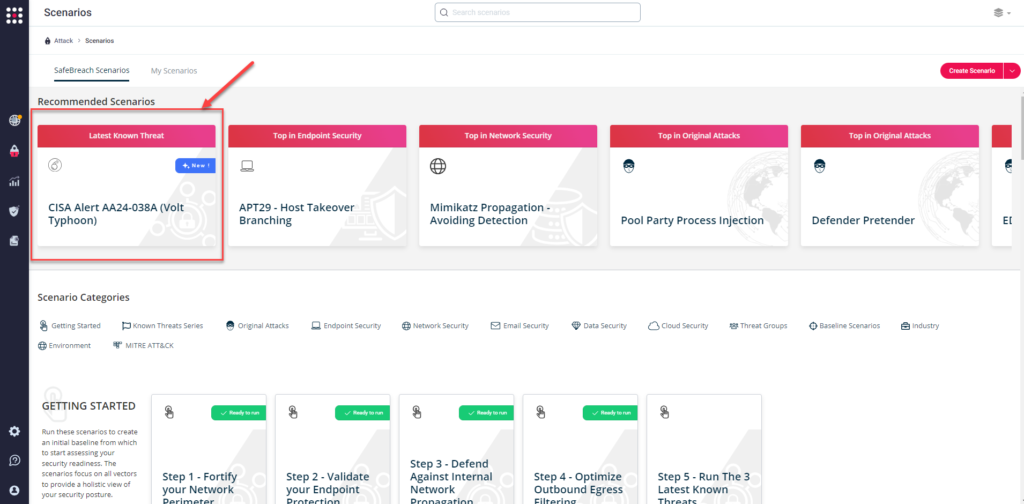
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-038A (Volt Typhoon) scenario from the list of available scenarios.
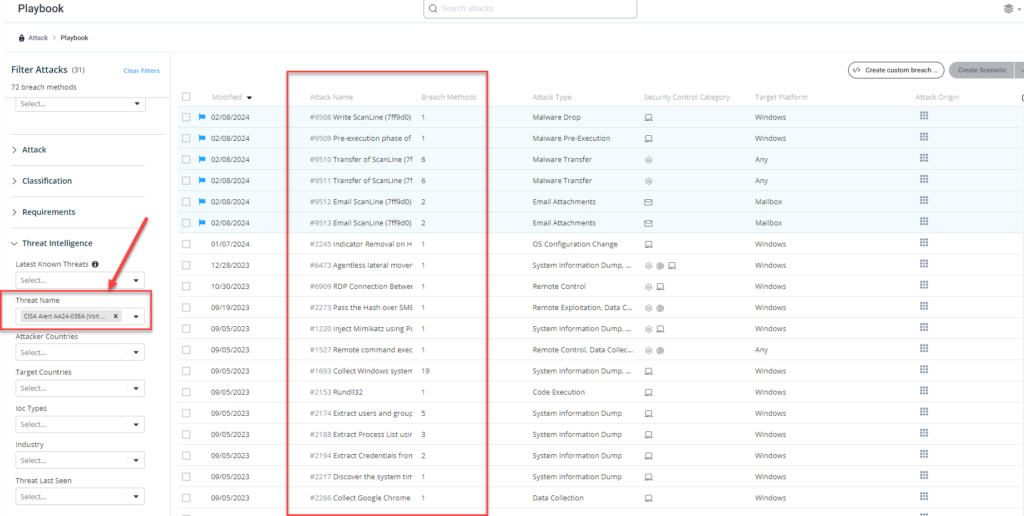
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA24-038A (Volt Typhoon). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
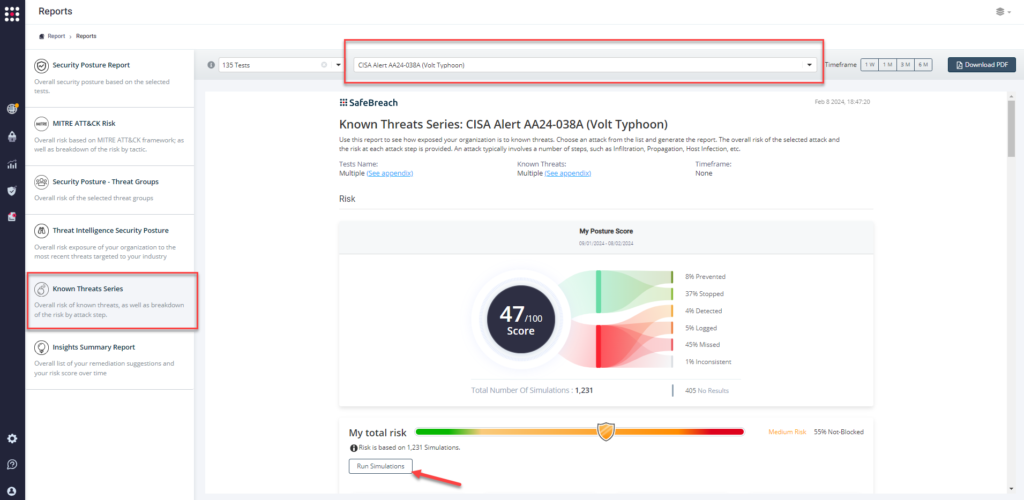
Method 3 – From the Known Attack Series report, select the AA24-038A (Volt Typhoon) report and select Run Simulations which will run all attack methods.
NOTE – FBI, NSA, and CISA recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Apply living off the land detection best practices.
- Routinely review application, security, and system event logs, focusing on Windows Extensible Storage Engine Technology (ESENT) Application logs.
- Monitor and review OT system logs.
- Use gait to detect possible network proxy activities.
- Examine VPN or other account login times, frequency, duration, and locations.
- Review standard directories for unusual files.
- Audit all network appliance and edge device configurations with indicators of malicious activity for signs of unauthorized or malicious configuration changes.
- Minimize and control use of remote access tools and protocols.
- For detailed information about mitigations and incident response, please refer to the full advisory.


