
On September 7, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and U.S. Cyber Command’s Cyber National Mission Force (CNMF) published a joint Cybersecurity Advisory (CSA), Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475.
According to the advisory, nation-state advanced persistent threat (APT) actors exploited CVE-2022-47966 to gain access to a public-facing application at an aeronautical sector organization. From there they established persistence and moved laterally through the organization’s network. CVE-2022-47966 allows for remote code execution on the ManageEngine application. APT actors also exploited CVE-2022-42475 to establish presence on the organization’s firewall device.
Technical Details
The investigation revealed that as early as January 2023, multiple nation-state APT actors were present on the organization’s network. The threat actors were observed leveraging disabled administrative account credentials and deleting logs from several critical servers in the environment, which prevented the ability to detect follow-on exploitation or data exfiltration. Below is a high-level summary of their tactics and techniques.
- Infiltration – (CVE-2022-47966 and CVE-2022-42475)
- CVE-2022-47966 – APT actors exploited a vulnerability to access the organization’s web server hosting the public-facing application Zoho ManageEngine ServiceDesk Plus.
- CVE-2022-42475 – APT actors exploited a heap-based buffer overflow vulnerability in FortiOS SSL-VPN to access the organization’s firewall device.
- Discovery – APT actors downloaded nmap.exe and npcap.exe to continue network and credential information gathering efforts. APT actors used these legitimate applications for malicious purposes.
- Persistence – Actors created a scheduled task to execute ssh.exe on a recurring basis. After compromising and utilizing account credentials from a previously hired contractor, they created a local account with administrative permissions on the server hosting ServiceDesk Plus.
- Credential Access – Actors successfully leveraged mimikatz and procdump to access and dump credentials, and dumped sam.hiv to obtain information about users on the system.
- Command and Control – Actors used various methods for C&C communication including third-party tools.
- Defense Evasion – Actors deleted logs, spawned hidden process, and used XPack to execute malicious payload.
Important Note for SafeBreach Customers – Coverage for CVE-2022-47966 and CVE-2022-42475
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It’s important to note that many of the attack tactics, techniques, and procedures (TTPs) used by these threat actors were already available in the SafeBreach playbook. Please run or re-run the attacks listed below to ensure your environments are protected.
Previously available playbook attacks for US-CERT Alert AA23-250A:
Mimikatz
- #794 Extract Login Information using MimiKatz
- #3829 Run obfuscated Mimikatz on host
- #5833 Extract Login Information using MimiKatz DCSync
Meterpreter:
- #262 – Remote Control using Meterpreter to Execute Persistence Commands
- #263 – Remote Control using Meterpreter to Change System Configuration
- #264 – Remote Control using Meterpreter to Execute File Commands
- #1042 – Remote Control using Meterpreter to Execute File Commands
- #7659 – Pre-execution phase of Meterpreter malware
XPack:
- #567 – Transfer of the TR/Crypt.XPACK.Gen5 trojan over HTTP/S
- #624 – Transfer of the TR/Crypt.Xpack.263533 trojan over HTTP/S
- #666 – Transfer of the TR/Crypt.Xpack.263533 trojan over HTTP/S
- #700 – Transfer of the TR/Crypt.XPACK.Gen5 trojan over HTTP/S
- #931 – Write TR/Crypt.Xpack.263533 trojan to disk
- #972 – Write TR/Crypt.XPACK.Gen5 trojan to disk
- #1710 – Email the TR/Crypt.XPACK.Gen5 trojan as a compressed attachment
- #1762 – Email the TR/Crypt.Xpack.263533 trojan as a compressed attachment
- #1912 – Email the TR/Crypt.XPACK.Gen5 trojan as a compressed attachment
- #1964 – Email the TR/Crypt.Xpack.263533 trojan as a compressed attachment
- #3218 – Pre-execution phase of TR/Crypt.Xpack.263533 trojan
- #3253 – Pre-execution phase of TR/Crypt.XPACK.Gen5 trojan
(T1003.001) Credential Dumping : LSASS Memory
- (1220) Inject Mimikatz using PowerShell to Extract Credentials,
- (6127) Extract LSASS memory dump using PowerShell and Rundll32,
- (6473) Agentless lateral movement via RDP,
- (6513) Agentless lateral movement via SMB and RCE, using Mimikatz,
- (794) Extract Login Information using MimiKatz
(T1053.005) Scheduled Task : Scheduled Task
- (1269) Creating Windows schedule task (schtasks.exe),
- (2164) Scheduled Task
(T1049) System Network Connections Discovery
- (1693) Collect Windows system data using CMD
(T1057) Process Discovery
- (2188) Extract Process List using Windows Commands
(T1564.001) Hide Artifacts : Hidden Files and Directories
- (2124) Hide a file – Windows
(T1040) Network Sniffing
- (1901) Capture network packets using WinPcap (Windows)
(T1021.001) Remote Services : Remote Desktop Protocol
- (6909) RDP Connection Between 2 Simulators
(T1136.001) Create Account : Local Account
- (2170) Create Account (Windows)
- (2189) Account Manipulation
- (7170) Add a local administrator (Windows)
(T1012) Query Registry
- (2194) Extract Credentials from the Registry using System Commands
(T1018) Remote System Discovery
- (2222) Discover Remote Systems using PowerShell,
- (6581) Discover domain computers using LDAP method
(T1543.003) Create or Modify System Process : Windows Service
- (2293) Create and Start a Service
(T1570) Lateral Tool Transfer
- (240) Upload File over SMB
(T1003.002) Credential Dumping : Security Account Manager
- (3828) Credentials collection using PwDump,
- (7169) Dump the SAM database from the registry (Windows)
(T1190) Exploit Public-Facing Application
- (6861) Remote exploitation of Apache Log4j vulnerability CVE-2021-44228
(T1078.003) Valid Accounts : Local Accounts
- (6473) Agentless lateral movement via RDP
(T1572) Protocol Tunneling
- (6910) RDP Tunneling
(T1564.003) Hide Artifacts : Hidden Window
- (7172) Spawn a hidden Powershell process,
- (7173) Spawn a hidden process (Windows)
(T1070.001) Indicator Removal on Host : Clear Windows Event Logs
- (7554) Clear Windows Event Logs
(T1046) Network Service Scanning
- (8018) Web application port scanning,
- (8019) Port scanning target simulator,
- (8020) Port scanning of local subnet network
(T1027.009) Obfuscated Files or Information : Embedded Payloads
- (8367) Embedded payloads (Windows)
Newly added playbook methods for US-CERT Alert AA23-250A:
Metasploit
- #9137 – Write Metasploit (3bfb63) hacktool to disk
- #9138 – Pre-execution phase of Metasploit (3bfb63) hacktool (Windows)
- #9139 – Transfer of Metasploit (3bfb63) hacktool over HTTP/S
- #9140 – Transfer of Metasploit (3bfb63) hacktool over HTTP/S
- #9141 – Email Metasploit (3bfb63) hacktool as a compressed attachment
- #9142 – Email Metasploit (3bfb63) hacktool as a compressed attachment
- #9143 – Write Metasploit (59ff4b) hacktool to disk
- #9144 – Pre-execution phase of Metasploit (59ff4b) hacktool (Windows)
- #9145 – Transfer of Metasploit (59ff4b) hacktool over HTTP/S
- #9146 – Transfer of Metasploit (59ff4b) hacktool over HTTP/S
- #9147 – Email Metasploit (59ff4b) hacktool as a compressed attachment
- #9148 – Email Metasploit (59ff4b) hacktool as a compressed attachment
#8338 – Remote exploitation of ManageEngine products (CVE-2022-47966)
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
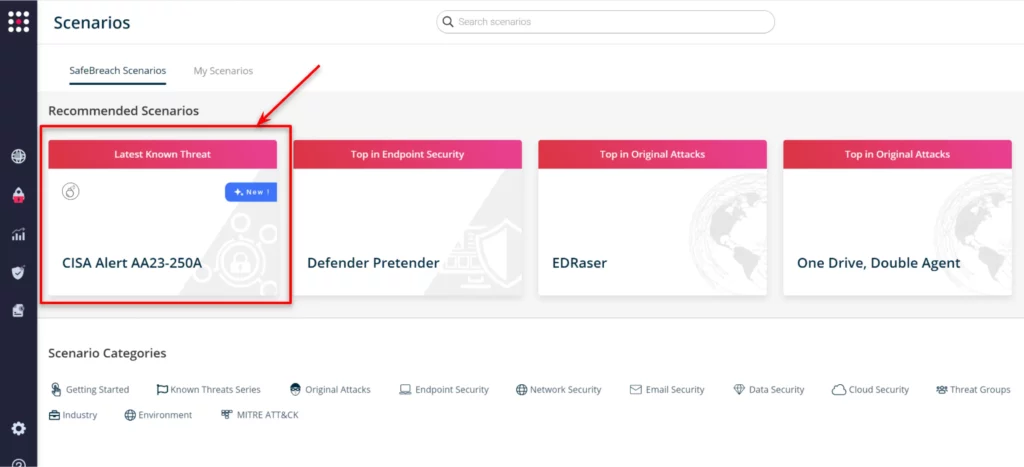
On the Scenarios page, choose the AA23-250A scenario from the list of available scenarios.
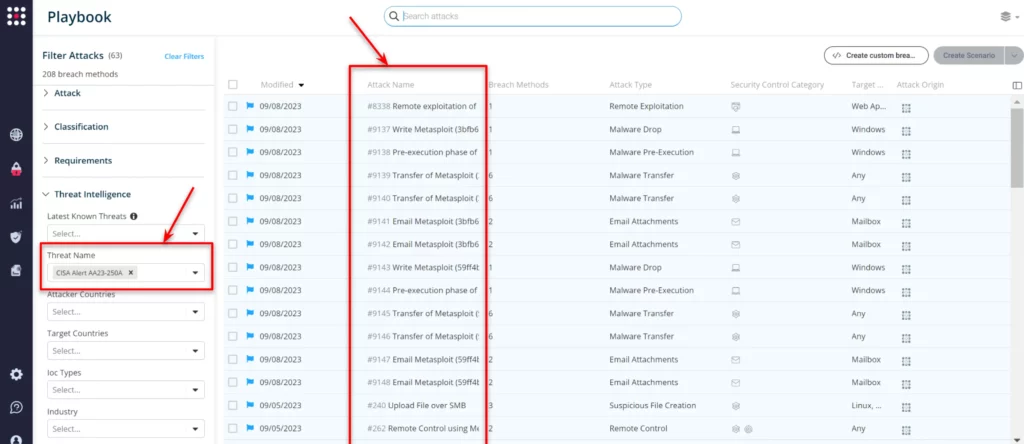
From the Attack Playbook page, select and filter attacks related to US-CERT Alert AA23-250A. You can also refer to the list above to ensure a comprehensive level of coverage.
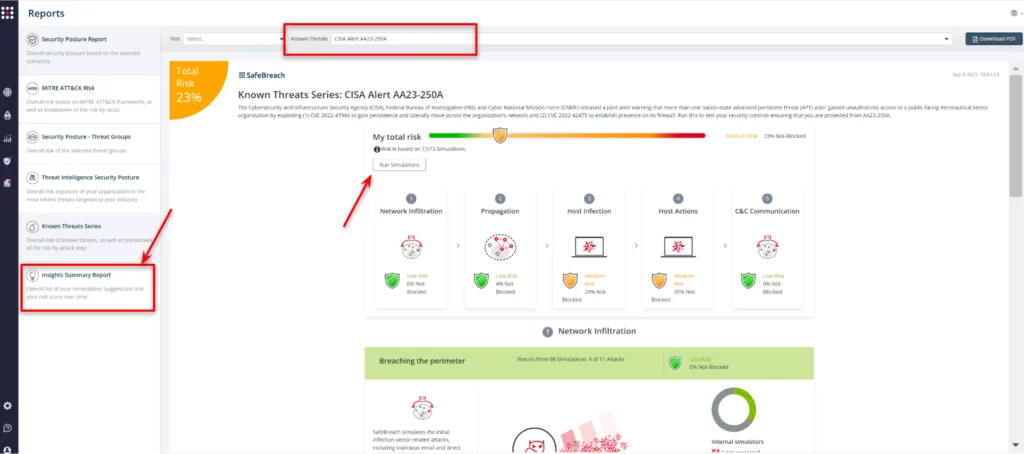
Finally, from the Known Attack Series report, select the AA23-250A report and select Run Simulations, which will run all attack methods.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Patch all systems for known exploited vulnerabilities (KEVs), including firewall security appliances.
- Monitor for unauthorized use of remote access software using endpoint detection tools.
- Remove unnecessary (disabled) accounts and groups from the enterprise that are no longer needed, especially privileged accounts.
For detailed information and incidence response, please refer to the full advisory.
