On February 26th, Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory asking organizations and entities to stay alert and prepared for potential cyberattacks leveraging two newly discovered wiper malwares known as WhisperGate and HermeticWiper. Details of the various tactics, techniques, and procedures (TTPs) are available in US-CERT Alert (AA22-057) Destructive Malware Targeting Organizations in Ukraine. Attackers had deployed these destructive malware against organizations in Ukraine to destroy computer systems and render them inoperable. Entities are requested to stay vigilant as it may unintentionally spill over to organizations in other countries and may be leveraged by opportunistic APT threat actors to disable critical infrastructure and systems and create chaos.
Additional details about WhisperGate and HermeticWiper
- Information about WhisperGate was disclosed by researchers at Microsoft Threat Intelligence Center (MSTIC) who first observed its occurrence on January 13th, 2022. They observed this malware to be a two-stage malware that first overwrites the Master Boot Record (MBR) on victim computers and then executes when the device is powered down, corrupting files, and rendering the device inoperable.
- The HermeticWiper was first observed on February 23rd by several researchers at Symantec and ESET research and further analysis revealed that it was a custom application with very few standard functions. It uses a signed driver to deploy the malware and manipulate the MBR by corrupting its first 512 bytes, resulting in subsequent boot load failure.
IMPORTANT NOTE for SafeBreach Customers
As soon as details and IOCs for WhisperGate were first available, corresponding attacks were immediately added to the SafeBreach Hacker’s Playbook™ on January 20th. Additional TTPs and IOCs related to WhisperGate (discovered after initial observation), were added to our playbook on February 13th. Attacks pertaining to the newly discovered HermeticWiper are now available in the playbook and ready to be run individually or as part of the AA22-057A Destructive Wiper Malware scenario. We encourage you to evaluate your preparedness against WhisperGate and HermeticWiper by running the attacks listed below. Additionally, we would also recommend you validate/revalidate your controls against attacks identified in US-CERT AA22-047A and US-CERT AA21-148A.
We would also recommend everyone to leverage useful resources and links available in our blog Russia-Ukraine Crisis: Resources for Securing Organizational Posture During Geopolitical Uncertainty.
SafeBreach Coverage for AA22-057A – Destructive Wiper Malware
11 newly added playbook methods for HermeticWiper:
- #6936 – Email HermeticWiper RCDATA_DRV_X64_empntdrv malware as a ZIP attachment (Infiltration)
- #6935 – Email HermeticWiper RCDATA_DRV_X64_empntdrv malware as a ZIP attachment (propagation)
- #6934 – Transfer of HermeticWiper RCDATA_DRV_X64_empntdrv malware over HTTP/S (Infiltration)
- #6933 – Transfer of HermeticWiper RCDATA_DRV_X64_empntdrv malware over HTTP/S (propagation)
- #6932 – Write HermeticWiper RCDATA_DRV_X64_empntdrv malware to disk (Host Actions)
- #6931 – Email HermeticWiper malware as a ZIP attachment (Infiltration)
- #6930 – Email HermeticWiper malware as a ZIP attachment (propagation)
- #6929 – Transfer of HermeticWiper malware over HTTP/S (Infiltration)
- #6928 – Transfer of HermeticWiper malware over HTTP/S (propagation)
- #6927 – Write HermeticWiper malware to disk (Host Actions)
- #6926 – Pre-execution phase of HermeticWiper malware (Host Actions)
12 previously added attack methods related to WhisperGate:
- #6891 – Email WhisperGate_stage2 malware as a ZIP attachment (Infiltration)
- #6890 – Email WhisperGate_stage2 malware as a ZIP attachment (propagation)
- #6889 – Transfer of WhisperGate_stage2 malware over HTTP/S (Infiltration)
- #6888 – Transfer of WhisperGate_stage2 malware over HTTP/S (propagation)
- #6887 – Write WhisperGate_stage2 malware to disk (Host Actions)
- #6886 – Pre-execution phase of WhisperGate_stage2 malware (Host Actions)
- #6885 – Email WhisperGate_stage1 malware as a ZIP attachment (Infiltration)
- #6884 – Email WhisperGate_stage1 malware as a ZIP attachment (propagation)
- #6883 – Transfer of WhisperGate_stage1 malware over HTTP/S (Infiltration)
- #6882 – Transfer of WhisperGate_stage1 malware over HTTP/S (propagation)
- #6881 – Write WhisperGate_stage1 malware to disk (Host Actions)
- #6880 – Pre-execution phase of WhisperGate_stage1 malware (Host Actions)
What you should do now
Attack methods related to US-CERT AA22-057A (Destructive Malware) are ready to run across your simulators. The Known Attack Series report has been updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT AA22-057A (Destructive Malware) report and select Run Simulations which will run all attack methods.
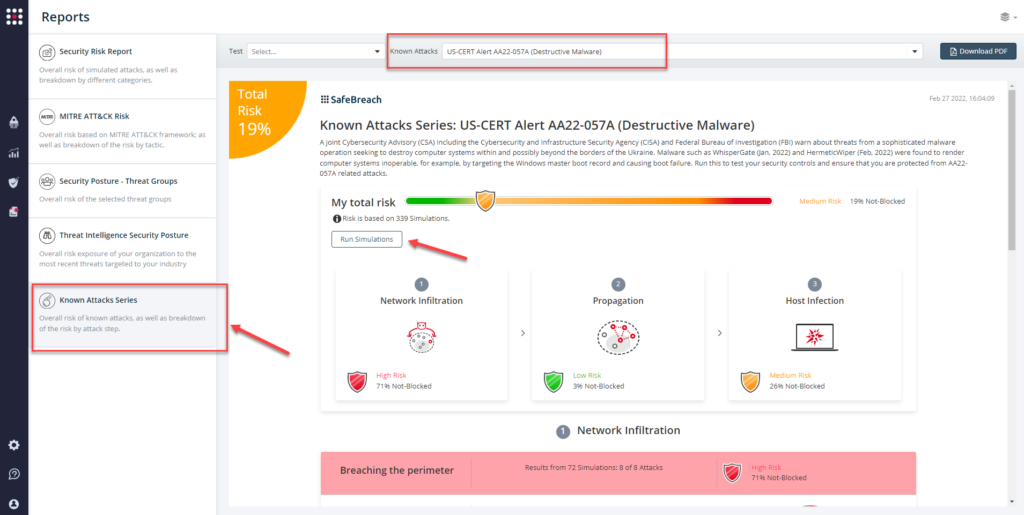
You can also select all the attacks related to US-CERT AA22-057A (Destructive Malware), by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT AA22-057A (Destructive Malware)
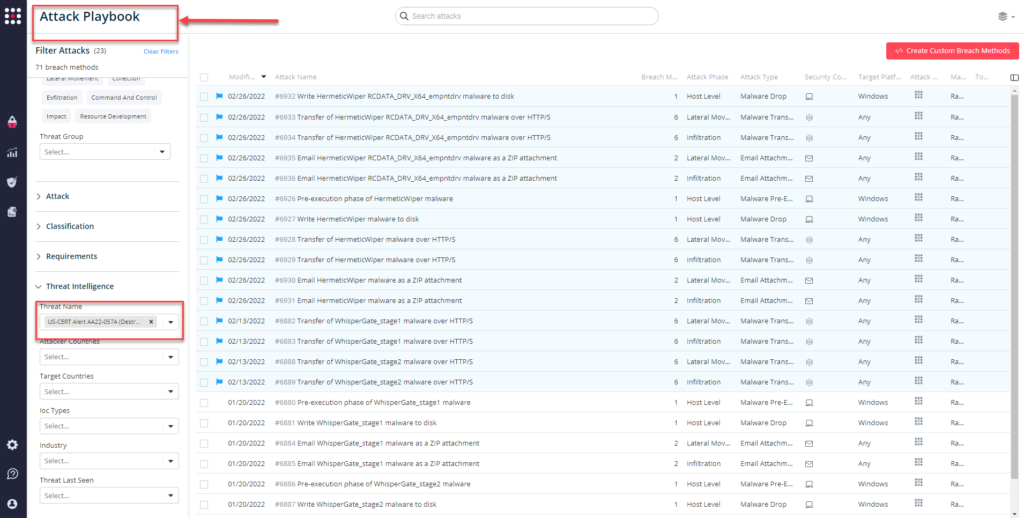
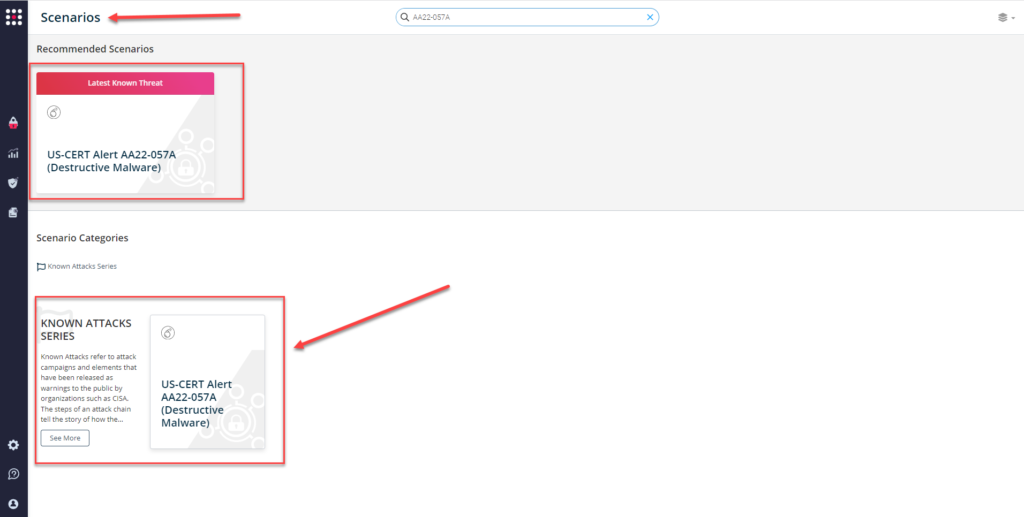
or you can go to the “SafeBreach Scenarios” page and choose the US-CERT AA22-057A (Destructive Malware) scenario from the list of available scenarios.
NOTE – The following actions have been recommended by CISA to ensure additional protection against destructive malware:
- Set antivirus and anti-malware programs to conduct regular scans
- Enable strong spam filters to prevent phishing emails from reaching end users
- Filter network traffic
- Update software
- Require multifactor authentication
Additional Useful Resources –
- CISA Shields Up Technical Guidance
- ESET Research Tweet: Breaking. #ESETResearch discovered a new data wiper malware used in Ukraine today. ESET telemetry shows that it was installed on hundreds of machines in the country.
- SentinelLabs: HermeticWiper | New Destructive Malware Used in Cyber Attacks on Ukraine
- Broadcom’s Symantec Threat Hunter Team: Ukraine: Disk-wiping Attacks Precede Russian Invasion
- Joint Cybersecurity Advisory — Technical Approaches to Uncovering and Remediating Malicious Activity
- US-CERT AA22-011A — Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure
- Russia Cyber Threat Overview and Advisories
- US-CERT AA22-054A — New Sandworm Malware Cyclops Blink Replaces VPNFilter
- SafeBreach coverage for US-CERT AA22-047A
- SafeBreach coverage for US-CERT AA21-148A