SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples described in US CERT AA21-055A detailing four zero-day vulnerabilities in Accellion File Transfer Appliance (FTA). The threat actor was able to install a new web shell attack named DEWMODE. The attackers are targeting Accellion FTA customers in order to steal confidential data, then subsequently attempting to extort money from the victim organizations to prevent public release of the exfiltrated data.
Here is an overview SafeBreach Hacker’s Playbook timeline based on US-Cert Alert updates only:
5 newly developed playbook methods related to AA21-055A:
- #5972 – Write DEWMODE malware to disk (Host-Level)
- #5973 – Transfer of DEWMODE malware over HTTP/S (Lateral Movement)
- #5974 – Transfer of DEWMODE malware over HTTP/S (Infiltration)
- #5975 – Email DEWMODE malware as a ZIP attachment (Lateral Movement)
- #5976 – Email DEWMODE malware as a ZIP attachment (Infiltration)
What you should do now
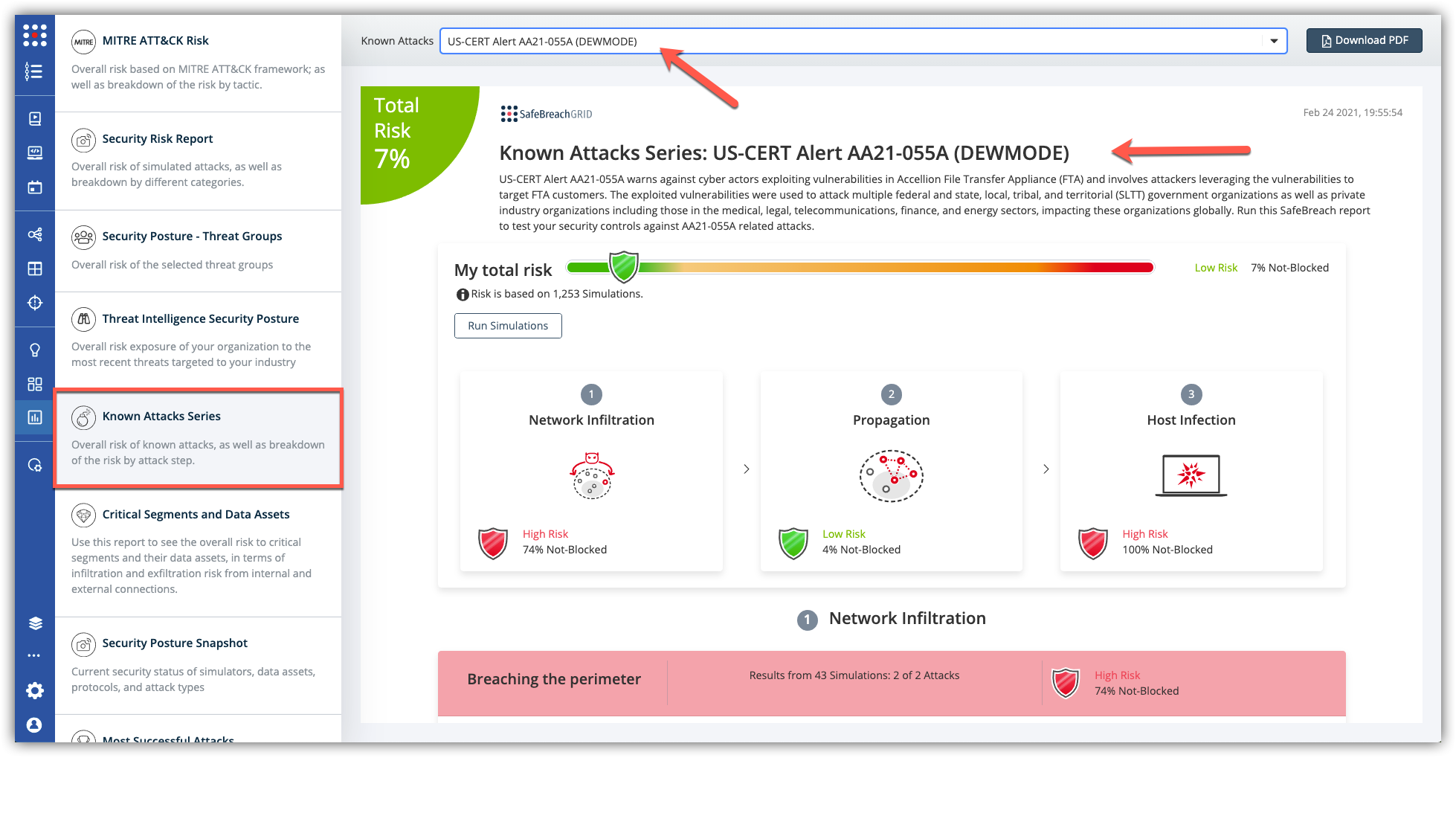
The new attack methods for US-CERT AA21-055A are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA21-055A report and select Run Simulations which will run all the attack methods.