Active Directory (AD) is the most common directory service in the world, providing a broad range of services that allow administrators to manage permissions and access to network resources. Developed by Microsoft for Windows domain networks, AD is included in most Windows server operating systems and, as such, is used by some of the largest enterprises in the world.
In the last few months, we have seen an increase in the use of AD attacks to exploit unpatched or partly patched critical vulnerabilities. This includes the lockFile ransomware, which uses PetitPotam as described here. Historically, there have been two ways for an organization to protect itself against these types of attacks: to manually set specific configurations in their environment and/or to use third-party security controls. However, it can be difficult for an organization to verify that it is actually safe even after taking these precautions, since the first time security controls are tested is typically during a real-world attack.
Breach and attack simulation (BAS) tools are changing that by allowing organizations to accurately and safely simulate attacks and attacker behavior to test their security controls, identify gaps, and take remediation steps before real-world attacks happen. As we did with the RemotePotato0 unpatched vulnerability, we will use this blog to explain two AD attacks an attacker may use to escalate privileges in an organization using three known vulnerabilities: CVE-2021-369429 (PetitPotam), CVE-2021-42278, and CVE-2021-42287. We will also outline the challenges organizations may face if they choose to manually test their security controls against these complex Domain Admin privilege escalation attacks and explain how the SafeBreach platform can be used to safely and proactively test controls instead.
About the Authentication Protocols Involved
The attacks discussed in this blog exploit vulnerabilities using the NTLM and Kerberos authentication protocols. We have written a short, high-level technical dictionary below for those who are not familiar with these protocols.
- Kerberos: A ticket-based authentication protocol that allows network nodes to authenticate one another securely.
- KDC: The Key Distribution Center, which is the Microsoft implementation of the Kerberos authentication protocol. It is a domain service that is responsible for creating TGTs and STs.
- TGT: A ticket-granting ticket, which is a Kerberos ticket generated by the KDC that is used in order to authenticate and request service tickets.
- ST: A service ticket, which is an additional type of Kerberos ticket that is generated by the KDC. This ticket is used in order to access services in the domain.
- AD CS: Active Directory Certificate Services (AD CS), which are domain services for issuing and managing public key infrastructure (PKI) certificates. The digital certificates that AD CS provides can be used for authentication of the computer, user, or device accounts on the domain.
- NTLM: A suite of security protocols offered by Microsoft to authenticate users’ identity and protect the integrity and confidentiality of their activity. For more information about NTLM and NTLM Relay attacks, see this blog post.
- EFSRPC: Encrypted File System Remote Protocol, which is Microsoft’s protocol for performing maintenance and management operations on encrypted data in remote machines.
About the Vulnerabilities Involved
This section provides insight about each CVE vulnerability. For more information about the acronyms, see the technical dictionary above.
Petit Potam’s CVE-2021-369429
PetitPotam is a recent AD vulnerability that was found by Gilles Lionel. The vulnerability allows an unprivileged domain user to abuse the domain controller’s permissions in order to escalate to a privileged user in the domain, such as a Domain Admin.
This is done using EfsRpcOpenFileRaw, a type of message that can be sent as a part of the EFSRPC protocol by Microsoft. This message is a request to open an encrypted object on a remote server. In order to identify the object in the request, an EFSRPC identifier must be passed. The identifier should be in a UNC path format. A UNC path contains the hostname or the IP of the server that contains the target object. When an EfsRpcOpenFileRaw request is sent to a Domain Controller, it starts by authenticating against the server specified in the EFSRPC identifier. This authentication is done by NTLM on behalf of the machine account of the Domain Controller.
Due to the fact that any user in the domain can send this request to the Domain Controller, it is possible for any user to trigger an NTLM authentication against any preferred server. When an attacker has this ability, NTLM Relay can be used in order to steal the permissions of the entity trying to authenticate, namely the permissions of the Domain Controller in this case.
Microsoft released a patch to block this possibility; however, a bypass for the patch was quickly developed using the EfsRpcEncryptFileSrv request instead. It remains unpatched to this day.
If you are unfamiliar with the NTLM Relay technique, you can read about it in our blog post about RemotePotato0.
CVE-2021-42278 and CVE-2021-42287
These two AD vulnerabilities were found by Andrew Bartlett of Catalyst IT and, when chained together, allow for an unprivileged domain user to impersonate any computer account in the domain, including the Domain Controller.
CVE-2021-42278 is a name-impersonation vulnerability. The convention is that computer accounts in the domain should have a trailing $ in their name; however, there is no validation process to make sure this is the case.
CVE-2021-42287 is a vulnerability in the KDC. When requesting an ST from the KDC, we must present a TGT. If the ST for the required user is not found, the KDC automatically tries again with a trailing $.
Microsoft has released an authentication update (KB5008380) that allows users to configure the system so that the attack will be blocked. But this raises a key question about how an organization can easily verify that it has applied the patch correctly.
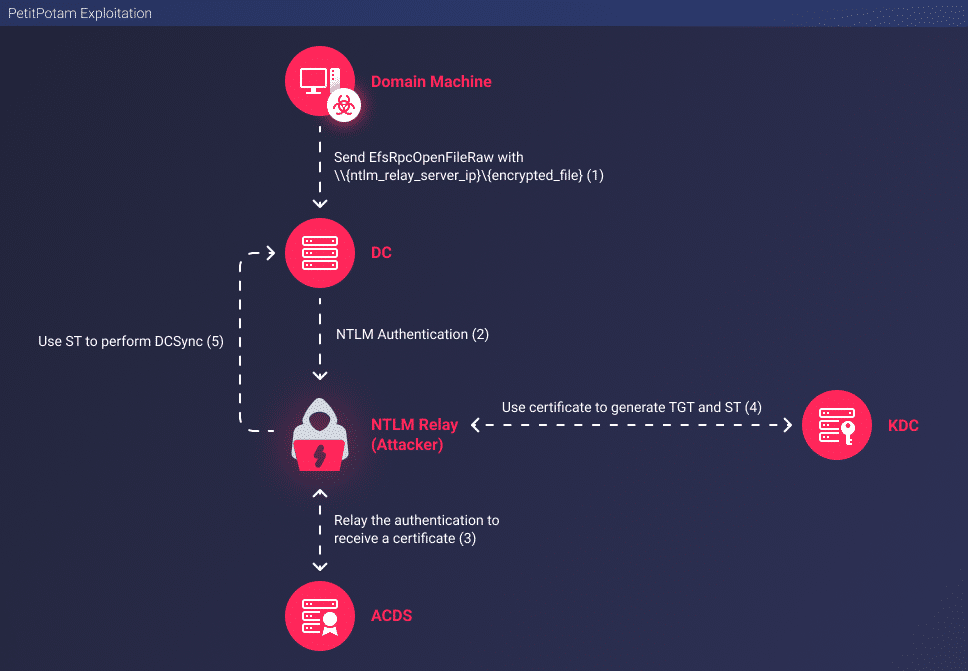
How Attackers Perform the PetitPotam Exploit
The following process describes the actions taken by attackers using the PetitPotam exploit:
- Find the hostname/IP of the Active Directory Certificate Services (ADCS) server in the domain.
- Set up an NTLM Relay server on an attacker’s server. The relay is targeting the ADCS server in the domain.
- Send an EfsRpcOpenFileRaw request to the Domain Controller with an attacker’s server mentioned in the EFSRPC identifier.
- The Domain Controller starts with NTLM authentication against the attacker’s server.
- The credentials of the machine account of the Domain Controller are relayed to the certificate services of the domain in order to produce a certificate. The certificate identifies the machine account of the Domain Controller.
- Use the certificate to retrieve a TGT.
- Use the TGT to generate an ST.
- Perform DCsync in order to retrieve privileged users’ credentials.
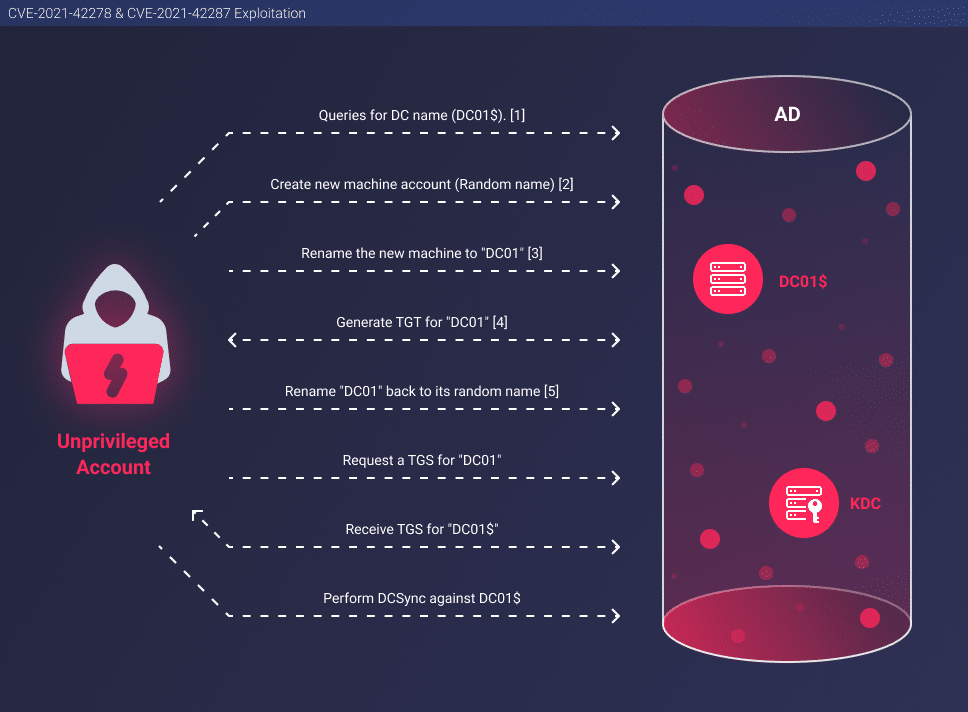
How Attackers Weaponize CVE-2021-42278 and CVE-2021-42287
The following process describes the actions taken by attackers when exploiting CVE-2021-42278 and CVE-2021-42287:
- Find the name of the Domain Controller computer account.
- Create a computer account with a random name.
- Rename the computer account created by the attacker to the name of the computer account of the Domain Controller, without the trailing $. (CVE-2021-42278)
- Obtain a TGT for the computer account created by the attacker.
- Rename the computer account back to its original name.
- Request an ST with the obtained TGT for the attacker’s computer account and by that actually obtain an ST for the Domain Controller. (CVE-2021-42287)
- Perform a DCSync in order to retrieve privileged users’ credentials.
Manual Weaponization of Attacks
An organization could manually weaponize these attacks to test their security controls. However, there are consequences that must be reversed.
- Weaponizing PetitPotam causes the original ntlmrelayx.py script, which is the most popular tool used for NTLM Relay, to send back a STATUS_NETWORK_SESSION_EXPIRED error message to the Domain Controller when it authenticates against it. That causes the Domain Controller to repeatedly try and authenticate over and over again.
- Weaponizing CVE-2021-42278 and CVE-2021-42287 causes a new machine account to be created in the domain.
Simulated Attacks with SafeBreach
As with all of the attacks in the Safebreach Hacker’s Playbook™, we are able to simulate the PetitPotam, CVE-2021-42278, and CVE-2021-42287 attacks in the safest and most accurate way possible. We are able to execute a full exploit path as seen in the wild, while avoiding the consequences of manual weaponization noted in the previous section.
This is accomplished by changing the NTLM Relay implementation to return a different status cause, which causes the Domain Controller to stop trying to authenticate again and again. And, in regard to the newly created machine account, there is no memory left from it after the attack has been completed using the SafeBreach platform.
Using the SafeBreach platform is also much less complex than the manual setup for testing, requiring only the minimal configurations identified below:
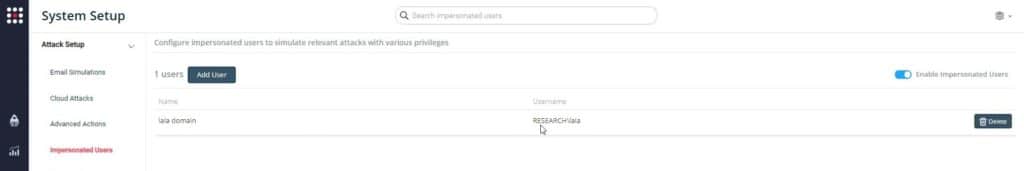
- In order to run the attack, you must set up an impersonated user using the System Setup. Select “Settings->Attack Setup->Impersonated Users”.
- To exploit PetitPotam, choose attack #6911 and/or attack #6912 from the Hacker’s Playbook. To exploit CVE-2021-42278 and CVE-2021-42287, choose attack #6892.
- Select “Run->Select simulators” to run.
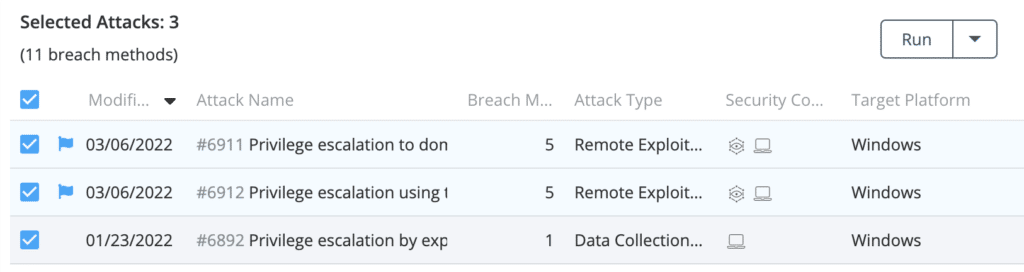
- Choose the simulators you want to run the attack on and press “Run->Run Now”.
That is it. In a matter of seconds, you are able to have results regarding your organization’s level of protection against these attacks that you can use to identify gaps, prioritize vulnerabilities, and take proactive remediation steps before breaches occur.
AUTHOR’S NOTE: The information provided in this blog was a joint contribution between Or Yair and Saar Hamam.