On September 20th, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory highlighting the various indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with the Snatch ransomware variant. This variant was identified as recently as June 1, 2023, by the FBI. Detailed information is listed in US-CERT Alert AA23-263A – #StopRansomware: Snatch Ransomware.
According to the advisory, threat actors leveraging Snatch ransomware have been observed evolving their TTPs since mid-2021. These threat actors have targeted a wide range of critical infrastructure sectors including the Defense Industrial Base (DIB), Food and Agriculture, and Information Technology sectors. These attacks often involve data exfiltration and double extortion. Once the threat actors acquire this data, they often contact victims to force them to pay ransom. Refusal to pay ransom can often lead to stolen data being posted on a blog (owned by Snatch threat actors). The FBI also observed the threat actors purchasing previously stolen data from other ransomware operations to further exploit those victims who refused to pay ransom.
Technical Details
The Snatch threat actors first operated their ransomware-as-a-service model in 2018 and claimed their first U.S. victim in 2019. Originally, the group was referred to as Team Truniger, based on the nickname of a key group member, Truniger, who previously operated as a GandCrab affiliate. Snatch threat actors use a customized ransomware variant notable for rebooting devices into Safe Mode enabling the ransomware to circumvent detection by antivirus or endpoint protection, and then encrypting files when few services are running.
Initial Access and Persistence – Initial access is primarily gained by exploiting weaknesses in Remote Desktop Protocol (RDP) for brute-forcing and gaining administrator credentials to victims’ networks. Snatch threat actors have also used the dark web to purchase previously stolen/compromised credentials. Persistence is typically gained and maintained by compromising an administrator account and establishing network connections over port 443 to a command and control (C2) server located on a Russian bulletproof hosting service. Snatch threat actors were observed initiating RDP connections from the bulletproof hosting service to other VPN services.
Data Discovery and Lateral Movement – The FBI observed the Snatch threat actors leveraging several different TTPs to perform data discovery, move laterally in victim networks, and identify critical victim data to exfiltrate. Snatch threat actors were also observed using “sc.exe” to configure, query, stop, start, delete, and add system services using the Windows Command line. Additionally, they have also used tools like Metasploit and Cobalt Strike to further their malicious objectives.
Defense Evasion and Execution – In the initial stages of ransomware deployment, Snatch threat actors attempt to disable any deployed antivirus software and run an executable file named “safe.exe” or some variation thereof. Upon initiation, the Snatch ransomware payload queries and modifies registry keys, uses various native Windows tools to enumerate the system, finds processes, and creates benign processes to execute Windows batch (.bat) files. In some instances, the program attempts to remove all the volume shadow copies from a system. After the execution of the batch files, the executable removes the batch files from the victim’s filesystem. The Snatch ransomware was also observed appending a series of hexadecimal characters to each file and folder name it encrypts—unique to each infection—and leaves behind a text file titled HOW TO RESTORE YOUR FILES.TXT in each folder. Snatch threat actors communicate with their victims through email and the Tox communication platform based on identifiers left in ransom notes or through their extortion blog.
Communications between Attackers and Victims – Since November 2021, some victims reported receiving a spoofed call from an unknown female who claimed association with Snatch and directed them to the group’s extortion site. In some instances, Snatch victims had a different ransomware variant deployed on their systems, but received a ransom note from Snatch threat actors. As a result, the victims’ data is posted on the ransomware blog involving the different ransomware variant and on the Snatch threat actors’ extortion blog.
Important Note for SafeBreach Customers – Coverage for AA23-263A (Snatch Ransomware)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers already had a wide amount of coverage against the IOCs and TTPs being leveraged by the threat actors. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
Existing Behavioral Attacks Related to Snatch Ransomware
- #1011 – Discover Linux system information using Bash commands (host level)
- #1693 – Collect Windows system data using CMD (host level)
- #1694 – Collect macOS system data using bash (host level)
- #2192 – Collect Data from Local Shared Drives using System Commands (host level)
- #2266 – Collect Google Chrome Bookmarks (host level)
- #1373 – Brute force attack over SIP protocol (lateral movement)
- #1374 – Impersonation attack over SIP protocol (lateral movement)
- #174 – Brute force attack over Telnet Protocol (lateral movement)
- #222 – Brute force attack over TDS protocol (MSSQL) (lateral movement)
- #258 – Brute force attack over the HTTP/S protocol (lateral movement)
- #1693 – Collect Windows system data using CMD (host level)
- #1695 – Discover Linux processes using Bash scripts (host level)
- #2188 – Extract Process List using Windows Commands (host level)
- #6871 – Discover macOS processes using Bash scripts (host level)
- #192 – Brute force attack over RDP protocol (lateral movement)
- #6473 – Agentless lateral movement via RDP (host level)
- #6909 – RDP Connection Between 2 Simulators (lateral movement)
- #6910 – RDP Tunneling (host level)
- #2194 – Extract Credentials from the Registry using System Commands (host level)
- #803 – Enable Administrator Shares (host level)
- #2199 – Space after Filename (Linux, macOS) (host level)
- #2248 – Masquerading (host level)
- #3829 – Run obfuscated Mimikatz on host (host level)
- #5388 – Exploit CVE-2020-1464 on Windows (host level)
- #6797 – Write a file ending with suspicious double extension to disk (host level)
- #6949 – Write eicar file to disk on a legitimate path (Linux) (host level)
- #6950 – Write eicar file to disk on a legitimate path (Mac) (host level)
- #8045 – Masquerading right to left override (host level)
- #8046 – Email executable with RTLO attachment (infiltration)
- #8047 – Email executable with RTLO attachment (lateral movement)
- #8048 – Email textual file with RTLO attachment (lateral movement)
- #8049 – Email textual file with RTLO attachment (infiltration)
- #8328 – Rename System Utilities (Linux) (host level)
- #2244 – Windows Management Instrumentation Event Subscription (host level)
- #2249 – Indicator Removal on Host (Linux) (host level)
- #2267 – Add an exclusion to Windows Defender using PowerShell (host level)
- #2389 – Modify Firewall Rules using netsh.exe (host level)
- #5107 – Stop a service using net stop command (host level)
- #7043 – Disable Cortex XDR using its default password (Windows) (host level)
- #7044 – Disable Cortex XDR using its default password (Linux) (host level)
- #7144 – Unregister anti malware scanning interface providers (host level)
- #7209 – Suppress alerts within Defender for Cloud (Azure) (infiltration)
- #7834 – Add Exclusions to Windows Defender (host level)
- #7835 – Disable Windows Defender From Registry (host level)
- #8023 – EDR evasion by overriding `ntdll` .text section (host level)
- #8024 – EDR evasion by overriding `ntdll` hooked functions (host level)
- #8853 – Disable rules in Windows Defender to allow credential harvesting using Lazagne (host level)
- #8856 – Create rule in Windows Defender to delete arbitrary file (host level)
- #8857 – Add Mimikatz as exclusion to Windows Defender and execute Mimikatz (host level)
- #2293 – Create and Start a Service (host level)
- #2357 – File System Permissions Weakness (host level)
- #904 – Start the secondary logon service (host level)
- #905 – Start the remote registry service (host level)
- #907 – Start the Distributed COM Service (host level)
- #912 – Start the SSDP discovery service (host level)
- #5670 – Agentless lateral movement via Remote Registry (host level)
- #796 – Enable IPv6 (host level)
- #803 – Enable Administrator Shares (host level)
- #905 – Start the remote registry service (host level)
- #6372 – Modify Volume Shadow Copy (VSS) (host level)
- #7168 – Enable a default account and add it to a Local group (Windows) (host level)
- #6473 – Agentless lateral movement via RDP (host level)
Newly Added Attacks Related to Snatch Ransomware
- #9169 – Write DefenderControl (8fe7ae) hacktool to disk
- #9170 – Pre-execution phase of DefenderControl (8fe7ae) hacktool (Windows)
- #9171 – Transfer of DefenderControl (8fe7ae) hacktool over HTTP/S
- #9172 – Transfer of DefenderControl (8fe7ae) hacktool over HTTP/S
- #9173 – Email DefenderControl (8fe7ae) hacktool as a compressed attachment
- #9174 – Email DefenderControl (8fe7ae) hacktool as a compressed attachment
- #9175 – Write Snatch (e70bcd) ransomware to disk
- #9176 – Pre-execution phase of Snatch (e70bcd) ransomware (Windows)
- #9177 – Transfer of Snatch (e70bcd) ransomware over HTTP/S
- #9178 – Transfer of Snatch (e70bcd) ransomware over HTTP/S
- #9179 – Email Snatch (e70bcd) ransomware as a compressed attachment
- #9180 – Email Snatch (e70bcd) ransomware as a compressed attachment
- #9181 – Write Snatch (acff7c) ransomware to disk
- #9182 – Pre-execution phase of Snatch (acff7c) ransomware (Windows)
- #9183 – Transfer of Snatch (acff7c) ransomware over HTTP/S
- #9184 – Transfer of Snatch (acff7c) ransomware over HTTP/S
- #9185 – Email Snatch (acff7c) ransomware as a compressed attachment
- #9186 – Email Snatch (acff7c) ransomware as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
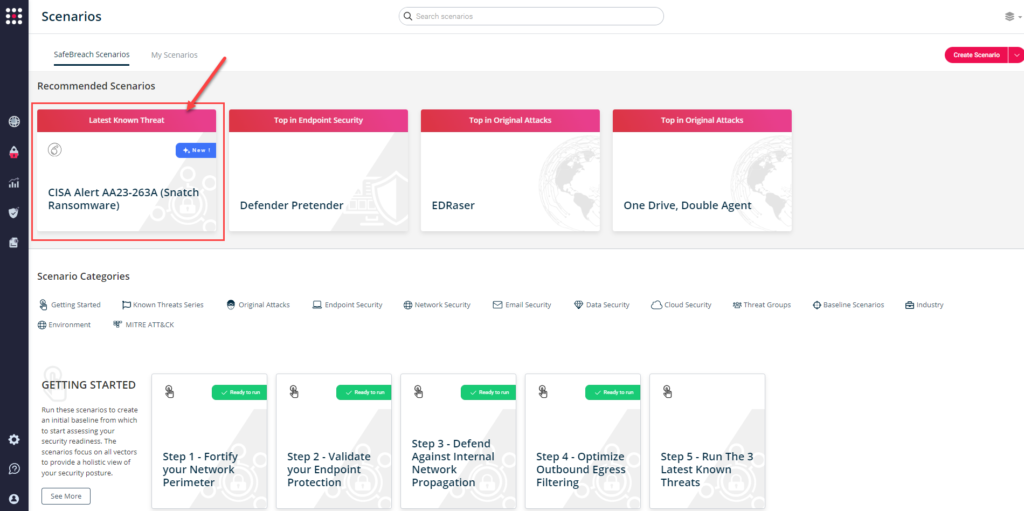
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA23-263A (Snatch Ransomware) scenario from the list of available scenarios.
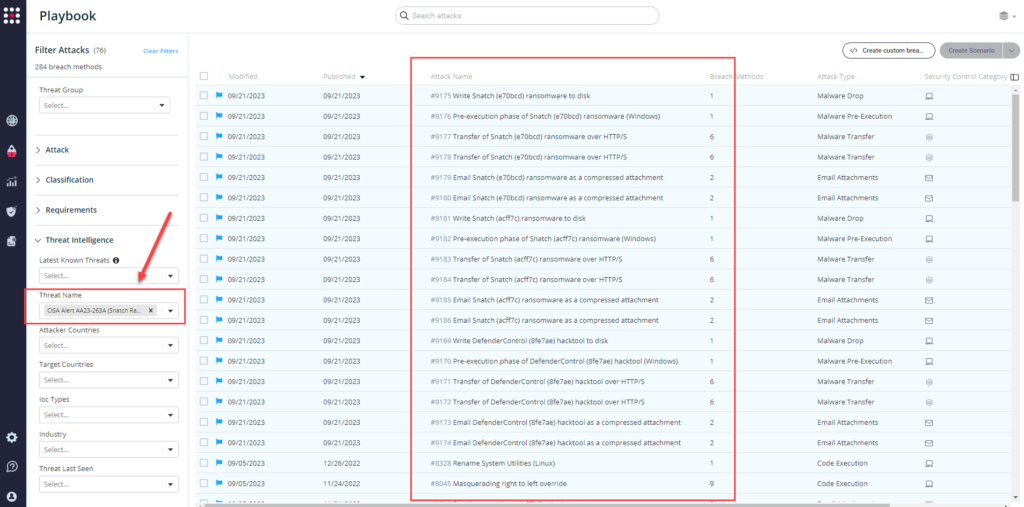
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-263A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
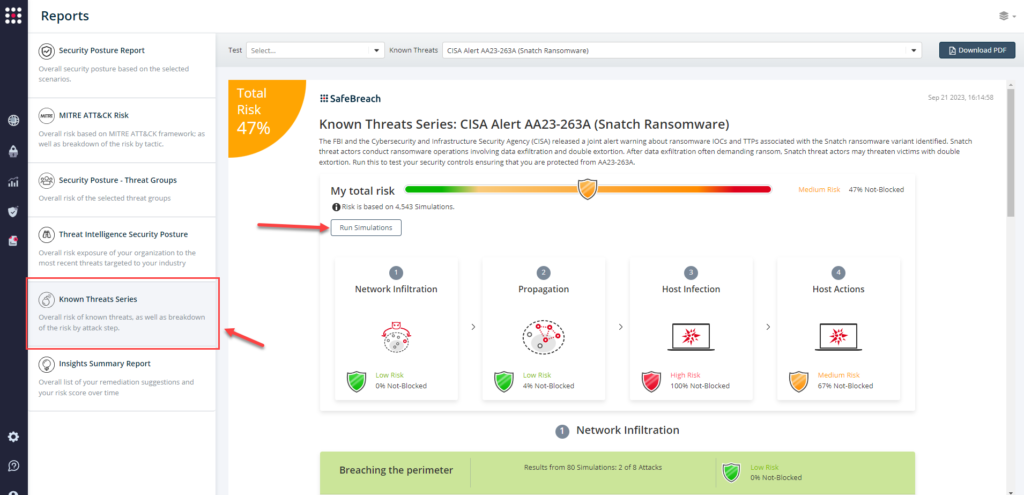
Method 3 – From the Known Attack Series report, select the AA23-263A (Snatch Ransomware) report and select Run Simulations which will run all attack methods.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Reduce threat of malicious actors using remote access tools by auditing remote access tools, reviewing logs for execution of remote access software, using software to detect instances of remote access software being loaded, requiring authorized remote access solutions, and blocking inbound and outbound connections on common remote access ports.
- Implement application controls to manage and control execution of software, including allowlisting remote access programs.
- Strictly limit the use of RDP and other remote desktop services.
- Disable command-line and scripting activities and permissions.
- Require phishing-resistant multifactor authentication (MFA).
- Keep all operating systems, software, and firmware up to date.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- For detailed information about mitigations and incident response, please refer to the full advisory

