On November 17th, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), the Federal Bureau of Investigation (FBI), the Australian Cyber Security Centre (ACSC), and the United Kingdom’s National Cyber Security Centre (NCSC) issued an alert to highlight ongoing malicious cyber activity by an advanced persistent threat (APT) group that FBI, CISA, ACSC, and NCSC assess is associated with the government of Iran. Details of the various tactics, techniques, and procedures (TTPs) are described in US-CERT Alert (AA21-321A) – Iranian Government-Sponsored APT Cyber Actors Exploiting Microsoft Exchange and Fortinet Vulnerabilities in Furtherance of Malicious Activities.
According to the information available, these state-sponsored threat actors have targeted a broad range of victims across multiple U.S. critical infrastructure sectors, including the transportation sector, healthcare and public health sector, as well as several Australian organizations. The attacks aimed to – steal and exfiltrate sensitive information as well as encrypt the data and hold it for a ransom. The attacks began in March 2021 and were initiated by exploiting the following existing vulnerabilities in Microsoft Exchange and Fortinet devices:
- CVE-2018-13379 – Path Traversal of Fortigate VPN vulnerability (first seen in March 2021)
- CVE-2019-5591 – FortiOS – Missing Authentication for Critical Function
- CVE-2020-12812 – FortiOS SSL VPN – 2FA bypass by changing username case
- CVE-2021-34473 – Microsoft Exchange (Proxyshell exploit) – active since October 2021
Once the attackers successfully exploited the vulnerabilities and gained access, they hijacked legitimate tools and processes (including – MicrosoftOutlookUpdater, MimiKatz, WinPEAS, WMI, FileZilla, Bitlocker) to install malware/ ransomware, escalate privileges, move laterally, steal and exfiltrate sensitive data, and hold it for ransom by encrypting it on their way out.
NOTE – The SafeBreach Hacker’s Playbook has been updated to include the newly discovered tactics and techniques from this US-CERT alert. We encourage you to test your preparedness against the Iranian threat groups by running the attacks listed below. Additionally, we would also recommend you consider running/ re-running attacks described in US-CERT AA21-259A and US-CERT AA21-296B to ensure a more comprehensive level of protection against Iranian state-sponsored APT groups.
12 newly developed playbook methods related to US-CERT AA21-321A (Iranian Threat Actors)
- #6811 – Pre-execution phase of MicrosoftOutLookUpdater malware (Host-Level)
- #6812 – Write MicrosoftOutLookUpdater malware to disk (Host-Level)
- #6813 – Transfer of MicrosoftOutLookUpdater malware over HTTP/S (Lateral Movement)
- #6814 – Transfer of MicrosoftOutLookUpdater malware over HTTP/S (Infiltration)
- #6815 – Email MicrosoftOutLookUpdater malware as a ZIP attachment (Lateral Movement)
- #6816 – Email MicrosoftOutLookUpdater malware as a ZIP attachment (Infiltration)
- #6817 – Pre-execution phase of winPEAS malware (Host-Level)
- #6818 – Write winPEAS malware to disk (Host-Level)
- #6819 – Transfer of winPEAS malware over HTTP/S (Lateral Movement)
- #6820 – Transfer of winPEAS malware over HTTP/S (Infiltration)
- #6821 – Email winPEAS malware as a ZIP attachment (Lateral Movement)
- #6822 – Email winPEAS malware as a ZIP attachment (Infiltration)
We would also like to highlight that existing SafeBreach customers already had a certain level of protection against these attacks as the Hacker’s Playbook already included many (13) of the tactics, techniques, and procedures (TTPs) preferred by the Iranian APT groups (including the ones being reused for the current attacks). These attacks can be seen below:
- #103 – Data asset exfiltration using FTP STOR (ASCII)
- #104 – Data asset exfiltration using FTP STOR (Binary)
- #1269 – Creating Windows schedule task (schtasks)
- #130 – Data asset exfiltration over TFTP
- #2164 – Scheduled Task
- #2170 – Create Account (Windows)
- #2189 – Account Manipulation
- #2389 – Add a Firewall Rule using netsh.exe
- #5567 – Path Traversal of Fortigate VPN vulnerability CVE-2018-13379
- #6576 – Remote exploitation of Microsoft Exchange ProxyShell vulnerability CVE-2021-34473
- #794 – Extract Login Information using MimiKatz
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #2273 – Pass the Hash over SMB using Mimikatz
What you should do now
The newly updated and existing attack methods for US-CERT Alert AA21-321A (Iranian Threat Actors) are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA21-321A (Iranian Threat Actors) report and select Run Simulations which will run all attack methods.
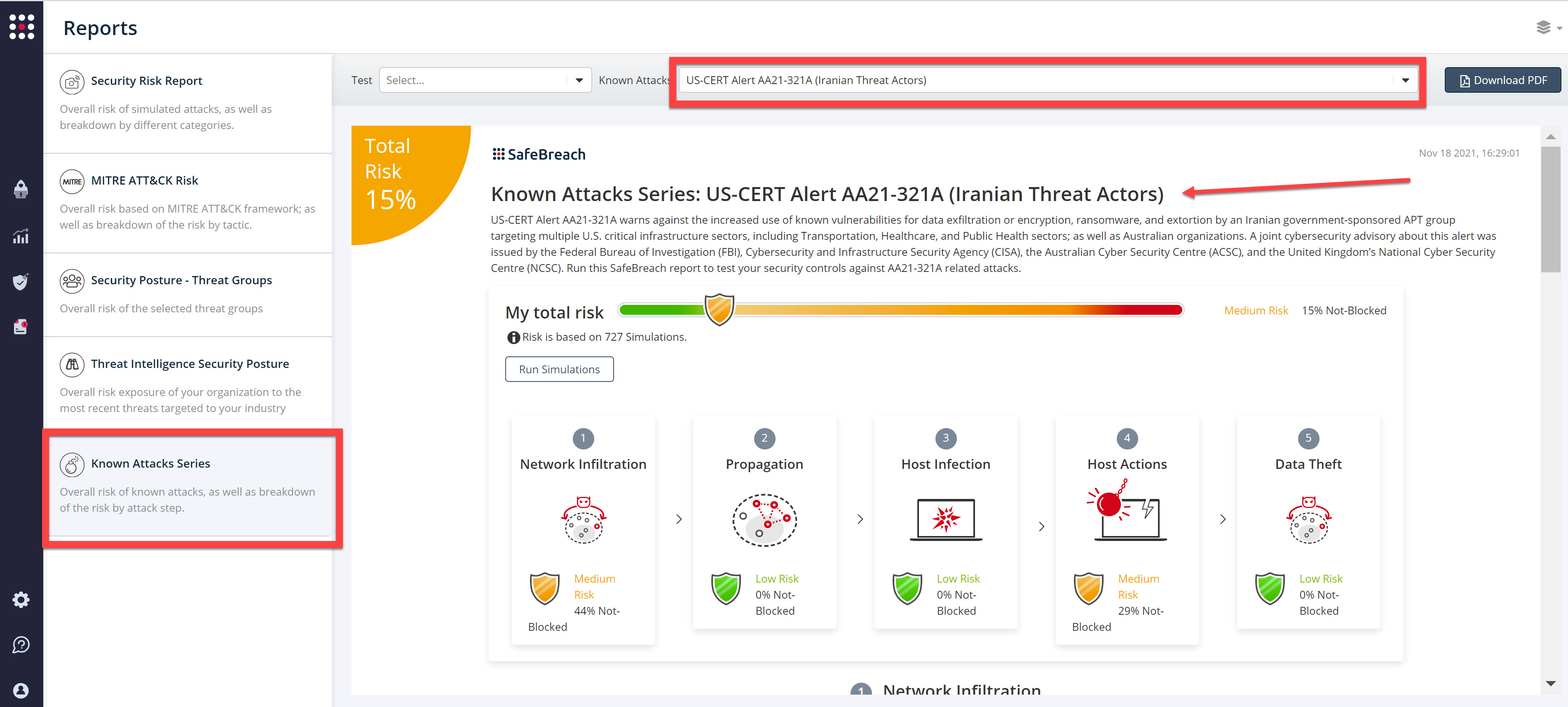
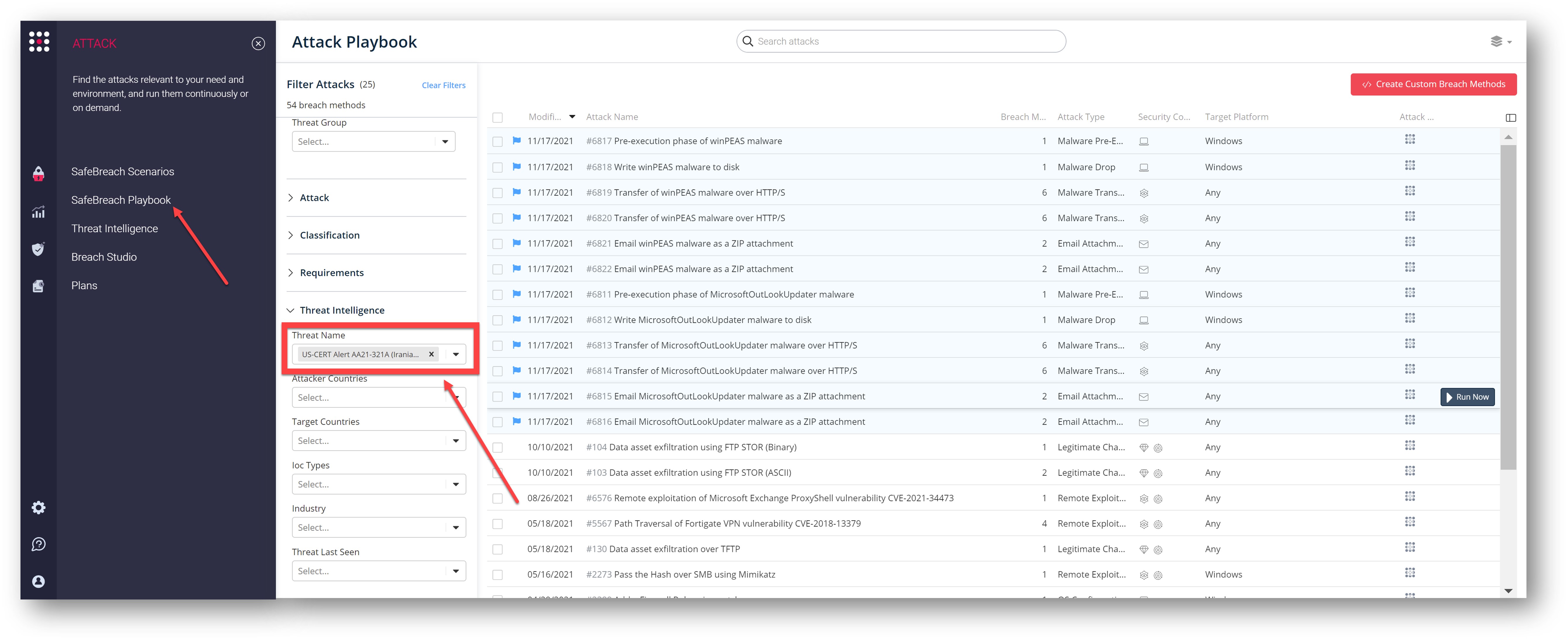
You can also select all the attacks related to US-CERT Alert AA21-321A (Iranian Threat Actors), by going to the SafeBreach Playbook and filtering by Threat Name – US-CERT Alert AA21-321A (Iranian Threat Actors)
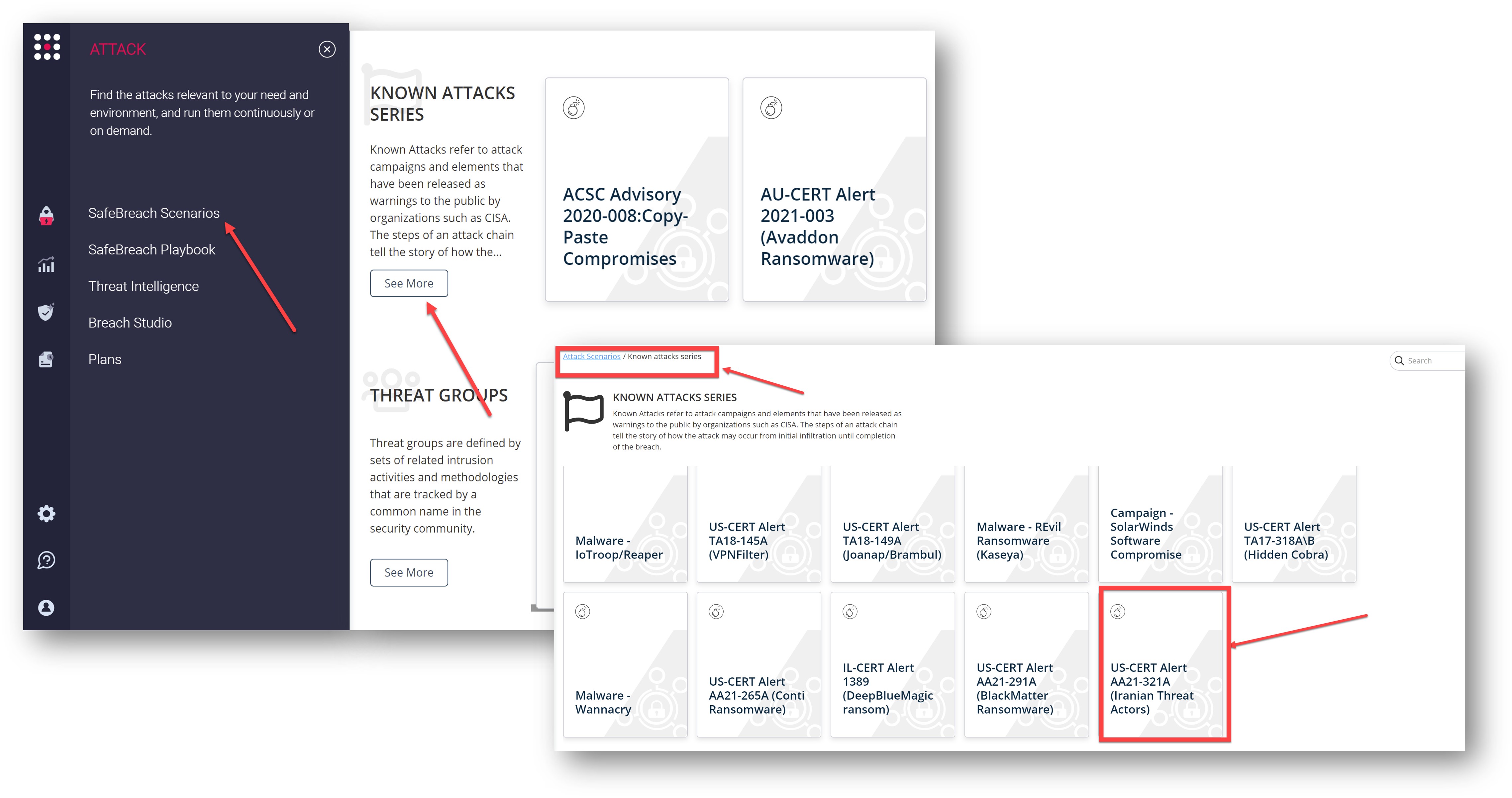
or you can go to the “SafeBreach Scenarios” page, scroll to the “Known Attack Series” and choose the US-CERT Alert AA21-321A (Iranian Threat Actors) scenario from the list of available scenarios.
NOTE – CISA, FBI, ACSC, and NCSC also recommend the following mitigations to secure your organization against Iranian state-sponsored malicious cyber activity:
- Immediately patch software affected by the following vulnerabilities: CVE-2021-34473, 2018-13379, 2020-12812, and 2019-5591.
- Implement multi-factor authentication.
- Use strong, unique passwords.