SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for the Kaseya VSA Ransomware attack including ransomware samples, domains, and URLs described in the CISA-FBI Guidance for MSPs and their Customers Affected by the Kaseya VSA Supply-Chain Ransomware Attack which addresses a global supply-chain ransomware attack against multiple managed service providers (MSPs) and their customers. This campaign leveraged a vulnerability in the Kaseya VSA (Virtual System/Server Administrator) software that allowed the attackers to take control of the affected MSPs remote management tool and deploy a REvil ransomware launcher to encrypt the victim systems of its clients.
News of this ransomware attack broke before the start of the July 4th holiday weekend and details of its potential impact will only become evident as companies resume business on Tuesday, July 6th.
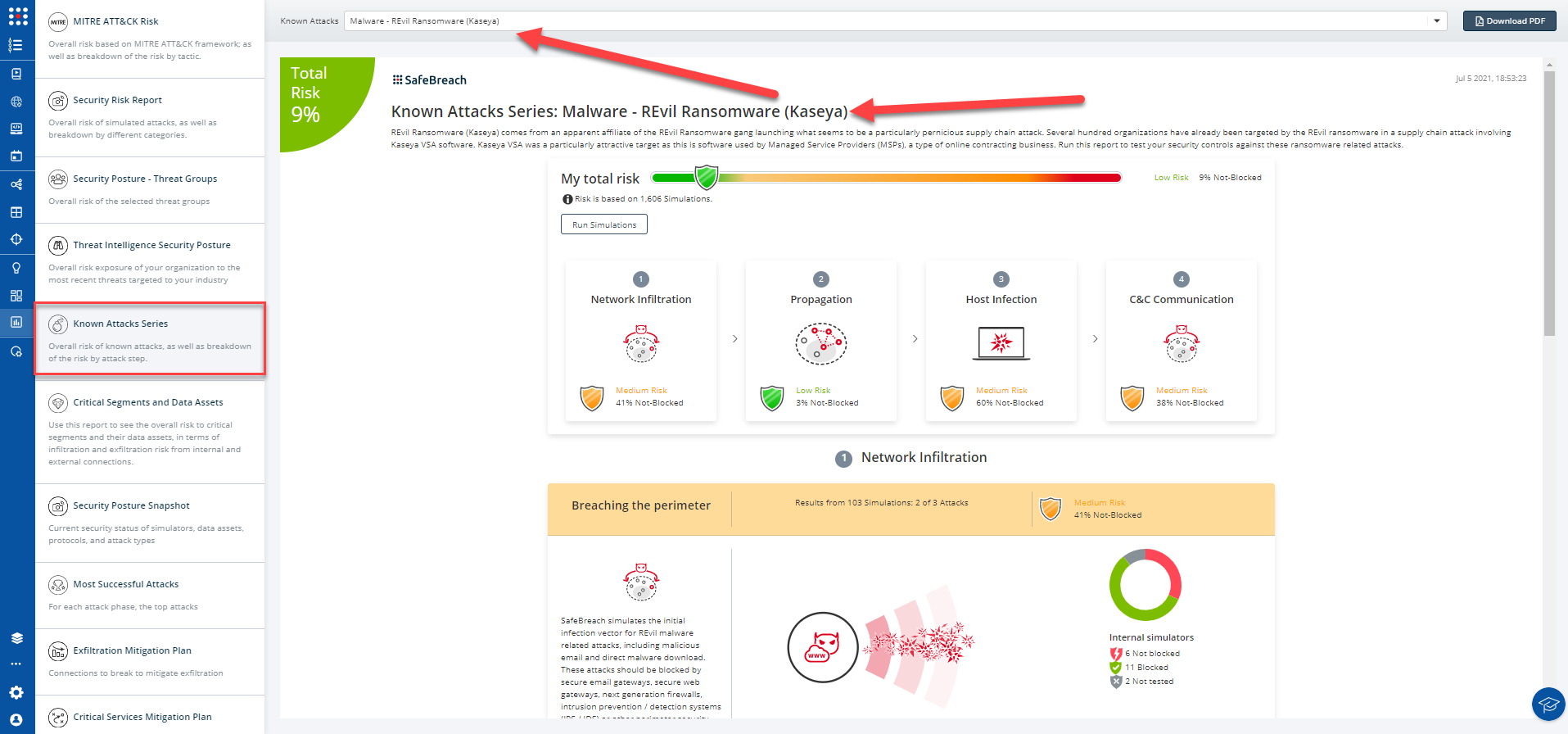
8 newly developed playbook methods related to CISA-FBI Advisory Re: Kaseya VSA Ransomware Attack
Infiltration
- #6486 – Communication with REvil_Kaseya using HTTP
- #6487 – Communication with a real malicious REvil_Kaseya server using HTTP/S
- #6490 – Transfer of REvil_Kaseya malware over HTTP/S
- #6492 – Email REvil_Kaseya malware as a ZIP attachment
- #6493 – Remote Exploitation of Kaseya VSA
Lateral Movement
- #6489 – Transfer of REvil_Kaseya malware over HTTP/S
- #6491 – Email REvil_Kaseya malware as a ZIP attachment
Host-Level
- #6488 – Write REvil_Kaseya malware to disk
6 existing playbook methods related to CISA-FBI Advisory Re: Kaseya VSA Ransomware Attack
Host-Level
- #4112 – Write REvil/Sodinokibi malware to disk
- #4113 – Execute the REvil/Sodinokibi ransomware
Infiltration
- #4116 – Transfer of REvil/Sodinokibi malware over HTTP/S
- #4118 – Email REvil/Sodinokibi malware as a ZIP attachment
Lateral Movement
- #4115 – Transfer of REvil/Sodinokibi malware over HTTP/S
- #4117– Email REvil/Sodinokibi malware as a ZIP attachment
What you should do now
The new attack methods for CISA-FBI Advisory Re: Kaseya VSA Ransomware Attack are already in the SafeBreach Hacker’s playbook and ready to be run across your simulators. The Known Attack Series report is updated so you can run the specific attacks from this US-CERT alert. From the Known Attack Series report, select the Malware – REvil Ransomware (Kaseya) report and select Run Simulations which will run all attack methods.