On July 6th, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Canadian Centre for Cyber Security (CCCS) released an advisory highlighting the newly identifying Truebot malware variants. Truebot (also known as Silence Downloader) is a botnet that has been used by the CL0P ransomware gang to collect and exfiltrate stolen target victim information. Detailed information is listed in US-CERT Alert AA23-187A – Increased Truebot Activity Infects U.S. and Canada-Based Networks.
According to the advisory, newer Truebot variants have been exploiting CVE-2022-31199 to gain initial access to victim networks. CVE-2022-31199 is a remote code execution (RCE) vulnerability in the Netwrix Auditor application. By exploiting this vulnerability, threat actors can deploy the Truebot malware at scale in victim networks. Based on the current information available, threat actors are leveraging previously used phishing campaigns (with malicious hyperlink redirects) in addition to exploiting the above-listed vulnerability to deliver the newer malware variants.
Technical Details
TrueBot is a malware downloader linked to the Russian-speaking Silence cybercrime group and used by TA505 hackers (associated with the FIN11 group) to deploy Clop ransomware on compromised networks since December 2022. Traditionally, threat actors have leveraged phishing to trick users into clicking a malicious link that downloads Truebot malware on their systems. Additionally, it has also been observed that threat actors are very adept at hiding the Truebot malware within legitimate-looking file formats.
The newly discovered Truebot variants have been delivered by exploiting a RCE vulnerability (CVE-2022-31199) in Netwrix Auditor – a tool used for IT system auditing. Exploiting this vulnerability allows the attackers to gain an initial foothold within victim networks and move laterally within the compromised network. Once the Truebot file is successfully delivered/ downloaded on the victim network, Truebot renames itself and loads FlawedGrace – a remote access trojan (RAT) onto the network. FlawedGrace is able to modify registry and print spooler programs that control the order that documents are loaded to a print queue. FlawedGrace manipulates these features to both escalate privilege and establish persistence.
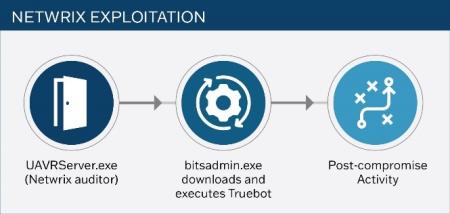
Picture Credit – CISA Advisory
During FlawedGrace’s execution phase, the RAT stores encrypted payloads inside the Windows registry. This tool can create tasks and inject payloads into command processes that allow FlawedGrace to setup command and control (C&C) and inject dynamic link libraries (DLLs) to escalate attacker privileges. Post initial access, Truebot has been observed injecting Cobalt Strike beacons into Windows memory.
During the first stage of Truebot’s execution process, it checks the current version of the operating system (OS) and processor architecture allowing it to enumerate all running processes, collect sensitive local host data, and send this data to an encoded data string for second-stage execution. Truebot also has the ability to discover software security protocols and system time metrics, which aids in defense evasion, as well as enables synchronization with the compromised system’s internal clock to facilitate scheduling tasks. A unique 13-character globally unique identifier (GUID) is also created to label and organize the collected data.
Following Truebot’s enumeration of running processes and tools, the affected system’s computer and domain name, and GUID are sent to a hard coded URL via a POST request. The POST request functions as means for establishing a C2 connection for bi-lateral communication. With this established connection, Truebot uses a second obfuscated domain to receive additional payloads, self-replicate across the environment, and/or delete files used in its operations. Truebot has been observed associated with the following delivery vectors and tools –
- Raspberry Robin malware – one of the largest malware distribution platforms
- FlawedGrace – a RAT that can receive incoming commands from a C2 server sent over a custom binary protocol
- Cobalt Strike – popular remote access tool (RAT) that has been used for persistence and exfiltration
- Teleport – custom data exfiltration tool that is known to evade detection during data exfiltration
Important Note for SafeBreach Customers – Coverage for AA23-187A (Truebot)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers already had a wide amount of coverage against the IOCs and TTPs being leveraged by the threat actors. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
Existing IOC-Based Attacks Related to Truebot
- #7973 – Write TrueBot malware to disk
- #7974 – Transfer of TrueBot malware over HTTP/S
- #7975 – Transfer of TrueBot malware over HTTP/S
- #7976 – Email TrueBot malware as a compressed attachment
- #7977 – Email TrueBot malware as a compressed attachment
- #8814 – Write TrueBot (c0f8ae) downloader to disk
- #8815 – Transfer of TrueBot (c0f8ae) downloader over HTTP/S
- #8816 – Transfer of TrueBot (c0f8ae) downloader over HTTP/S
- #8817 – Email TrueBot (c0f8ae) downloader as a compressed attachment
- #8818 – Email TrueBot (c0f8ae) downloader as a compressed attachment
- #8950 – Write Truebot (0e3a14) downloader to disk
- #8951 – Transfer of Truebot (0e3a14) downloader over HTTP/S
- #8952 – Transfer of Truebot (0e3a14) downloader over HTTP/S
- #8953 – Email Truebot (0e3a14) downloader as a compressed attachment
- #8954 – Email Truebot (0e3a14) downloader as a compressed attachment
- #7968 – Write Raspberry Robin worm malware to disk
- #7969 – Transfer of Raspberry Robin worm malware over HTTP/S
- #7970 – Transfer of Raspberry Robin worm malware over HTTP/S
- #7971 – Email Raspberry Robin worm malware as a compressed attachment
- #7972 – Email Raspberry Robin worm malware as a compressed attachment
- #8819 – Write Cobalt Strike Beacon hacktool to disk
- #8820 – Transfer of Cobalt Strike Beacon hacktool over HTTP/S
- #8821 – Transfer of Cobalt Strike Beacon hacktool over HTTP/S
- #8822 – Email Cobalt Strike Beacon hacktool as a compressed attachment
- #8823 – Email Cobalt Strike Beacon hacktool as a compressed attachment
- #2598 – Write flawedgrace malware to disk
- #2599 – Transfer of flawedgrace malware over HTTP/S
- #2600 – Transfer of flawedgrace malware over HTTP/S
- #2601 – Email flawedgrace malware as a compressed attachment
- #2602 – Email flawedgrace malware as a compressed attachment
- #3141 – Pre-execution phase of flawedgrace malware
Existing Behavioral Attacks Related to Truebot
- #8364 – Load custom shared module via LoadLibrary
- #7001 – Install a print processor
- #8363 – Print spoofer privilege escalation
- #7818 – Pre-execution phase of a malicious large file (Windows)
- #7220 – Process Injection – Thread Execution Hijacking
- #8359 – Process Injection – Asynchronous Procedure Calls
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials
- #3819 – Windows Credentials Collection using LaZagne
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32
- #6514 – Carbanak UAC Bypass and Credential Dumping
- #794 – Extract Login Information using MimiKatz
- #8371 – In memory credential extraction via MiniDumpWriteDump and handle hijacking
- #8370 – In memory credential extraction via MiniDumpWriteDump
- #1693 – Collect Windows system data using CMD
- #6872 – Discover macOS network configuration using Bash
- #811 – Discover Linux network configuration using Bash
- #2217 – Discover the system time using net time command (Windows)
- #1269 – Creating Windows schedule task (schtasks.exe)
- #6479 – Simulate the SocGholish dropper with pre-execution of malicious malware
- #240 – Upload File over SMB
- #2188 – Extract Process List using Windows Commands
- #7213 – Debugger Evasion (Windows)
- #2273 – Pass the Hash over SMB using Mimikatz
- #6411 – Screen Capture (Windows)
- #8004 – Capture Screen using Powershell
- #3829 – Run obfuscated Mimikatz on hos
- #6473 – Agentless lateral movement via RDP
- #214 – Scheduled task creation over SMB
- #2164 – Scheduled Task
Note – Since the US-CERT does not explicitly state exfiltration techniques used for the Truebot campaign, you can leverage all available exfiltration techniques from the Hacker’s Playbook to validate your security controls.
Newly Added Attacks
- #9014 – Write TrueBot UPX (be821f) rat to disk
- #9015 – Pre-execution phase of TrueBot UPX (be821f) rat (Windows)
- #9016 – Transfer of TrueBot UPX (be821f) rat over HTTP/S
- #9017 – Transfer of TrueBot UPX (be821f) rat over HTTP/S
- #9018 – Email TrueBot UPX (be821f) rat as a compressed attachment
- #9019 – Email TrueBot UPX (be821f) rat as a compressed attachment
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
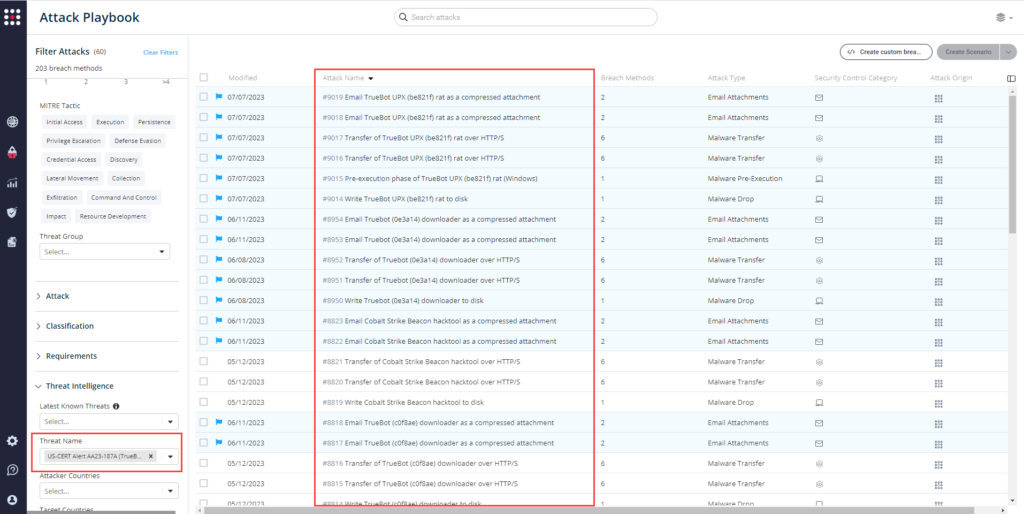
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-187A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
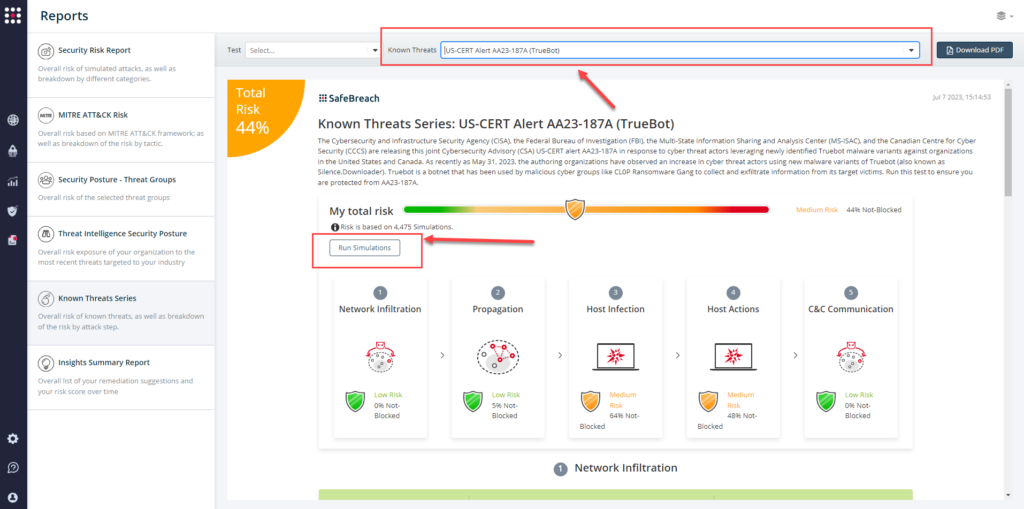
From the Known Attack Series report, select the AA23-187A (Truebot) report and select Run Simulations which will run all attack methods.
You can also go to the “SafeBreach Scenarios” page and choose the AA23-187A (Truebot) scenario from the list of available scenarios.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Apply patches to CVE-2022-31199
- Update Netwrix Auditor to version 10.5.
- Implement filters at the email gateway to filter out emails with known malicious indicators.
- Implement application controls to manage and control execution of software, including allowlisting remote access programs.
- Strictly limit the use of RDP and other remote desktop services.
- Disable command-line and scripting activities and permissions
- Update Windows PowerShell or PowerShell Core to the latest version and uninstall all earlier PowerShell versions.
- For detailed information about mitigations and incident response, please refer to the full advisory

