On February 19, 2025, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint advisory to disseminate known Ghost (Cring)—(“Ghost”)—ransomware IOCs and TTPs identified through FBI investigation as recently as January 2025. Detailed information about this threat and the associated IOCs and TTPs can be seen in the advisory #StopRansomware: Ghost (Cring) Ransomware.
This blog will share an overview of the threat and our coverage for these threat actors. As a SafeBreach customer, you will have access to all the attacks listed below and more to validate your organizational security controls against this threat.
US CERT Alert AA25-050A [Ghost (Cringe) Ransomware]
Beginning in early 2021, Ghost actors began attacking victims whose Internet-facing services ran outdated versions of software and firmware. This indiscriminate targeting of networks containing vulnerabilities has led to the compromise of organizations across more than 70 countries, including organizations in China. Ghost actors, located in China, conduct these widespread attacks for financial gain. Affected victims include critical infrastructure, schools and universities, healthcare, government networks, religious institutions, technology and manufacturing companies, and numerous small- and medium-sized businesses.
Ghost actors rotate their ransomware executable payloads, switch file extensions for encrypted files, modify ransom note text, and use numerous ransom email addresses, which has led to variable attribution of this group over time. Names associated with this group include Ghost, Cring, Crypt3r, Phantom, Strike, Hello, Wickrme, HsHarada, and Rapture. Samples of ransomware files Ghost used during attacks are: Cring.exe, Ghost.exe, ElysiumO.exe, and Locker.exe.
Ghost actors use publicly available code to exploit Common Vulnerabilities and Exposures (CVEs) and gain access to Internet-facing servers. Ghost actors exploit well-known vulnerabilities and target networks where available patches have not been applied.
Technical Details
Initial Access – According to the information available, the FBI has observed Ghost actors obtaining initial access to networks by exploiting public-facing applications that are associated with multiple CVEs [T1190]. Their methodology includes leveraging vulnerabilities in Fortinet FortiOS appliances (CVE-2018-13379), servers running Adobe ColdFusion (CVE-2010-2861 and CVE-2009-3960), Microsoft SharePoint (CVE-2019-0604), and Microsoft Exchange (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207— commonly referred to as the ProxyShell attack chain).
Execution – Ghost actors have been observed uploading a web shell [T1505.003] to a compromised server and leveraging Windows Command Prompt [T1059.003] and/or PowerShell [T1059.001] to download and execute Cobalt Strike Beacon malware [T1105] that is then implanted on victim systems. Despite Ghost actors’ malicious implementation, Cobalt Strike is a commercially available adversary simulation tool often used for the purposes of testing an organization’s security controls.
Persistence – Persistence is not a major focus for Ghost actors, as they typically only spend a few days on victim networks. In multiple instances, they have been observed proceeding from initial compromise to the deployment of ransomware within the same day. However, Ghost actors sporadically create new local [T1136.001] and domain accounts [T1136.002] and change passwords for existing accounts [T1098]. In 2024, Ghost actors were observed deploying web shells [T1505.003] on victim web servers.
Privilege Escalation – Ghost actors often rely on built-in Cobalt Strike functions to steal process tokens running under the SYSTEM user context to impersonate the SYSTEM user, often for the purpose of running Beacon a second time with elevated privileges [T1134.001]. Ghost actors have been observed using multiple open-source tools in an attempt at privilege escalation through exploitation [T1068] such as “SharpZeroLogon,” “SharpGPPPass,” “BadPotato,” and “GodPotato.” These privilege escalation tools would not generally be used by individuals with legitimate access and credentials.
Credential Access – Ghost actors use the built-in Cobalt Strike function “hashdump” or Mimikatz [T1003] to collect passwords and/or password hashes to aid them with unauthorized logins and privilege escalation or to pivot to other victim devices.
Defense Evasion – Ghost actors used their access through Cobalt Strike to display a list of running processes [T1057] to determine which antivirus software [T1518.001] is running so that it can be disabled [T1562.001]. Ghost frequently runs a command to disable Windows Defender on network connected devices. Options used in this command are: Set-MpPreference -DisableRealtimeMonitoring 1 -DisableIntrusionPreventionSystem 1 -DisableBehaviorMonitoring 1 -DisableScriptScanning 1 -DisableIOAVProtection 1 -EnableControlledFolderAccess Disabled -MAPSReporting Disabled -SubmitSamplesConsent NeverSend.
Discovery – Ghost actors have been observed using other built-in Cobalt Strike commands for domain account discovery [T1087.002], open-source tools such as “SharpShares” for network share discovery [T1135] and “Ladon 911” and “SharpNBTScan” for remote systems discovery [T1018]. Network administrators would be unlikely to use these tools for network share or remote systems discovery.
Lateral Movement – Ghost actors used elevated access and Windows Management Instrumentation Command-Line (WMIC) [T1047] to run PowerShell commands on additional systems on the victim network— often for the purpose of initiating additional Cobalt Strike Beacon infections. The associated encoded string is a base 64 PowerShell command that always begins with:
powershell -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgA
EkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA
6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIA… [T1132.001][T1564.003].
This string decodes to “$s=New-Object IO.MemoryStream(,[Convert]::FromBase64String(“” and is involved with the execution of Cobalt Strike in memory on the target machine. In cases where lateral movement attempts are unsuccessful, Ghost actors have been observed abandoning an attack on a victim.
Exfiltration – Ghost ransom notes often claim exfiltrated data will be sold if a ransom is not paid. However, Ghost actors do not frequently exfiltrate a significant amount of information or files, such as intellectual property or personally identifiable information (PII), that would cause significant harm to victims if leaked. The FBI has observed limited downloading of data to Cobalt Strike Team Servers [T1041]. Victims and other trusted third parties have reported limited uses of Mega.nz [T1567.002] and installed web shells for similar limited data exfiltration. Note: The typical data exfiltration is less than hundreds of gigabytes of data.
Command & Control – Ghost actors rely heavily on Cobalt Strike Beacon malware and Cobalt Strike Team Servers for command and control (C2) operations, which function using hypertext transfer protocol (HTTP) and hypertext transfer protocol secure (HTTPS) [T1071.001]. Ghost rarely registers domains associated with their C2 servers. Instead, connections made to a uniform resource identifier (URI) of a C2 server, for the purpose of downloading and executing Beacon malware, directly reference the C2 server’s IP address. For example, http://xxx.xxx.xxx.xxx:80/Google.com where xxx.xxx.xxx.xxx represents the C2 server’s IP address. For email communication with victims, Ghost actors use legitimate email services that include traffic encryption features. [T1573] Some examples of emails services that Ghost actors have been observed using are Tutanota, Skiff, ProtonMail, Onionmail, and Mailfence.
Impact & Encryption – Ghost actors use Cring.exe, Ghost.exe, ElysiumO.exe, and Locker.exe, which are all ransomware executables that share similar functionality. Ghost variants can be used to encrypt specific directories or the entire system’s storage [T1486]. The nature of executables’ operability is based on command line arguments used when executing the ransomware file. Various file extensions and system folders are excluded during the encryption process to avoid encrypting files that would render targeted devices inoperable. These ransomware payloads clear Windows Event Logs [T1070.001], disable the Volume Shadow Copy Service, and delete shadow copies to inhibit system recovery attempts [T1490]. Data encrypted with Ghost ransomware variants cannot be recovered without the decryption key. Ghost actors hold the encrypted data for ransom and typically demand anywhere from tens to hundreds of thousands of dollars in cryptocurrency in exchange for decryption software [T1486]. The impact of Ghost ransomware activity varies widely on a victim-to-victim basis. Ghost actors tend to move to other targets when confronted with hardened systems, such as those where proper network segmentation prevents lateral movement to other devices.
Important Note for SafeBreach Customers – Coverage for AA25-050A [Ghost (Cringe) Ransomware]
As soon as details were made available, the SafeBreach Labs teams added attacks based on the advisory and mapped existing attacks in the Hacker’s Playbook to these US-CERT alerts immediately. It is important to note that existing SafeBreach customers already had a good level of coverage against tactics and techniques previously leveraged by the ransomware group identified in the advisory. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs.
New IOC-Based Attacks Related to US CERT Alert AA25-050A [Ghost (Cringe) Ransomware]
SharpShares
- #10707 – Write SharpShares (bc6f41) hacktool to disk
- #10708 – Pre-execution phase of SharpShares (bc6f41) hacktool (Windows)
- #10709 – Transfer of SharpShares (bc6f41) hacktool over HTTP/S
- #10710 – Transfer of SharpShares (bc6f41) hacktool over HTTP/S
- #10711 – Email SharpShares (bc6f41) hacktool as a compressed attachment
- #10712 – Email SharpShares (bc6f41) hacktool as a compressed attachment
GodPotato
- #10713 – Write GodPotato (352a28) hacktool to disk
- #10714 – Pre-execution phase of GodPotato (352a28) hacktool (Windows)
- #10715 – Transfer of GodPotato (352a28) hacktool over HTTP/S
- #10716 – Transfer of GodPotato (352a28) hacktool over HTTP/S
- #10717 – Email GodPotato (352a28) hacktool as a compressed attachment
- #10718 – Email GodPotato (352a28) hacktool as a compressed attachment
Cringe
- #10719 – Write Cring (5511c8) ransomware to disk
- #10720 – Pre-execution phase of Cring (5511c8) ransomware (Windows)
- #10721 – Transfer of Cring (5511c8) ransomware over HTTP/S
- #10722 – Transfer of Cring (5511c8) ransomware over HTTP/S
- #10723 – Email Cring (5511c8) ransomware as a compressed attachment
- #10724 – Email Cring (5511c8) ransomware as a compressed attachment
Elysium
- #10725 – Write Elysium (36b5c8) ransomware to disk
- #10726 – Pre-execution phase of Elysium (36b5c8) ransomware (Windows)
- #10727 – Transfer of Elysium (36b5c8) ransomware over HTTP/S
- #10728 – Transfer of Elysium (36b5c8) ransomware over HTTP/S
- #10729 – Email Elysium (36b5c8) ransomware as a compressed attachment
- #10730 – Email Elysium (36b5c8) ransomware as a compressed attachment
Existing IOC-Based Attacks Related to US CERT Alert AA25-050A [Ghost (Cringe) Ransomware]
- 5718 – Pre-execution phase of SharpZeroLogon trojan
- 5719 – Write SharpZeroLogon trojan to disk
- 5720 – Transfer of SharpZeroLogon trojan over HTTP/S
- 5721 – Transfer of SharpZeroLogon trojan over HTTP/S
- 5722 – Email SharpZeroLogon trojan as a compressed attachment
- 5723 – Email SharpZeroLogon trojan as a compressed attachment
Existing Behavioral Attacks Related to US CERT Alert AA25-050A [Ghost (Cringe) Ransomware]
- #794 – Extract Login Information using MimiKatz
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials (lateral movement)
- #1693 – Collect Windows system data using CMD
- #2188 – Extract Process List using Windows Commands
- #2170 – Create Account (Windows)
- #2174 – Extract users and groups using net.exe (Windows)
- #2189 – Account Manipulation
- #2192 – Collect Data from Local Shared Drives using System Commands
- #2206 – Extract Security Packages using PowerShell
- #2222 – Discover Remote Systems using PowerShell
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #2273 – Pass the Hash over SMB using Mimikatz (lateral movement)
- #2335 – Collect and Enumerate Domain Controller Shares using PowerView (PowerShell)
- #2336 – Collect and Enumerate Domain Computers Shares using PowerView (PowerShell)
- #3829 – Run obfuscated Mimikatz on host
- #5107 – Stop a service using net stop command
- #5672 – Agentless lateral movement via WMI
- #5673 – Agentless lateral movement via Remote PowerShell (WMI)
- #5833 – Extract Login Information using MimiKatz DCSync
- #6372 – Modify Volume Shadow Copy (VSS)
- #6513 – Agentless lateral movement via SMB and RCE, using Mimikatz
- #6578 – Discover domain users using LDAP method
- #6801 – Credential harvesting using Mimikatz DCSync with interactive session token
- #6802 – Credential harvesting using Mimikatz DCSync with user credentials
- #6807 – Extract credentials from ntds.dit file using volume shadow copy
- #7144 – Unregister anti malware scanning interface providers
- #7169 – Dump the SAM database from the registry (Windows)
- #7170 – Add a local administrator (Windows)
- #7172 – Spawn a hidden Powershell process
- #7173 – Spawn a hidden process (Windows)
- #7834 – Add Exclusions to Windows Defender
- #7835 – Disable Windows Defender From Registry
- #8363 – Print spoofer privilege escalation
- #8857 – Add Mimikatz as exclusion to Windows Defender and execute Mimikatz
- #9456 – Extract SAM credentials from registry
- #10336 – Extract Programs List using Windows Commands
- #10339 – Collect information about antivirus products using CMD
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
Method 1
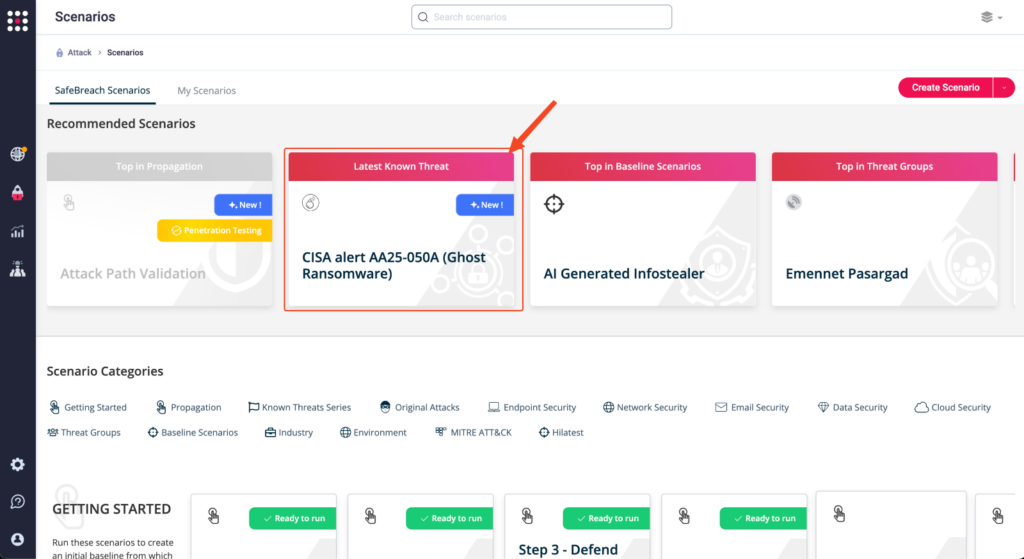
You can go to the “SafeBreach Scenarios” page and choose AA254-050A [Ghost (Cring) Ransomware].
Method 2
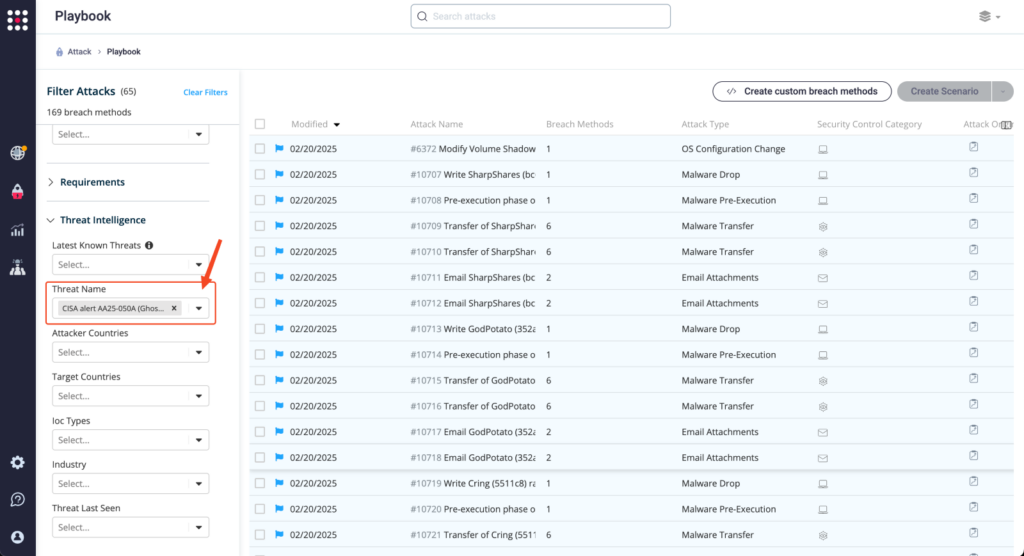
From the Attack Playbook, select and filter attacks related to AA254-050A [Ghost (Cring) Ransomware]. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
Method 3
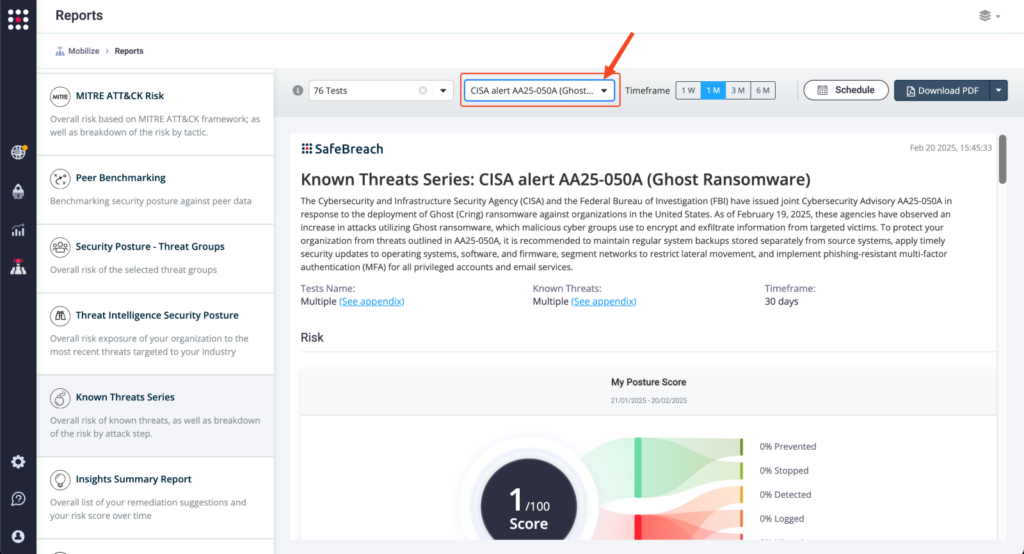
From the Known Attack Series report, select the US CERT Alert AA254-050A [Ghost (Cring) Ransomware] report and select Run Simulations, which will run all attack methods.
NOTE: The FBI and CISA recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against advanced cyber threats. Additional recommendations can be seen in the advisory (linked below):
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location Promptly patch all internet exposed devices and services, including web servers, web applications, and remote access gateways.
- Require all accounts with password logins.
- Disable unused or unnecessary network services, ports and protocols.
- Keep all operating systems, software, and firmware up to date.
- Require Phishing-Resistant multifactor authentication to administrator accounts.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- For additional recommendations, please review the advisory in detail.