The SafeBreach platform has been updated with coverage for the newly discovered Azov ransomware data wiper and LODEINFO malware. SafeBreach customers can select and run these attacks from the SafeBreach Hacker’s Playbook™ to ensure coverage against these advanced threats. Additional details about the threat and our coverage can be seen below.
Azov Ransomware Data Wiper
Azov ransomware is known to be distributed via SmokeLoader—a malicious bot application that can be used to load other malware, pirated software, key generators, and adware bundles. This data wiper scans all drives; encrypts any file that does not have .exe, .dll, and .ini extensions; and appends the .azov file extension to the encrypted filenames.
According to the ransom note, devices are encrypted in protest of Crimea’s seizure, and the threat actors purportedly claim well-known researchers and other entities are involved in the operation and to contact them for decryption. However, they do not have decryption keys, the threat actors cannot be contacted to pay the ransom, and the malware should be treated as a destructive data wiper instead of ransomware.
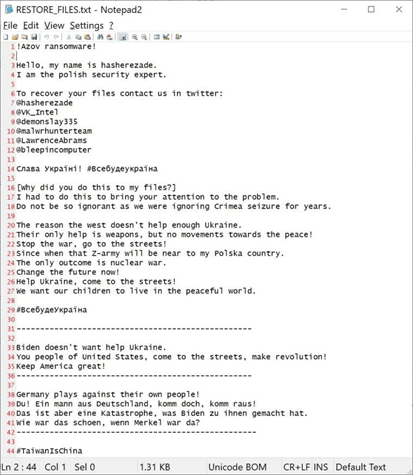
According to the information available, devices infected with Azov Ransomware had all their data corrupted upon the end of the malware’s dormancy until October 27, 2022, at 10:14:30 AM UTC. According to security researchers from Checkpoint, Azov overwrites and corrupts data in alternating 666-byte chunks—666 bytes of garbage, 666 bytes original, 666bytes of garbage, 666 bytes original, etc.
SafeBreach Coverage of Azov Ransomware
The SafeBreach platform has been updated with the following attacks to ensure our customers can validate their security controls against the new ransomware variant:
- #7998 – Pre-execution phase of Azov malware (Host-Level)
- #7999 – Write Azov malware to disk (Host-Level)
- #8000 – Transfer of Azov malware over HTTP/S (Lateral Movement)
- #8001 – Transfer of Azov malware over HTTP/S (Infiltration)
- #8002 – Email Azov malware as a ZIP attachment (Lateral Movement)
- #8003 – Email Azov malware as a ZIP attachment (Infiltration)
LODEINFO Malware
Late last month, the Chinese Cicada hacking group (also known as APT10) was noticed abusing security software to install a new variation of the LODEINFO malware against several Japanese organizations. Targets included media groups, diplomatic agencies, government/public sector entities, and think tanks—all high-value targets for cyberespionage. LODEINFO is a backdoor-type malware capable of causing chain infections and stealing sensitive information from infected devices.
Early March 2022, threat researchers from Kaspersky noticed the APT10 threat actors launching attacks in Japan with a new threat vector, including a spearphishing email, a self-extracting (SFX) RAR file, and abusing a DLL-side-loading flaw in security software. The RAR archive contains the legitimate K7Security Suite software executable, NRTOLD.exe, and a malicious DLL named K7SysMn1.dll. When NRTOLD.exe is executed, it will attempt to load the legitimate K7SysMn1.dll file that is normally included in the software suite. However, the executable does not look for the DLL in a specific folder and thus allows malware developers to create a malicious DLL using the same name as K7SysMn1.dll. If the malicious DLL is stored in the same folder as the legitimate executables, when launched, the executable will now load the malicious DLL, which contains the LODEINFO malware. As the malware is sideloaded using a legitimate security application, other security software may not detect it as malicious. Additional details about APT10’s infection chain and its evolution can be found in the reports published by Kaspersky here and here.
In June 2022, Kaspersky noticed another variant in the APT10 infection chain, using file-less downloader shellcode delivered via a password-protected Microsoft Office document carrying malicious VBA code. This time, instead of DLL side-loading, the hackers relied on the macro code to inject and load the shellcode (DOWNISSA) directly into the memory of the WINWORD.exe process.
The latest version of LODEINFO is V0.6.7 released in September 2022. APT10’s targeted attacks on Japanese entities have constantly evolved with newer attacks being able to better evade organizational defenses. The latest variants improve upon the malware’s anti-detection/anti-analysis capabilities and have streamlined functionalities.
SafeBreach Coverage of LODEINFO Malware
The SafeBreach platform has been updated with the following attacks to ensure our customers can validate their security controls against the new malware variant:
- #7948 – Write LODEINFO malware to disk
- #7949 – Transfer of LODEINFO malware over HTTP/S
- #7950 – Transfer of LODEINFO malware over HTTP/S
- #7951 – Email LODEINFO malware as a ZIP attachment
- #7952 – Email LODEINFO malware as a ZIP attachment
Interested In Protecting Against Advanced Ransomware?
SafeBreach now offers a complimentary and customized real-world ransomware assessment (RansomwareRx) that can allow you to gain unparalleled visibility into how your security ecosystem responds at each stage of the defense process. This ransomware assessment includes:
- Training – Understand the methodology around ransomware attacks, persistent threats, and malware attacks.
- Assessment – Review goals and ensure simulation connection to our management console and all configurations are complete.
- Attack Scenario – Run safe-by-design, real-world ransomware attacks across the cyber kill chain on a single device of your choice.
- Report – Receive a custom-built report that includes simulation results and actionable remediation insights.
Empower your team to understand more about ransomware attacks, methodologies, and behaviors—all through the lens of the attacker. Request your complimentary RansomwareRx assessment today.