The discovery of Log4j and Log4j2 vulnerabilities have left security teams scrambling to ensure that their critical systems aren’t potentially exposed to attackers trying to maximize damage before the vulnerabilities are fixed. The damage caused by Log4j vulnerabilities could potentially match or even exceed that caused by the SolarWinds attack.
The real impact of these vulnerabilities may not be known for years, it is critical to ensure your systems are patched and protected against these identified vulnerabilities. Nation-states and ransomware gangs are already leveraging these vulnerabilities for their nefarious objectives, including the Conti ransomware gang abusing Log4j to access VMware vCenter servers.
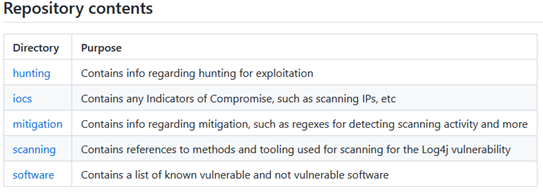
Attackers will continue exploiting the Log4J vulnerabilities before security teams can patch them. Comparing a list of vulnerable and affected software against your existing software inventory can help you prioritize your remediation efforts and effectively reduce risk. Both CISA and NCSC-NL have repositories of the affected software (see below).
As SafeBreach’s Security Services Director, I wanted to share some resources and links that can help your security teams:
Updated Vulnerability List
RMI Protocol Specs
Apache Logging – Patches
Some useful Log4j resources to keep an eye on:
US-CERT
- https://www.cisa.gov/uscert/apache-log4j-vulnerability-guidance
- https://github.com/cisagov/log4j-affected-db
NCSC-NL GitHub Repository
Log4Shell IOCs
SafeBreach’s coverage of the Log4j vulnerability and associated attacks
Log4j Coverage in Hacker’s Playbook – SafeBreach recently updated its Hacker’s Playbook™ to include the Log4j attack mechanisms identified by the Cybersecurity Infrastructure Security Agency (CISA). This coverage includes the following:
- Attack #6843 – Communication with a real malicious server exploiting CVE-2021-44228 (log4j) using LDAP.
- Attack #6844 – Communication with server vulnerable to CVE-2021-44228 (log4j) using HTTP.
- Attack #6845 – Remote exploitation of Apache Log4j vulnerability CVE-2021-44228.
Conti Ransomware TTPs – The Conti ransomware gang has become the first major threat actor to weaponize the Log4j vulnerability to target vulnerable VMware vCenter servers. The Hacker’s Playbook already includes 24 Conti ransomware attacks (including the initial access and lateral movement attacks being currently leveraged by the threat actor). Learn more here.
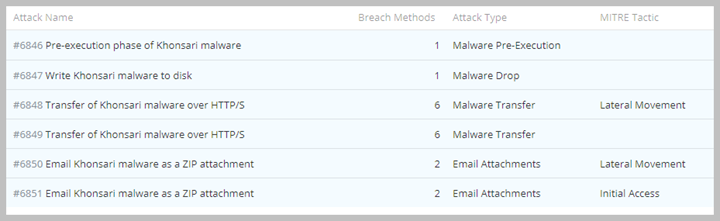
Khonsari Ransomware Coverage in Hacker’s Playbook – As soon as the news broke that attackers were actively leveraging the Log4j/Log4j2 vulnerabilities to distribute Khonsari Ransomware, the SafeBreach Research and Product teams rapidly added coverage in our playbook for attacks that leverage the Khonsari ransomware variant (see below).