On February 28th, the Symantec Threat Hunter Team (part of Broadcom software) uncovered a highly sophisticated piece of malware being used by China-linked threat actors in a global espionage campaign against select governments and other critical infrastructure targets. The Cybersecurity and Infrastructure Security Agency (CISA) has alerted organizations to review the publication Daxin: Stealthy Backdoor Designed for Attacks Against Hardened Networks for various associated technical details and IOCs related to Daxin Malware that may assist them in its detection and remediation.
According to CISA and Symantec, Daxin is a highly sophisticated rootkit backdoor with complex, stealthy command and control (C2) functionality and it has been optimized for use against hardened targets (typically of strategic interest to China), allowing the threat actors to deeply burrow into targeted networks and stealthily exfiltrate sensitive data without raising any suspicions.
Additional details about Daxin Malware
- Daxin comes in the form of a Windows kernel driver, and it implements advanced communications functionality, which both provides a high degree of stealth and permits the attackers to communicate with infected computers on highly secured networks, where direct internet connectivity is not available.
- The malware’s communication techniques are so sophisticated that its traffic can blend in unseen with normal network traffic on the target’s network. Daxin avoids starting its own network services and instead abuses any legitimate services already running on the infected computers.
- This well thought out malware is also capable of relaying its communications across a network of infected computers within the attacked organization. The attackers can select an arbitrary path across infected computers and send a single command that instructs these computers to establish requested connectivity.
- Daxin also features network tunneling, allowing attackers to communicate with legitimate services on the victim’s network that can be reached from any infected computer.
Relationship with Zala Malware
The developers of Daxin malware were already experimenting and fine-tuning techniques to be later used in Daxin with an older piece of malware – Backdoor.Zala (a.k.a Exforel). Daxin appears to build on Zala’s networking techniques, reusing a significant amount of distinctive code and even sharing certain magic constants. This is in addition to a certain public library used to perform hooking that is also common between some variants of Daxin and Zala. This indicates that Daxin designers had access to Zala’s codebase.
Newly Added SafeBreach Coverage
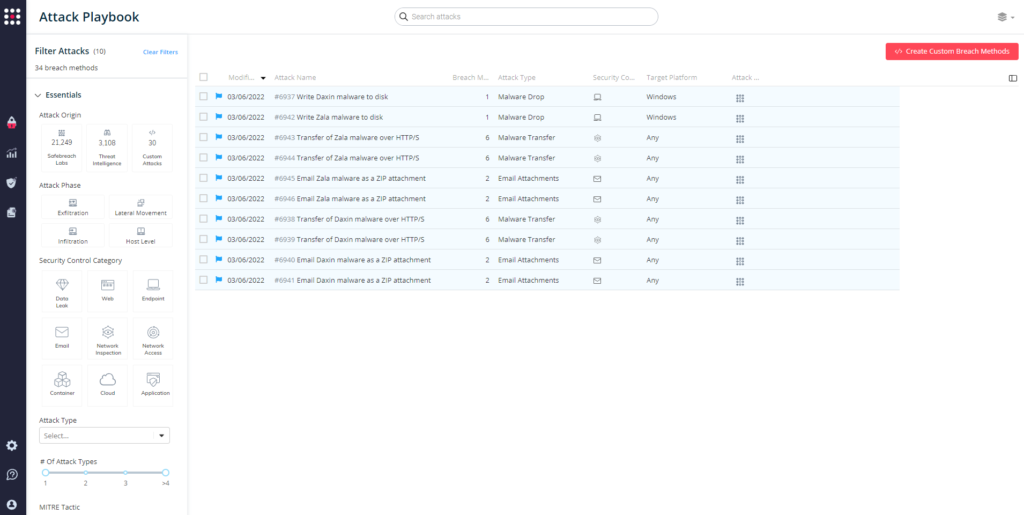
5 newly added playbook methods for Daxin Malware:
- #6937 – Write Daxin malware to disk (Host-Level)
- #6938 – Transfer of Daxin malware over HTTP/S (Lateral Movement)
- #6939 – Transfer of Daxin malware over HTTP/S (Infiltration)
- #6940 – Email Daxin malware as a ZIP attachment (Lateral Movement)
- #6941 – Email Daxin malware as a ZIP attachment (Infiltration)
5 newly added attack methods related to Zala Malware:
- #6942 – Write Zala malware to disk (Host-Level)
- #6943 – Transfer of Zala malware over HTTP/S (Lateral Movement)
- #6944 – Transfer of Zala malware over HTTP/S (Infiltration)
- #6945 – Email Zala malware as a ZIP attachment (Lateral Movement)
- #6946 – Email Zala malware as a ZIP attachment (Infiltration)
What you should do now
Attack methods related to these advanced threats have been added to the Hacker’s Playbook™ and are ready to run across your simulators. From the Attack Playbook, select and filter attacks related to Daxin and Zala (see below).