On May10th, Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC) issued an urgent advisory about malicious threat activity involving the Black Basta ransomware variant. Detailed information about these threats and the associated IOCs and TTPs can be seen on #StopRansomware: Black Basta.
This blog will share an overview of the threat and our coverage for this ransomware variant. As a SafeBreach customer, you will have access to all the attacks listed below and more to validate your organizational security controls against this advanced ransomware family.
US CERT ALERT AA24-131A – Black Basta Ransomware – What You Should Know
Threat actors have used the Black Basta ransomware variant to target, encrypt, and steal data from organizations belonging to 12 out of the 16 critical infrastructure sectors, including the Health and Public Health (HPH) sector. Black Basta was first identified in 2022 and leverages the ransomware-as-a-service (RaaS) model. According to the data available, Black Basta threat actors have targeted over 500 organizations and critical infrastructure entities across North America, Europe, and Australia. Black Basta affiliates typically target victims through phishing and exploiting known vulnerabilities in their networks. Post-infection, they expect victims to pay ransom within 10-12 days using a unique code and a .onion URL left behind in the ransom note. If victims refuse to make payment, their stolen data is published on the Black Basta TOR site.
It is believed that the Black Basta affiliates particularly target healthcare organizations due to their size, dependance on technology, access to sensitive personal information, and the impact of a ransomware attack on the organization (disruption to patient care).
Technical Details
Black Basta is believed to be one of the factions that came out of the Conti ransomware family. Since its launch in April 2022, its victims include high-profile organizations including German defense contractor Rheinmetall, Hyundai Motors (European division), U.K. technology outsourcing company Capita, industrial automation company and government contractor ABB, the Toronto Public Library, the American Dental Association, Sobeys, Knauf, and Yellow Pages Canada. Based on information available, the Black Basta ransomware affiliates are believed to have collected nearly $100 million in ransom payments from nearly 90 victims (until November 2023). A typical Black Basta ransomware attack unfolds as follows:
- Initial Access – threat actors gain access to victims through spear phishing and using Qakbot – a remote access trojan (RAT) that steals sensitive data and propagates throughout the victim networks. Information from the latest attacks reveals that threat actors have also begun exploiting the ConnectWise vulnerability (CVE-2024-1709) to bypass authentication and gain entry to victim networks, at times even using valid credentials.
- Discovery and Ransomware Execution – Once they gain access to victim networks, the threat actors have been observed using SoftPerfect scanner to perform network reconnaissance.
- Lateral Movement – Threat actors were observed leveraging tools like BITSAdmin and PsExec, along with Remote Desktop Protocol (RDP), for lateral movement. Additionally Cobalt Strike beacons, Splashtop, and Screen Connect were also used for remote access and lateral movement across victim networks.
- Privilege Escalation and Lateral Movement – Black Basta affiliates use credential scraping tools like Mimikatz for privilege escalation. Following vulnerabilities were also exploited for local Windows Active Domain privilege escalation:
- ZeroLogon – CVE-2020-1472, [CWE-330]
- NoPac (CVE-2021-42278 [CWE-20]
- PrintNightmare (CVE-2021-34527, [CWE-269]
- Data Exfiltration and Encryption – Black Basta affiliates use RClone to facilitate data exfiltration prior to encryption. They have also been observed using PowerShell to disable antivirus products, and in some instances, deploying a tool called Backstab, designed to disable endpoint detection and response (EDR) tools. Once the AV tool is disabled, a ChaCha20 algorithm with an RSA-4096 public key fully encrypts files and a ransom note titled readme.txt is left on the compromised system. To make system recovery difficult, threat actors use the vssadmin.exe program to delete volume shadow copies.
Important Note for SafeBreach Customers – Coverage for US-CERT AA24-131A
As soon as details were made available, the SafeBreach Labs teams added new attacks based on the advisory and mapped existing attacks in the Hacker’s Playbook to these US-CERT alerts immediately. It is important to note that existing SafeBreach customers already had a good level of coverage against the Black Basta ransomware variant identified in the advisories. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs.
Existing IOC-Based Playbook Attacks Related to AA24-131A
- ALL EXISTING MIMIKATZ ATTACKS
- #8080 – Write Qakbot_zip (QBot) trojan to disk
- #8081 – Transfer of Qakbot_zip (QBot) trojan over HTTP/S
- #8082 – Transfer of Qakbot_zip (QBot) trojan over HTTP/S
- #8083 – Email Qakbot_zip (QBot) trojan as a compressed attachment
- #8084 – Email Qakbot_zip (QBot) trojan as a compressed attachment
- #1359 – Transfer of the QakBot trojan over HTTP/S
- #1864 – Email the QakBot trojan as a compressed attachment
- #2066 – Email the QakBot trojan as a compressed attachment
- #8842 – Write QakBot OneNote dropper to disk
- #8843 – Transfer of QakBot OneNote dropper over HTTP/S
- #8844 – Transfer of QakBot OneNote dropper over HTTP/S
- #8845 – Email QakBot OneNote dropper as a compressed attachment
- #8846 – Email QakBot OneNote dropper as a compressed attachment
- #8085 – Write Qakbot_dll (QBot) trojan to disk
- #8086 – Transfer of Qakbot_dll (QBot) trojan over HTTP/S
- #8087 – Transfer of Qakbot_dll (QBot) trojan over HTTP/S
- #8088 – Email Qakbot_dll (QBot) trojan as a compressed attachment
- #8089 – Email Qakbot_dll (QBot) trojan as a compressed attachment
- #7176 – Write Black Basta ransomware to disk
- #7177 – Transfer of Black Basta ransomware over HTTP/S
- #7178 – Transfer of Black Basta ransomware over HTTP/S
- #7179 – Email Black Basta ransomware as a compressed attachment
- #7180 – Email Black Basta ransomware as a compressed attachment
- #9525 – Write Black Basta (949df4) ransomware to disk
- #9526 – Transfer of Black Basta (949df4) ransomware over HTTP/S
- #9527 – Transfer of Black Basta (949df4) ransomware over HTTP/S
- #9528 – Email Black Basta (949df4) ransomware as a compressed attachment
- #9529 – Email Black Basta (949df4) ransomware as a compressed attachment
NEW IOC-Based Playbook Attacks Related to AA24-131A
- #10130 – Write Black Basta (53e94a) ransomware to disk
- #10131 – Pre-execution phase of Black Basta (53e94a) ransomware (Windows)
- #10132 – Transfer of Black Basta (53e94a) ransomware over HTTP/S
- #10133 – Transfer of Black Basta (53e94a) ransomware over HTTP/S
- #10134 – Email Black Basta (53e94a) ransomware as a compressed attachment
- #10135 – Email Black Basta (53e94a) ransomware as a compressed attachment
- #10136 – Write Black Basta (8980bc) ransomware to disk
- #10137 – Pre-execution phase of Black Basta (8980bc) ransomware (Windows)
- #10138 – Transfer of Black Basta (8980bc) ransomware over HTTP/S
- #10139 – Transfer of Black Basta (8980bc) ransomware over HTTP/S
- #10140 – Email Black Basta (8980bc) ransomware as a compressed attachment
- #10141 – Email Black Basta (8980bc) ransomware as a compressed attachment
Existing Behavioral Attacks Related to AA24-131A
- ALL EXISTING RANSOMWARE ATTACKS
- #1355 – Transfer of data over BITS protocol
- #1339 – Remote command execution by PSExec
- #2267 – Add an exclusion to Windows Defender using PowerShell
- #5487 – Exploit CVE-2020-1472 ZeroLogon
- #6246 – Exploit ZeroLogon (CVE-2020-1472) (Windows)
- #6372 – Modify Volume Shadow Copy (VSS)
- #6482 – Remote Code Execution via CVE-2021-34527 (PrintNightmare)
- #6473 – Agentless lateral movement via RDP
- #6483 – Agentless lateral movement via SMB and RCE, using Token duplication
- #6513 – Agentless lateral movement via SMB and RCE, using Mimikatz
- #6550 – Agentless lateral movement via SMB and RCE, using Impersonated user
- #6909 – RDP Connection Between 2 Simulators
- #6910 – RDP Tunneling
- #7144 – Unregister anti malware scanning interface providers
- #7834 – Add Exclusions to Windows Defender
- #7835 – Disable Windows Defender from Registry
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
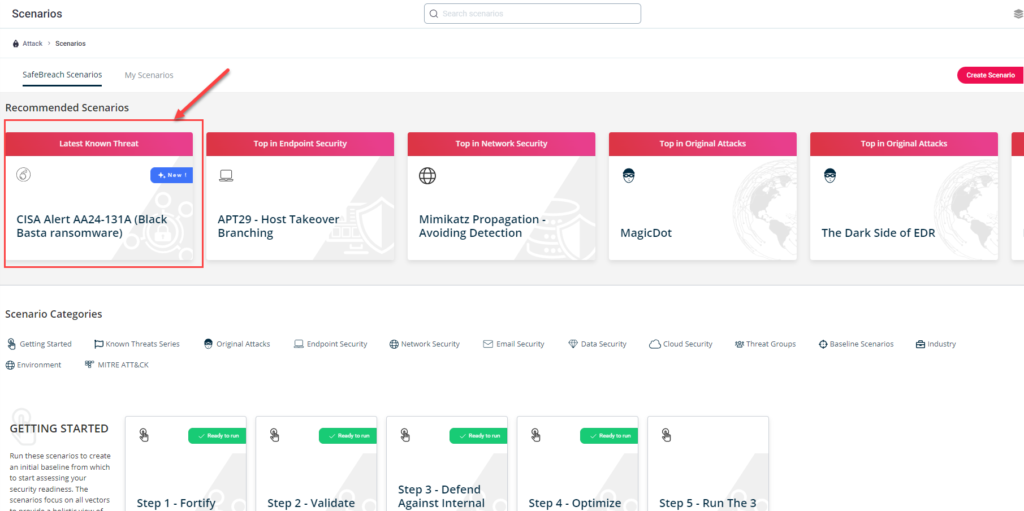
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-131A (Black Basta Ransomware)
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA24-131A (Black Basta Ransomware). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.

Method 3 – From the Known Attack Series report, select the US-CERT Alert AA24-131A (Black Basta Ransomware) report and select Run Simulations, which will run all attack methods.

NOTE – FBI, CISA, HHS, and MS-ISAC recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against growing threat of advanced cyber threats. Additional recommendations can be seen in each of the advisories (linked below):
- Install updates for operating systems, software, and firmware as soon as they are released.
- Require phishing-resistant multi-factor authentication (MFA).
- Implement recommendations, including training users to recognize and report phishing attempts.
- Require multifactor authentications for all services.
- Make backups of critical systems and device configurations to enable devices to be repaired and restored.
- For additional recommendations, please review the advisory in detail.


