This week Microsoft has released security updates for their products. These security updates fix 58 vulnerabilities in total, it is less than the average security update in 2020.
In this article we’re going to deep dive into 2 Microsoft Windows vulnerabilities fixed this month.
- CVE-2020-17140 Windows SMB Information Disclosure Vulnerability
- CVE-2020-17092 – Windows Network Connections Service Elevation of Privilege Vulnerability
CVE-2020-17140 root cause analysis
CVE-2020-17140 is a use after free (UAF) vulnerability which can get triggered remotely and can lead to a memory leak from a region in the kernel addresses space which contains information about a user-mode process. The vulnerability is in ‘srv2.sys’ which is also known as SMB 2.0 server driver, you can infer from its name that this driver handles all the client’s SMB 2.0 connections and this is the reason it is a builtin driver in windows.
According to MSRC this vulnerability existed in SMB clients as well but we’re not going to focus on that.
When we compared between the old and the new version of srv2.sys we found that only one function has changed named ‘Smb2UpdateLeaseFileName’ and the only blocks that has changed are the following:
on the left – the vulnerable version, on the right the fixed version
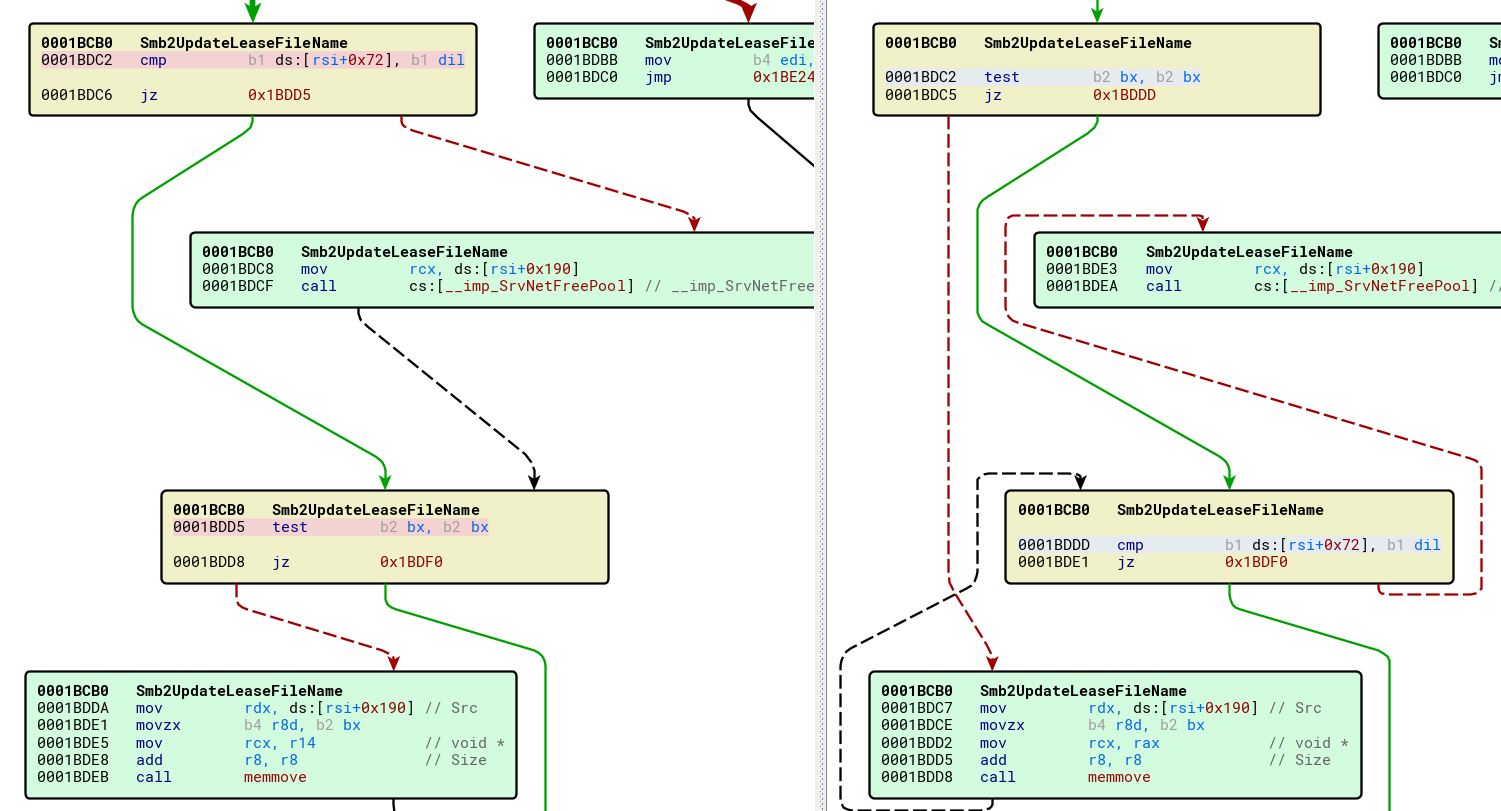
It is clear to see that on the vulnerable version (left side), if ds:[rsi+0x72] not equal to dil (the lower byte of rdi) it will free the pointer in ds:[rsi+0x190] using the function SrvNetFreePool,
But if bx is not zero it will copy that freed memory using memove function.
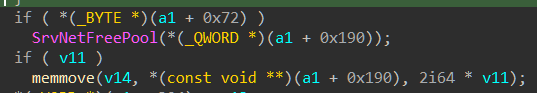
This code appears to be triggered in the logic of the smbv2 service processing SetInfo request, when the client sends an SMB2 SET_INFO request to set information about the file or underlying object storage.
CVE-2020-17092 root cause analysis
CVE-2020-17092 is a local vulnerability, a local user can escalate privileges from a weak user to Administrator privileges.
When we inspected netman.dll and netshell.dll We found 2 types of bug fixed there.
**Dll hijacking:
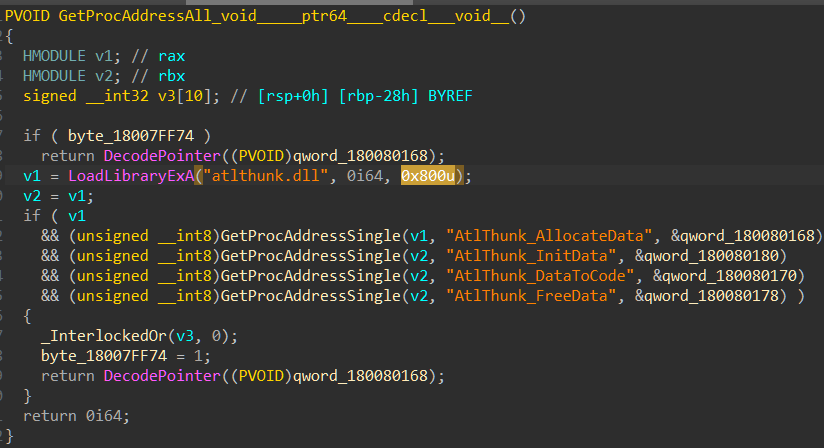
**Inside netshell.dll there are 4 variations of a function name GetProcAddressAll, originally the function loaded a dll named atlthunk.dll _using the function _LoadLibraryExA with flags variable (the 3rd variable) value 0 – which means it is equivalent to LoadLibraryA.
In the fixed version Microsoft changed the flag to 0x800 which is the flag named “LOADLIBRARYSEARCH_SYSTEM32” – means it will look for that dll in system32 only and not on other folders found in PATH environment variable (which can be changed by a weak user). Therefore we think that CVE-2020-17092 is a DLL hijacking vulnerability
after:
**
**
Unsigned overflow:
Microsoft fixed an unsigned integer overflow vulnerability in netman.dll. The variable which got overflowed then passed as an argument to function MemAlloc which means that it can lead to writing on the heap structure itself or other allocated buffers.
We compared the vulnerable version of netman.dll and the patched dll of netman.dll and the only changed function was in HrBuildPropertiesExFromProperties
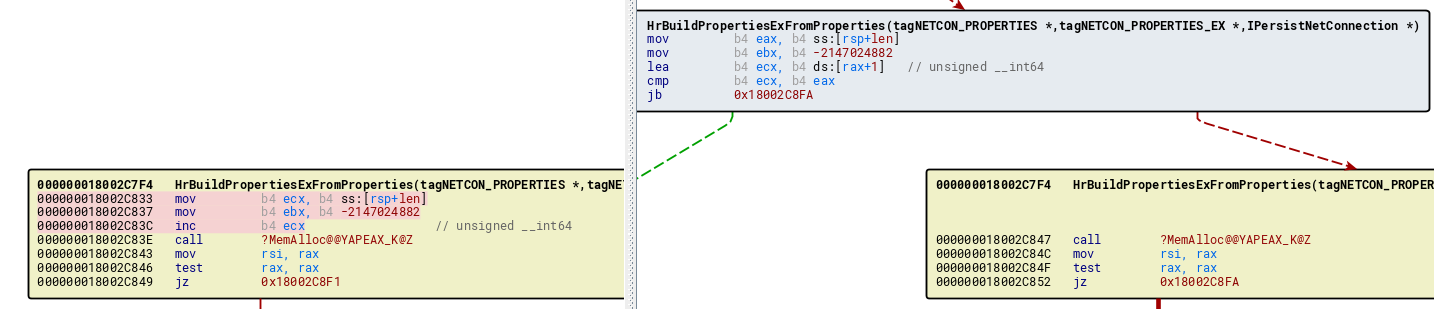
The only time len + 1 is smaller than len is when len is unsigned int max (0xffffffff) and adding +1 to it will cause the len to be zero.
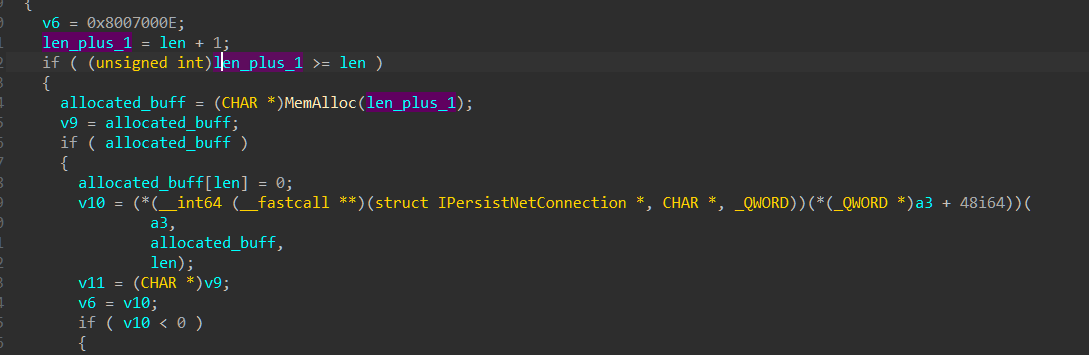
The same type of fix is found in netshell.dll in function HrBuildPropertiesExFromProperties so we’re not sure if it is related to netshell.dll or netman.dll
We are not 100% sure that this vulnerability is related to CVE-2020-17092.