On April 18th, the United States’ Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Europol’s European Cybercrime Centre (EC3), and the Netherlands’ National Cyber Security Centre (NCSC-NL) issued an urgent advisory about Akira ransomware’s recently exhibited malicious behavior (as of February 2024). Detailed information about these threats and the associated IOCs and TTPs can be seen on #StopRansomware: Akira Ransomware.
This blog will share an overview of the threat and our coverage for this ransomware variant. As a SafeBreach customer, you will have access to all the attacks listed below and more to validate your organizational security controls against this advanced ransomware family.
AA24-109A – Akira Ransomware – What You Should Know
The TTPs and IOCs identified in this advisory were the result of an investigation led by the FBI (in partnership with a trusted third party). According to the information available, Akira ransomware has been targeting a wide range of businesses and critical infrastructure entities since March 2023 across North America, Europe, and Australia. During the initial attacks, threat actors leveraging Akira ransomware targeted Windows-only systems. However, in April 2023, they began targeting VMware ESXi virtual machines through a new Linux variant. It is believed that as of the beginning of this year, the Akira ransomware group has successfully impacted over 250 organizations and has extorted nearly $42 million USD from the victims.
The early versions of the ransomware variant were written in C++ and encrypted files with a .akira extension. However, starting August 2023, some Akira ransomware attacks began deploying Megazord, leveraging Rust-based code that encrypts files with a .powerranges extension. Based on the current investigation, Akira threat actors have been using Megazord and Akira variants (including Akira v2) interchangeably to target victims. A typical Akira ransomware attack unfolds as follows:
- Initial Access – threat actors gain access to victims through a virtual private network (VPN) service without multifactor authentication (MFA) configured, mostly using known Cisco vulnerabilities CVE-2020-3259 and CVE-2023-20269. They have also been observed gaining access using external-facing services such as Remote Desktop Protocol (RDP), spear phishing, and abusing valid credentials.
- Persistence and Discovery – Once they gain access to victim networks, the threat actors attempt to abuse domain controller functions by creating new domain accounts, including creating an admin account named itadm. By leveraging Kerberoasting, threat actors have been observed extracting stored credentials from the process memory of the Local Security Authority Subsystem Service (LSASS). Additionally, these threat actors have been known to use credential scraping tools like Mimikatz and LaZagne to further privilege escalation. Tools like SoftPerfect and Advanced IP Scanner were also used for network device discovery (reconnaissance) purposes and net Windows commands were leveraged to identify domain controllers and gather information on domain trust relationships
- Defense Evasion – Threat actors were observed deploying 2 distinct ransomware variants against different system architectures within the same compromise event. Akira threat actors were first observed deploying the Windows-specific “Megazord” ransomware, with further analysis revealing that a second payload was concurrently deployed in this attack (later identified as a novel variant of the Akira ESXi encryptor, “Akira_v2”). To ensure unimpeded lateral movement within the victim network, threat actors disable security software to avoid detection, including the use of PowerTool to exploit the Zemana AntiMalware driver and terminate any antivirus-related processes.
- Exfiltration and Impact – Threat actors leverage tools like FileZilla, WinRAR, WinSCP, and RClone to exfiltrate data. To establish command and control channels, threat actors leverage readily available tools like AnyDesk, MobaXterm, RustDesk, Ngrok, and Cloudflare Tunnel, enabling exfiltration through various protocols such as File Transfer Protocol (FTP), Secure File Transfer Protocol (SFTP), and cloud storage services like Mega to connect to exfiltration servers. Threat actors use double extortion to encrypt victim systems after exfiltrating stolen data. The Akira ransom note provides each company with a unique code and instructions to contact the threat actors via a .onion URL. Akira threat actors do not leave an initial ransom demand or payment instructions on compromised networks, and do not relay this information until contacted by the victim. Ransom payments are paid in Bitcoin to cryptocurrency wallet addresses provided by the threat actors.
- Encryption – Akira threat actors utilize a sophisticated hybrid encryption scheme to lock data. This involves combining a ChaCha20 stream cipher with an RSA public-key cryptosystem for speed and secure key exchange. This approach tailors encryption methods based on file type and size and is capable of full or partial encryption. Encrypted files are appended with either a .akira or .powerranges extension. To further inhibit system recovery, Akira’s encryptor (w.exe) utilizes PowerShell commands to delete volume shadow copies (VSS) on Windows systems.

Important Note for SafeBreach Customers – Coverage for US-CERT AA24-109A
As soon as details were made available, the SafeBreach Labs teams added new attacks based on the advisory and mapped existing attacks in the Hacker’s Playbook to these US-CERT alerts immediately. It is important to note that existing SafeBreach customers already had a good level of coverage against the Akira ransomware variant identified in the advisories. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs.
Existing IOC-Based Playbook Attacks Related to AA24-109A
- #9003 – Write Akira (8ab296) ransomware to disk
- #9004 – Pre-execution phase of Akira (8ab296) ransomware (Linux)
- #9005 – Transfer of Akira (8ab296) ransomware over HTTP/S
- #9006 – Transfer of Akira (8ab296) ransomware over HTTP/S
- #9007 – Email Akira (8ab296) ransomware as a compressed attachment
- #9008 – Email Akira (8ab296) ransomware as a compressed attachment
- #9036 – Write Akira (e612b4) ransomware to disk
- #9037 – Pre-execution phase of Akira (e612b4) ransomware (Windows)
- #9038 – Transfer of Akira (e612b4) ransomware over HTTP/S
- #9039 – Transfer of Akira (e612b4) ransomware over HTTP/S
- #9040 – Email Akira (e612b4) ransomware as a compressed attachment
- #9041 – Email Akira (e612b4) ransomware as a compressed attachment
NEW IOC-Based Playbook Attacks Related to AA24-109A
- Akira (Megazord)
- #9993 – Write Akira (Megazord) (c53198) ransomware to disk
- #9994 – Pre-execution phase of Akira (Megazord) (c53198) ransomware (Windows)
- #9995 – Transfer of Akira (Megazord) (c53198) ransomware over HTTP/S
- #9996 – Transfer of Akira (Megazord) (c53198) ransomware over HTTP/S
- #9997 – Email Akira (Megazord) (c53198) ransomware as a compressed attachment
- #9998 – Email Akira (Megazord) (c53198) ransomware as a compressed attachment
- Akira_v2
- #9999 – Write Akira_v2 (be3f75) ransomware to disk
- #10000 – Pre-execution phase of Akira_v2 (be3f75) ransomware (Linux)
- #10001 – Transfer of Akira_v2 (be3f75) ransomware over HTTP/S
- #10002 – Transfer of Akira_v2 (be3f75) ransomware over HTTP/S
- #10003 – Email Akira_v2 (be3f75) ransomware as a compressed attachment
- #10004 – Email Akira_v2 (be3f75) ransomware as a compressed attachment
- Veeam-Get-Creds
- #10005 – Write Veeam-Get-Creds (afdb88) hacktool to disk
- #10006 – Transfer of Veeam-Get-Creds (afdb88) hacktool over HTTP/S
- #10007 – Transfer of Veeam-Get-Creds (afdb88) hacktool over HTTP/S
- #10008 – Email Veeam-Get-Creds (afdb88) hacktool as a compressed attachment
- #10009 – Email Veeam-Get-Creds (afdb88) hacktool as a compressed attachment
Existing Behavioral Attacks Related to AA24-109A
- #794 – Extract Login Information using MimiKatz (host level)
- #811 – Discover Linux network configuration using Bash (host level)
- #1011 – Discover Linux system information using Bash commands (host level)
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials (lateral movement)
- #1220 – Inject Mimikatz using PowerShell to Extract Credentials (lateral movement)
- #1693 – Collect Windows system data using CMD (host level)
- #1693 – Collect Windows system data using CMD (host level)
- #1695 – Discover Linux processes using Bash scripts (host level)
- #2170 – Create Account (Windows) (host level)
- #2174 – Extract users and groups using net.exe (Windows) (host level)
- #2175 – Discover Linux user configurations using Bash (Linux) (host level)
- #2188 – Extract Process List using Windows Commands (host level)
- #2222 – Discover Remote Systems using PowerShell (host level)
- #2273 – Pass the Hash over SMB using Mimikatz (lateral movement)
- #2273 – Pass the Hash over SMB using Mimikatz (lateral movement)
- #2306 – Domain Trust Discovery (host level)
- #3819 – Windows Credentials Collection using LaZagne (host level)
- #3827 – Linux Credentials Collection using LaZagne (host level)
- #3829 – Run obfuscated Mimikatz on host (host level)
- #3829 – Run obfuscated Mimikatz on host (host level)
- #3829 – Run obfuscated Mimikatz on host (host level)
- #5672 – Agentless lateral movement via WMI (host level)
- #5673 – Agentless lateral movement via Remote PowerShell (WMI) (host level)
- #5833 – Extract Login Information using MimiKatz DCSync (host level)
- #6127 – Extract LSASS memory dump using Rundll32 (host level)
- #6372 – Modify Volume Shadow Copy (VSS) (host level)
- #6473 – Agentless lateral movement via RDP (host level)
- #6513 – Agentless lateral movement via SMB and RCE, using Mimikatz (host level)
- #6580 – Discover domain groups using LDAP method (host level)
- #6581 – Discover domain computers using LDAP method (host level)
- #6801 – Credential harvesting using Mimikatz DCSync with interactive session token (host level)
- #6802 – Credential harvesting using Mimikatz DCSync with user credentials (host level)
- #7168 – Enable a default account and add it to a Localgroup (Windows) (host level)
- #8370 – In memory credential extraction via MiniDumpWriteDump (host level)
- #8371 – In memory credential extraction via MiniDumpWriteDump and handle hijacking (host level)
- #8372 – Credential extraction via Pypykatz (host level)
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
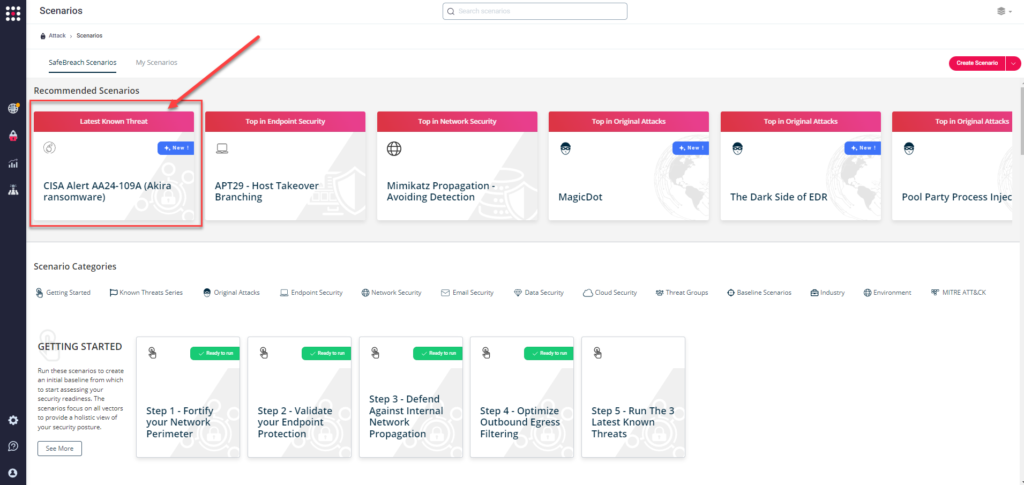
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA24-109A (Akira Ransomware)
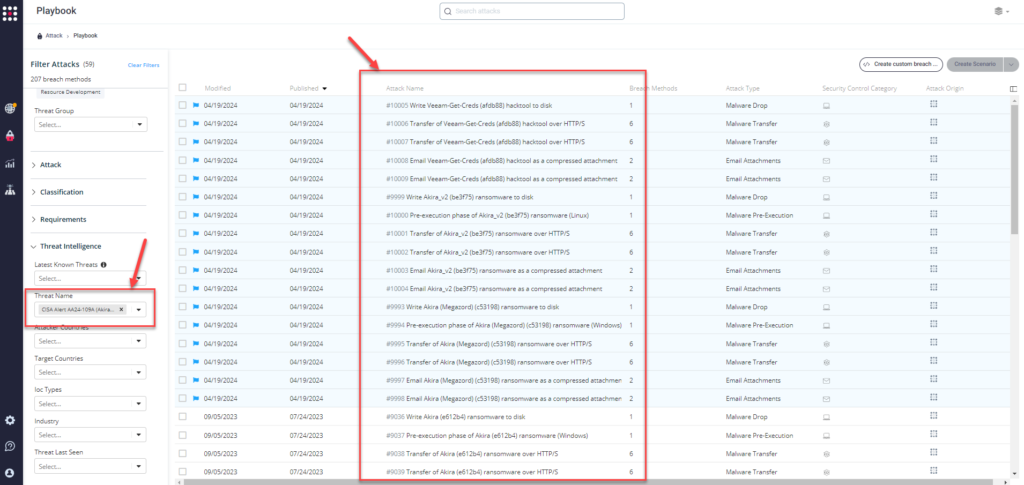
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA24-109A (Akira Ransomware). Additionally, you can refer to the list above to ensure a comprehensive level of coverage.
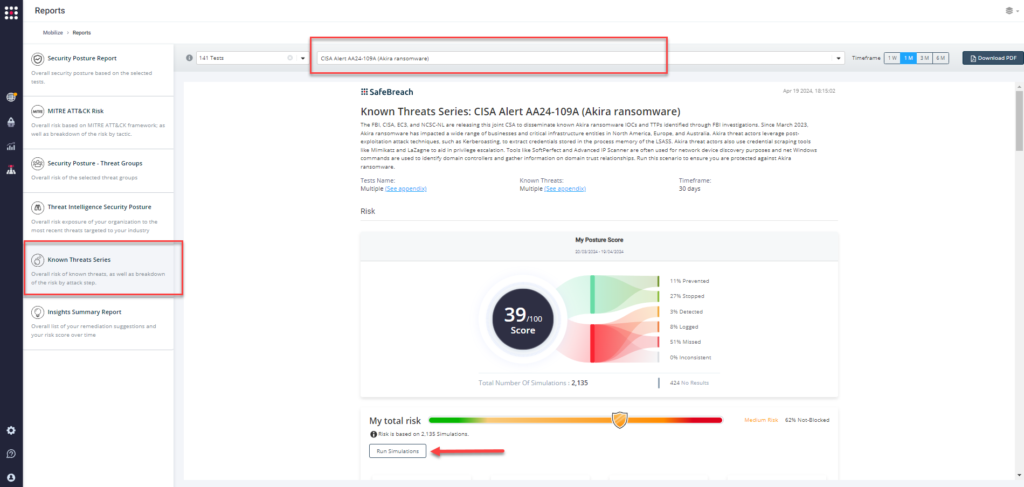
Method 3 – From the Known Attack Series report, select the US-CERT Alert AA24-109A (Akira Ransomware) report and select Run Simulations, which will run all attack methods.
NOTE – FBI, CISA, EC3, and NCSC-NL recommend continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations can be seen below:
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location.
- Require all accounts with password logins.
- Require multifactor authentication for all services.
- Keep all operating systems, software, and firmware up to date.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool.
- For additional recommendations, please review the advisory in detail.


