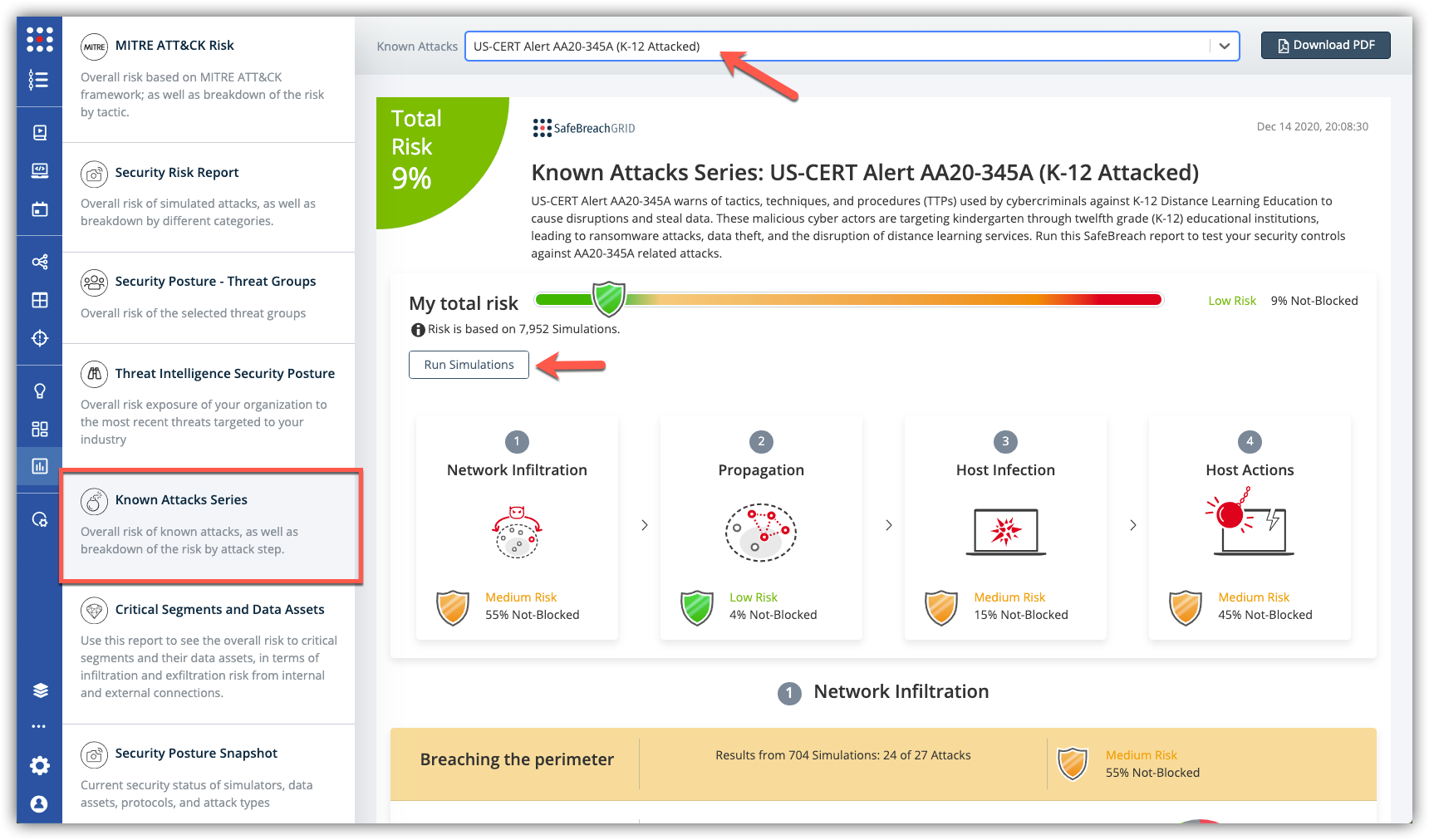
Cyber Actors Target K-12 Distance Learning Education to Cause Disruptions and Steal Data
SafeBreach Labs has updated the Hacker’s Playbook™ with new attack methods for malware samples described in US-CERT (AA20-345A) Cyber Actors Target K-12 Distance Learning Education to Cause Disruptions and Steal Data which addresses attacks on educational institutions with several different ransomware and malware strains along with DDOS and uninvited users disrupting video conference classrooms.
The SafeBreach Hacker’s Playbook already had attacks for the malware strains noted in the alert. No new attacks were added to address this coverage and filtering in the playbook by the malware name will detail each of the attacks. The existing coverage is extensive and a general breakdown in coverage is as follows:
517 existing playbook methods related to AA20-345A:
- 433 attacks for Maze coverage
- 10 attacks for Ryuk coverage
- 10 attacks for Dridex coverage
- 8 attacks for Zeus coverage
- 8 attacks for CoinMiner coverage
- 8 attacks for Gh0st coverage
- 7 attacks for IRC Bot coverage
- 6 attacks for REvil/Sodinokibi coverage
- 6 attacks for Agent Telsa coverage
- 6 attacks for NanoCore coverage
- 5 attacks for Kovter coverage
- 5 attacks for Cerber coverage
- 5 attacks for Shlayer coverage
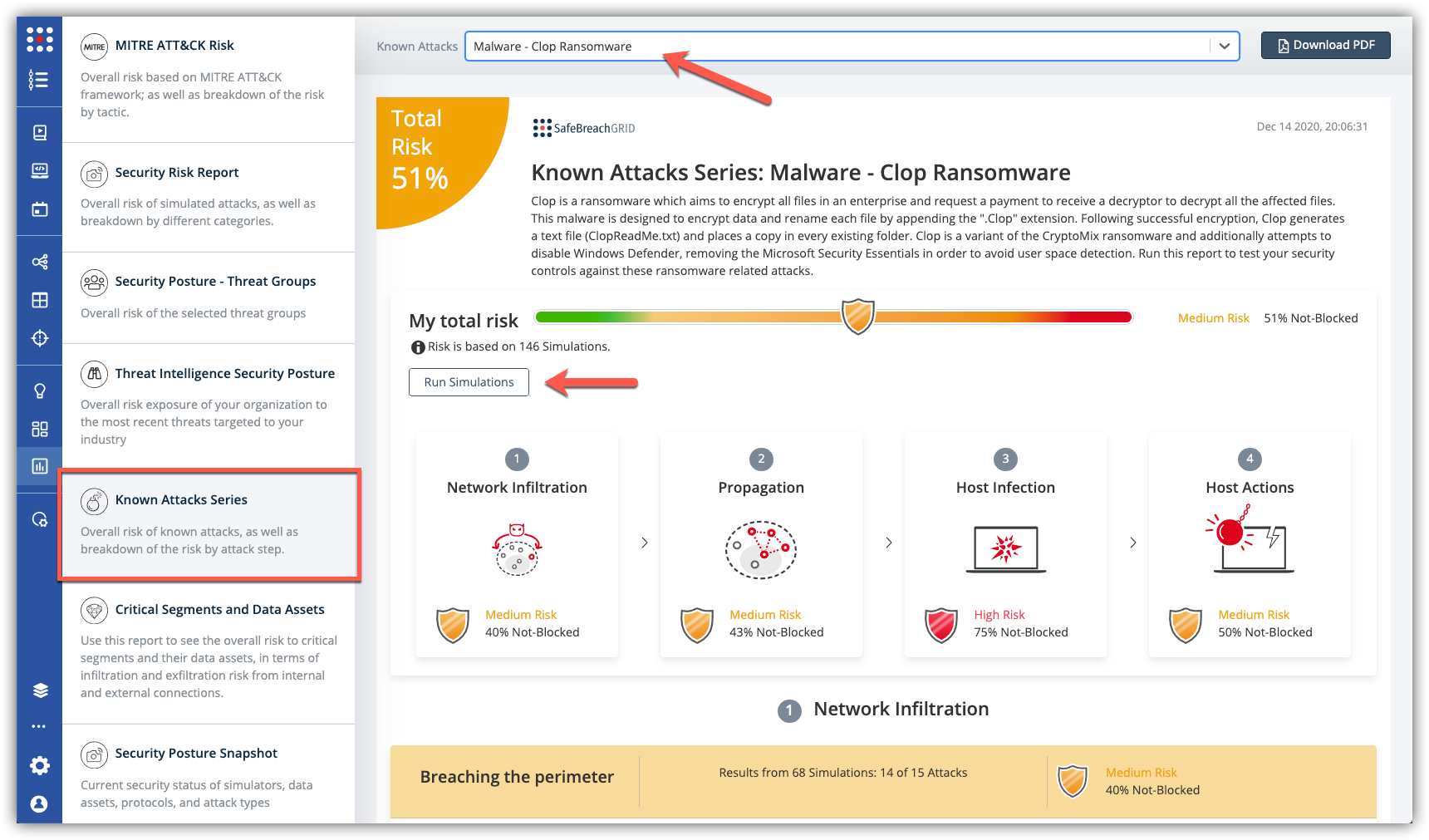
Clop Ransomware
In addition, the SafeBreach Hacker’s Playbook™ has been updated to test against Clop Ransomware attacks. There have been large scale attacks using Clop recently, the following attacks have been included to test security controls to validate your security defense will prevent and/or detect the attack.
46 newly developed playbook methods related to Clop Ransomware:
- #3564 – Execute the clop ransomware
- #3711 – Write clop ransomware to disk
- #5541 – Pre-execution phase of clop_ransomware malware
- #5542 – Write clop_ransomware malware to disk
- #5543 – Transfer of clop_ransomware malware over HTTP/S
- #5544 – Transfer of clop_ransomware malware over HTTP/S
- #5545 – Email clop_ransomware malware as a ZIP attachment
- #5546 – Email clop_ransomware malware as a ZIP attachment
- #5616 – Pre-execution phase of clop_ransomware malware
- #5617 – Write clop_ransomware malware to disk
- #5618 – Transfer of clop_ransomware malware over HTTP/S
- #5619 – Transfer of clop_ransomware malware over HTTP/S
- #5620 – Email clop_ransomware malware as a ZIP attachment
- #5621 – Email clop_ransomware malware as a ZIP attachment
- #5622 – Pre-execution phase of clopransomware6a15 malware
- #5623 – Write clopransomware6a15 malware to disk
- #5624 – Transfer of clopransomware6a15 malware over HTTP/S
- #5625 – Transfer of clopransomware6a15 malware over HTTP/S
- #5626 – Email clopransomware6a15 malware as a ZIP attachment
- #5627 – Email clopransomware6a15 malware as a ZIP attachment
- #5628 – Pre-execution phase of clopransomware94b7 malware
- #5629 – Write clopransomware94b7 malware to disk
- #5630 – Transfer of clopransomware94b7 malware over HTTP/S
- #5631 – Transfer of clopransomware94b7 malware over HTTP/S
- #5632 – Email clopransomware94b7 malware as a ZIP attachment
- #5633 – Email clopransomware94b7 malware as a ZIP attachment
- #5634 – Pre-execution phase of clopransomwareccf9 malware
- #5635 – Write clopransomwareccf9 malware to disk
- #5636 – Transfer of clopransomwareccf9 malware over HTTP/S
- #5637 – Transfer of clopransomwareccf9 malware over HTTP/S
- #5638 – Email clopransomwareccf9 malware as a ZIP attachment
- #5639 – Email clopransomwareccf9 malware as a ZIP attachment
- #5640 – Pre-execution phase of clopransomware389e malware
- #5641 – Write clopransomware389e malware to disk
- #5642 – Transfer of clopransomware389e malware over HTTP/S
- #5643 – Transfer of clopransomware389e malware over HTTP/S
- #5644 – Email clopransomware389e malware as a ZIP attachment
- #5645 – Email clopransomware389e malware as a ZIP attachment
- #5646 – Pre-execution phase of clopransomwareb631 malware
- #5647 – Write clopransomwareb631 malware to disk
- #5648 – Transfer of clopransomwareb631 malware over HTTP/S
- #5649 – Transfer of clopransomwareb631 malware over HTTP/S
- #5650 – Email clopransomwareb631 malware as a ZIP attachment
- #5651 – Email clopransomwareb631 malware as a ZIP attachment
What you should do now
The Known Attack Series reports are updated so you can run the specific attacks for US-CERT AA20-345A alert and/or Clop Ransomware. From the Known Attack Series report, select either the US-CERT Alert AA20-345A (K-12 Attacked) or the Malware: Clop Ransomware reports and select Run Simulations which will run all the attack methods.