SafeBreach Labs has updated the Hacker’s Playbook™ with new simulations for attacks described in US-CERT COVID-19 Exploited by Malicious Cyber Actors (AA20-099A) which details the growing use of COVID-19 related attacks by APT groups. Attacks noted are numerous and extensive as unfortunately hackers are leveraging the pandemic to trick users and exploit new remote workforce infrastructure such as networks and VPN access.
The new IOCs defined are predominantly infiltration techniques, socially engineered around coronavirus, using the organizations that are keeping us current and informed, see sample phishing email addressed from World Health Organization that we presented in our Top 4 Security Validations for a Remote Workforce webinar. The phishing lures are designed to direct users to newly registered domains to phish for credentials or download / deploy malware like ransomware or trojans.
The techniques used to exploit employees working from home are designed to leverage VPN, VDI and RDP vulnerabilities and attacks, specifically brute force attacks.
The SafeBreach Hacker’s Playbook addresses the wide array of attacks noted throughout the alert to keep your remote workforce safe.
Newly developed playbook methods related to AA20-099A:
- #4137 – Email a link to coronavirus-tshirt[.]shop (USCERT_AA20-099A)
- #4138 – Email a link to coronavirus-tshirts[.]shop (USCERT_AA20-099A)
- #4139 – Email a link to coronavirustr[.]shop (USCERT_AA20-099A)
- #4140 – Email a link to covid19goods[.]shop (USCERT_AA20-099A)
- #4141 – Email a link to fightcovid19[.]shop (USCERT_AA20-099A)
- #4142 – Email a link to nocovid19[.]shop (USCERT_AA20-099A)
- #4143 – Email a link to fukcovid19[.]shop (USCERT_AA20-099A)
- #4144 – Email a link to covid19help[.]shop (USCERT_AA20-099A)
- #4145 – Email a link to coronavirustestkit[.]shop (USCERT_AA20-099A)
- #4146 – Email a link to covid19livebd[.]shop (USCERT_AA20-099A)
- #4147 – Email a link to corona-virus-test-kits[.]shop (USCERT_AA20-099A)
- #4148 – Email a link to corona-virus-test[.]shop (USCERT_AA20-099A)
- #4149 – Email a link to anti-covid19[.]shop (USCERT_AA20-099A)
- #4150 – Email a link to lireproustautempsducoronavirus[.]blog (USCERT_AA20-099A)
- #4151 – Email a link to nocovid[.]fun (USCERT_AA20-099A)
- #4152 – Email a link to covid19com[.]blog (USCERT_AA20-099A)
- #4153 – Email a link to coronaviruslaw[.]blog (USCERT_AA20-099A)
- #4154 – Email a link to copingwithcovid[.]blog (USCERT_AA20-099A)
- #4155 – Email a link to covid19quarantine[.]fun (USCERT_AA20-099A)
- #4156 – Email a link to whatcoronavirus[.]com (USCERT_AA20-099A)
- #4157 – Email a link to vaccine-coronavirus[.]com (USCERT_AA20-099A)
- #4158 – Email a link to trackcoronavirus[.]com (USCERT_AA20-099A)
- #4159 – Email a link to coronabye[.]com (USCERT_AA20-099A)
- #4160 – Email a link to corona-nearby[.]com (USCERT_AA20-099A)
- #4161 – Email a link to coronavirusabc[.]com (USCERT_AA20-099A)
- #4162 – Email a link to coronavirusdefense[.]com (USCERT_AA20-099A)
- #4163 – Email a link to coronavirus[.]page (USCERT_AA20-099A)
- #4164 – Email a link to coronavirus19news[.]com (USCERT_AA20-099A)
- #4165 – Email a link to coronastats[.]net (USCERT_AA20-099A)
- #4166 – Email a link to thecoronaviruslive[.]info (USCERT_AA20-099A)
- #4167 – Email a link to whereisthecoronavirus[.]com (USCERT_AA20-099A)
- #4168 – Email a link to coronavirusupdate[.]tk (USCERT_AA20-099A)
- #4169 – Email a link to coronavirustechhandbook[.]com (USCERT_AA20-099A)
- #4170 – Email a link to trackcorona[.]net (USCERT_AA20-099A)
- #4171 – Email a link to coronawatch[.]eu (USCERT_AA20-099A)
- #4172 – Email a link to coronavirus-in[.]space (USCERT_AA20-099A)
- #4173 – Email a link to mycoronavirus[.]world (USCERT_AA20-099A)
- #4174 – Email a link to coronanow[.]kr (USCERT_AA20-099A)
- #4175 – Email a link to coronastop28[.]com (USCERT_AA20-099A)
- #4176 – Email a link to coronavirusecuador[.]com (USCERT_AA20-099A)
- #4177 – Email a link to stopcorona[.]org (USCERT_AA20-099A)
- #4178 – Email a link to coronavirus-testing[.]com (USCERT_AA20-099A)
- #4179 – Email a link to corona-virus[.]tokyo (USCERT_AA20-099A)
- #4180 – Email a link to coronavirus[.]cc (USCERT_AA20-099A)
- #4181 – Email a link to coronavirustoday[.]com (USCERT_AA20-099A)
- #4182 – Email a link to coronavirusupdates[.]online (USCERT_AA20-099A)
- #4183 – Email a link to coronavirusofficialnews[.]com (USCERT_AA20-099A)
- #4184 – Email a link to coronaviruszone[.]com (USCERT_AA20-099A)
Existing playbook methods related to AA20-099A:
- #192 – Brute force attack over RDP protocol
- #2298 – Malicious C2 Communication (Infiltration)
- #3003 – Email trickbot malware as a ZIP attachment (Infiltration)
- #1382 – Transfer of the TrickBot Malware over HTTP (Lateral Movement)
- #3002 – Transfer of trickbot malware over HTTP/S (Lateral Movement)
- #2326 – Transfer of TrickBot malware dropper over HTTP/S (Lateral Movement)
- #1868 – Email the TrickBot malware as part of a ZIP attachment (Infiltration)
- #1887 – Email the TrickBot (21.5.2018) malware as part of a ZIP attachment (Infiltration)
- #1560 – Transfer of the TrickBot Malware over HTTP/s (Lateral Movement)
- #3004 – Email trickbot malware as a ZIP attachment (Lateral Movement)
- #1387 – Write to Disk of TrickBot (Host Level)
- #3085 – Pre-execution phase of TrickBot (21.5.2018) files malware (Host Level)
- #3070 – Pre-execution phase of TrickBot malware (Host Level)
- #2070 – Email the TrickBot malware as part of a ZIP attachment (Lateral Movement)
- #2089 – Email the TrickBot (21.5.2018) malware as part of a ZIP attachment (Lateral Movement)
- #1559 – Write TrickBot (21.5.2018) files to Disk (Host Level)
- #2108 – Write TrickBot Files to Disk (Host Level)
- #1381 – Write TrickBot to disk (Host Level)
- #3191 – Pre-execution phase of trickbot malware (Host Level)
- #3001 – Transfer of trickbot malware over HTTP/S (Infiltration)
- #3000 – Write trickbot malware to disk (Host Level)
- #2109 – Transfer of the TrickBot Malware over HTTP/s (Lateral Movement)
- #3098 – Pre-execution phase of TrickBot Files malware (Host Level)
The alert also addresses ransomware without calling out a specific ransomware. The SafeBreach Hacker’s Playbook has attack methods for over 100 different types of ransomware, that we suggest that you include in your testing for this specific US-CERT alert.
SafeBreach Has You Covered
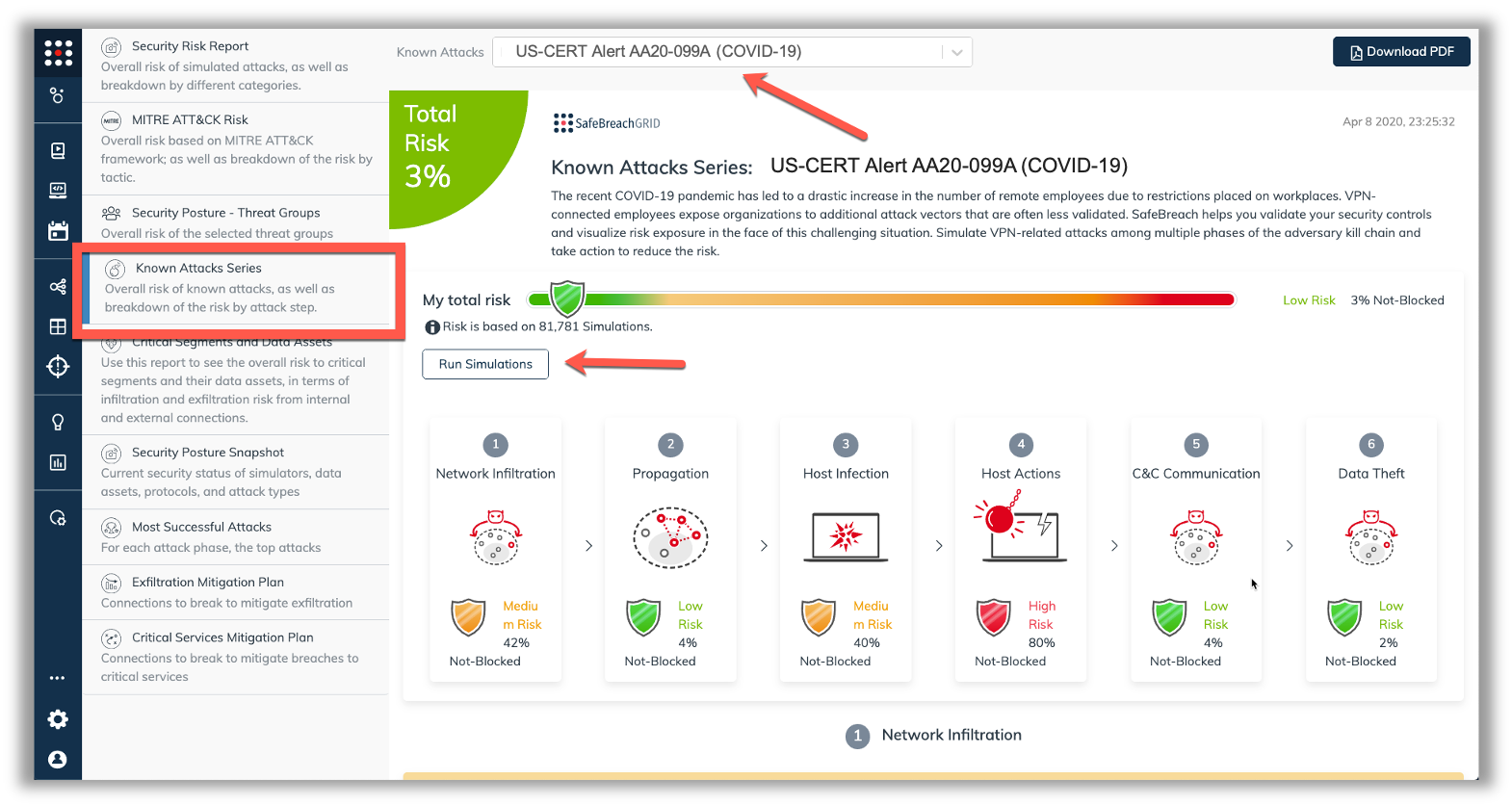
The new attack methods are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run only the attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA20-099A (COVID-19) report and there is an option to Run Simulations which will run all the attacks.