SafeBreach Labs has updated the Hacker’s Playbook™ with new simulations for attacks described in US-CERT Malware Analysis Report (AR19-304A) which describes updated techniques with new samples and behaviors for “HOPLIGHT” originating from North Korean (aka. “HIDDEN COBRA”).
HOPLIGHT is a backdoor trojan that drops files that are primarily proxy applications that mask traffic between the malware and remote operators. The proxies have the ability to generate fake TLS handshake sessions using valid public SSL certificates, disguising network connections with remote malicious actors. One file contains a public SSL certificate and the payload of the file appears to be encoded with a password or key. The remaining file does not contain any of the public SSL certificates, but attempts outbound connections and drops four files. The dropped files primarily contain IP addresses and SSL certificates.
HOPLIGHT is a nation-state attack that all organizations need to set as a priority as the widespread availability presents a challenge for network defenses and threat-actor attribution. SafeBreach recommends all industries and businesses simulate the tools described in this alert to identify whether or not they are protected against these attacks.
To assess security control effectiveness against these techniques, the SafeBreach Breach and Attack Simulation Platform specifically tests the following endpoint and network security controls available now:
Newly developed playbook methods related to AR19-304A
Playbook # 2383 – Write HOPLIGHT (AR19-304A) malware to disk (Host Level)
- Endpoint Controls – Are security controls or hardening in place to prevent saving the malicious files to local disk?
Playbook # 2384 – Transfer of HOPLIGHT (AR19-304A) malware over HTTP/S (Lateral Movement)
- Network Controls – Are security controls in place to prevent the download and transfer of the targeted malware used in this attack?
Playbook # 2385 – Transfer of HOPLIGHT (AR19-304A) malware over HTTP/S (Infiltration)
- Network Controls – Are security controls in place to prevent the download and transfer of the targeted malware used in this attack?
Playbook # 2386 – Email HOPLIGHT (AR19-304A) malware as a ZIP attachment (Lateral Movement)
- Email Controls – Are security controls in place to scan and identify email for the malicious payloads used in this attack?
Playbook # 2387 – Email HOPLIGHT (AR19-304A) malware as a ZIP attachment (Infiltration)
- Email Controls – Are security controls in place to scan and identify email for the malicious payloads used in this attack?
Playbook # 2389 – Add a Firewall Rule using netsh.exe (Host Level)
- Endpoint Controls – Are security controls or hardening in place to prevent the actions taking place on the computer?
Existing playbook methods related to AR19-304A
Playbook # 794 – Run Mimikatz on host
- Endpoint Controls – Are security controls or hardening in place to prevent the function hooking used in this attack?
Playbook # 2298 – Malicious C2 Communication
- Network Controls – Are security controls in place to detect and prevent communication with the FQDNs and IP addresses used in this attack?
Playbook # 109 – HTTP exfiltration
- Network Controls – Are security controls in place to prevent the exfiltration technique used in this attack?
Playbook # 2246 – Hooking of GetSystemTime function using mavinject.exe with a custom DLL (T1179)
- Endpoint Controls – Are security controls or hardening in place to prevent the function hooking used in this attack?
Playbook # 2293 – Create and Start a Service
- Endpoint Controls – Are security controls or hardening in place to prevent the persistence technique used in this attack?
SafeBreach validates your existing security controls are working as intended on an automated and continuous basis with the leading Breach and Attack Simulation platform. The SafeBreach Hacker’s Playbook™ of breach methods simulates these breach scenarios, and thousands more, without impacting users or infrastructure. Breach methods are constantly updated by SafeBreach Labs, our team of offensive security researchers, to help keep customers ahead of attacks.
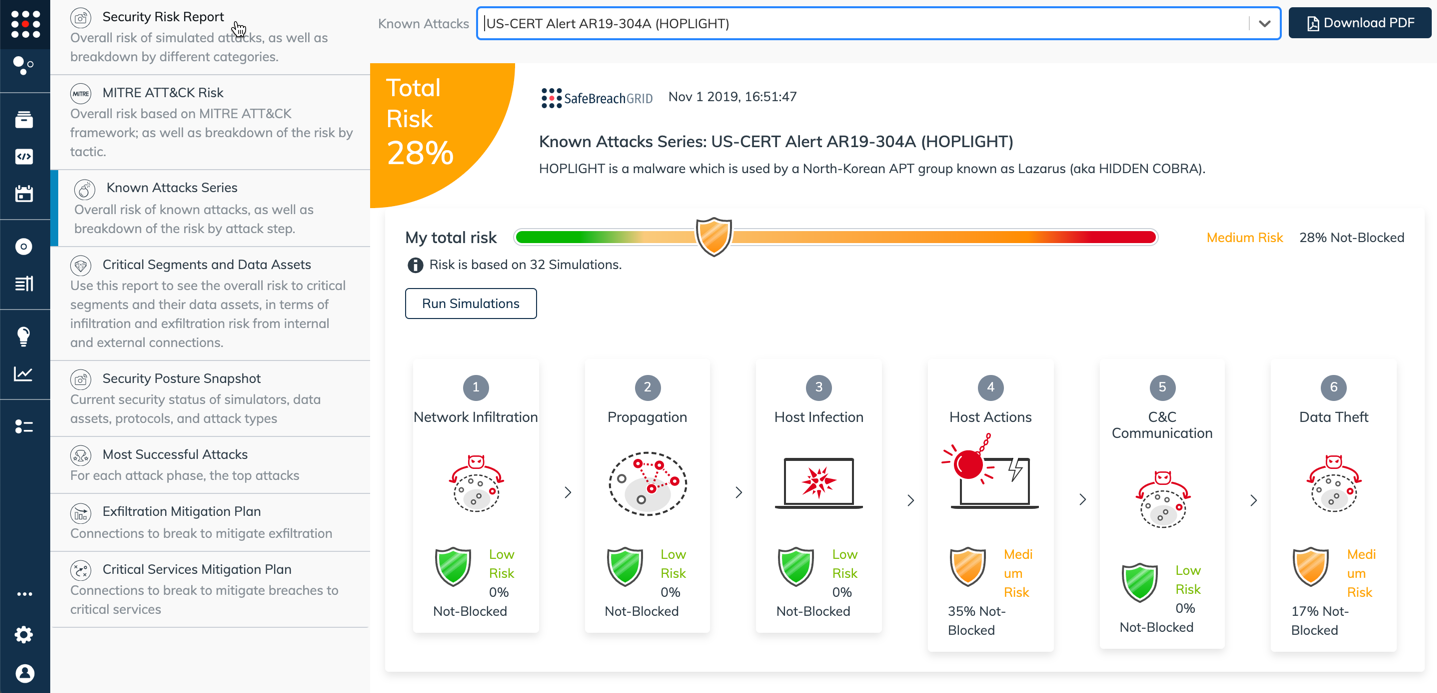
SafeBreach customers can easily report on their security posture against known threat groups by leveraging the new “Known Attacks Series” report for US-CERT Alert AR19-304A (HOPLIGHT) showing where they are susceptible to the latest breach methods released by SafeBreach labs.