SafeBreach Labs has an extensive Hacker’s Playbook™ that protects organizations from known threat groups tactics, techniques, and procedures (TTPs). The US-CERT Dridex Malware Alert (AA19-339A) which supplied updated indicators of compromise (IOCs) for Dridex was just released but SafeBreach customers can rest assured they are already protected.
Dridex is one of the most prevalent banking trojan associated with threat groups, TA505, Indrik Spider, Mummy Spider and TA542 that has caused major havoc to US financial institutions since 2011. Fraud and hacking charges were also announced today alleging over \$100 million was stolen from hundreds of US banks.
To assess security control effectiveness against Dridex, the SafeBreach Breach and Attack Simulation Platform specifically tests the following security controls :
Existing playbook infiltration methods related to AA19-339A
- #310 – Dridex Malware passed via HTTP/S
- #2530 – Transfer of Dridex malware over HTTP/S
- #1590 – Email Dridex v4 inside a ZIP attachment
- #2532 – Email Dridex malware as a ZIP attachment
Existing playbook lateral movement methods related to AA19-339A
- #1599 – Email Dridex v4 inside a ZIP attachment
- #2531 – Email Dridex malware as a ZIP attachment
- #2529 – Transfer of Dridex v4 malware over HTTP/S
- #275 – Dridex Malware passed via HTTP/S
Existing playbook host level methods related to AA19-339A
- #2528 – Write Dridex malware to disk (Host-level)
- #2528 – Write Dridex malware to disk
SafeBreach customer can quickly and easily run all simulations associated with Dridex from the SafeBreach Playbook by searching Dridex:
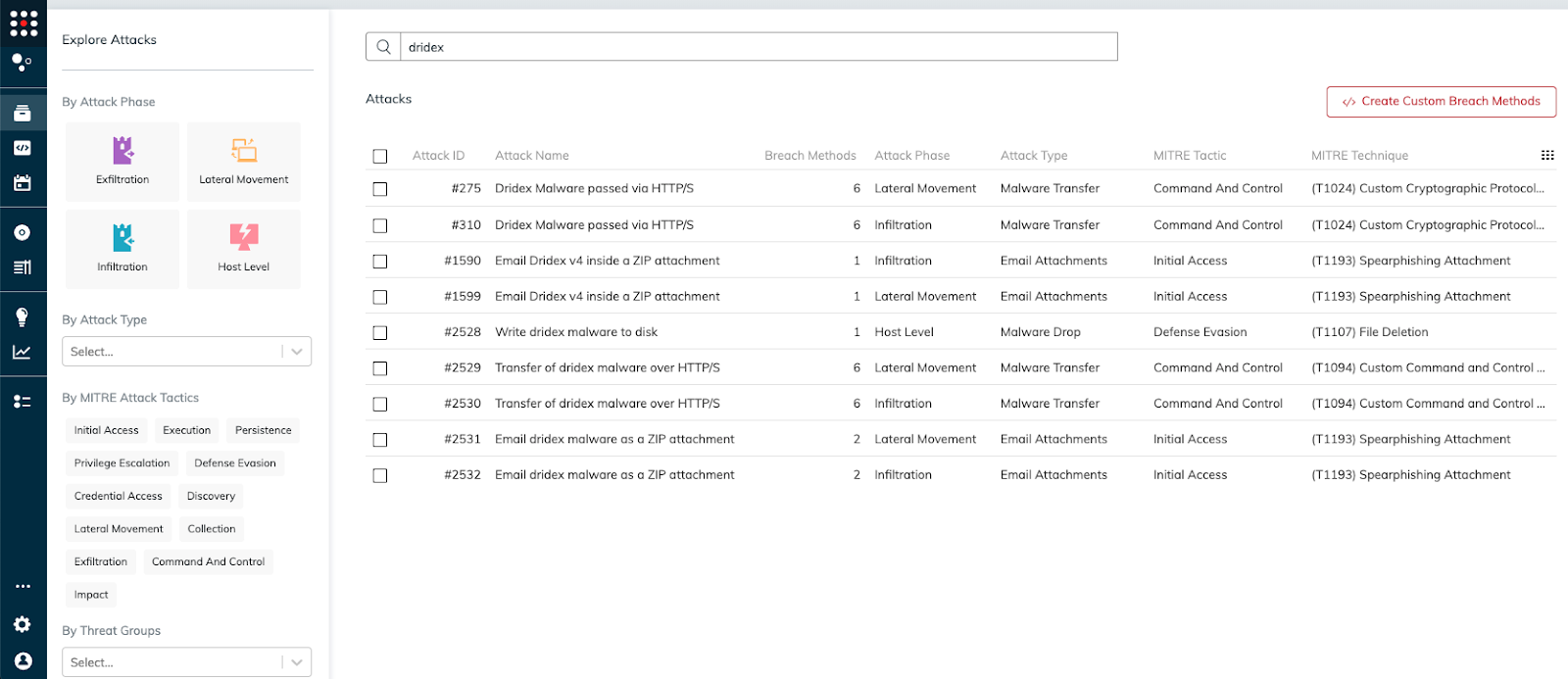
Select all the Attack ID’s and once all the simulations run you can easily assess which simulations were stopped and which were missed with remediation efforts to harden your security posture:
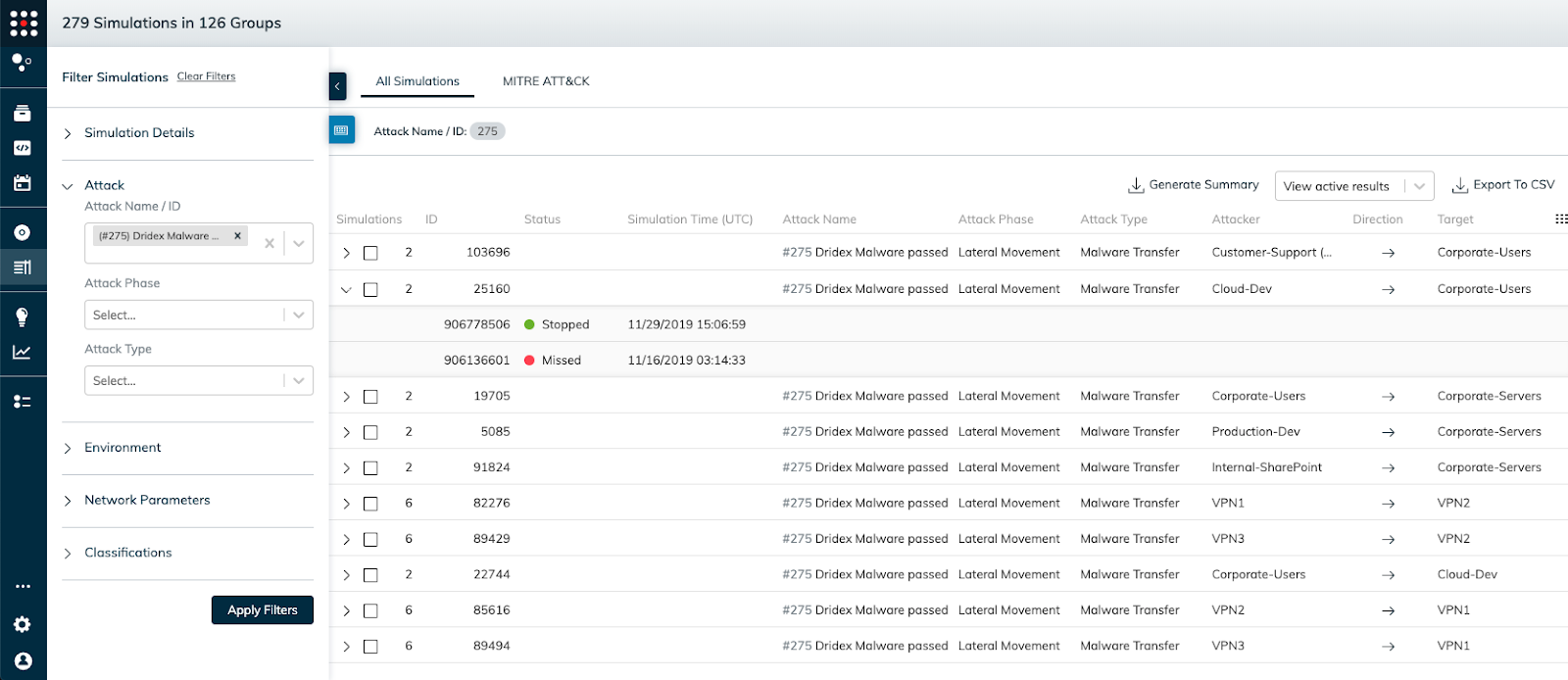
SafeBreach validates your existing security controls are working as intended on an automated and continuous basis with the leading Breach and Attack Simulation platform. The SafeBreach Hacker’s Playbook™ of breach methods simulates these breach scenarios, and thousands more, without impacting users or infrastructure. Breach methods are constantly updated by SafeBreach Labs, our team of offensive security researchers, to help keep customers ahead of attacks.
For any questions, please visit the SafeBreach Support Portal and submit a support request.