Introduction
SafeBreach Labs discovered a new vulnerability in Lenovo System Interface Foundation service, which is preinstalled on Lenovo PCs.
In this post, we will demonstrate how the CVE-2019-6189 vulnerability could have been used in order to achieve defense evasion and persistence by loading an arbitrary unsigned DLL into a signed process that runs as NT AUTHORITY\SYSTEM.
Note: In order to exploit this vulnerability the attacker needs to have Administrator privileges.
Lenovo System Interface Foundation
Lenovo System Interface Foundation is a necessary component of the following Universal Windows Platform applications:
- Lenovo Vantage
- Lenovo Settings for Enterprise
The component is preinstalled on Windows-based Lenovo PCs.
Vulnerability Discovery
In our exploration, we targeted the Lenovo System Interface Foundation service.
In addition to the fact that it is a signed process that runs as NT AUTHORITY\SYSTEM, this service was interesting because it is preinstalled on Windows-based Lenovo PCs. This vulnerability, preinstalled in many units, could have a widespread impact, with serious consequences for thousands of users.
After the Lenovo System Interface Foundation service started, it executed Lenovo.Modern.ImController.PluginHost.Device.exe as NT AUTHORITY\SYSTEM.
Once executed, the process tried to load Wintrust.dll from its own directory, instead of SysWOW64:
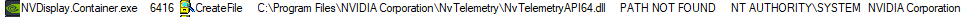
The service then tried to load a missing DLL file (Wintrust.dll)
PoC Demonstration
In order to test this vulnerability, we compiled an x86 arbitrary DLL which writes the following to the filename of a txt file:
- The name of the process which loaded it
- The username which executed it
- The name of the DLL file
We then placed it in the following path and restarted the computer:
C:\Program Files (x86)\Lenovo\ImController\PluginHost\wintrust.dll
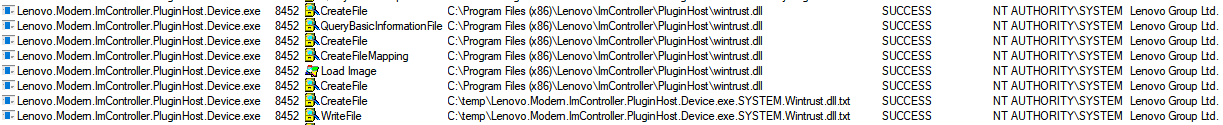
We were able to load an arbitrary DLL and execute our code within Lenovo.Modern.ImController.PluginHost.Device exe which was signed by “Lenovo Group Ltd.” and run as NT AUTHORITY\SYSTEM.
Root Cause Analysis
In order to analyze this one, we used dnSpy, because the vulnerable executable is based on .NET.
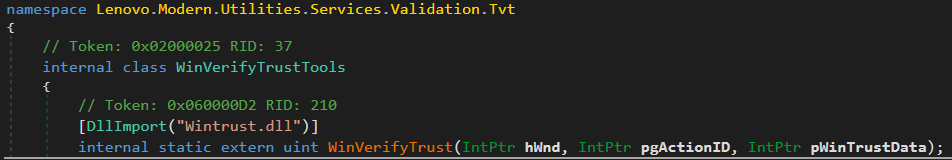
In order to verify the certificate of different binaries (for example, to load only trusted libraries), the Lenovo.Modern.ImController.PluginHost.Device.exe process uses the WinVerifyTrust WinAPI function.
The implementation can be found in the Lenovo.Modern.Utilities.dll (a shared framework for Lenovo Binaries), inside the Lenovo.Modern.Utilities.Services.Validation.Tvt.WinVerifyTrustTools class.
It uses the DllImport attribute to load the Wintrust.dll unmanaged DLL:
There are two root causes for this vulnerability:
- No digital certificate validation was made against this specific binary. The program did validate whether different DLL files which it loads are signed, but when it imported the Wintrust.dll library, it didn’t validate it (because it relied on the WinVerifyTrust function which is inside the DLL and hadn’t been loaded yet). Therefore, it was able to load an arbitrary unsigned DLL.
- Untrusted DLL Search Order
The code didn’t use the DefaultDllImportSearchPathsAttribute attribute with the System32 value of the DllImportSearchPath enum, so it tried to look for the library first in the CWD of the application, instead of loading it directly from SysWOW64.
Potential Malicious Uses and Impact
Below we show three possible ways that an attacker could have leveraged the CVE-2019-6189 vulnerability which we discovered and documented above.
Signed Execution, Whitelisting Bypass
The vulnerability gave attackers the ability to load and execute malicious payloads within the context of a Lenovo signed process. This ability might have been abused by an attacker for different purposes such as execution and evasion, for example: Application Whitelisting Bypass.
Persistence Mechanism
The vulnerability gave an attacker the ability to load and execute malicious payloads in a persistent way, each time the services were loaded. That means that once the attacker dropped a malicious DLL, the services would load the malicious code each time it was restarted.
Affected Products and Versions
- Lenovo System Interface Foundation – Prior to version 1.1.18.2
Timeline
Aug 28th, 2019 – Vulnerability reported to Lenovo PSIRT
Aug 28th, 2019 – Initial automatic response from Lenovo
Aug 28th, 2019 – Lenovo asked for a clarification
Aug 29th, 2019 – We sent a clarification
Aug 30th, 2019 – Status update from Lenovo
Sep 6th, 2019 – Status update from Lenovo
Sep 13th, 2019 – Lenovo confirmed the vulnerability
Sep 25th, 2019 – Lenovo shared a timeline for a fix deployment
Oct 22nd, 2019 – Lenovo issued CVE-2019-6189, and shared a final timeline for a public disclosure (End of November).
Nov 15th, 2019 – Lenovo said that they will disclose the issue on November 19th.
Nov 19th, 2019 – Lenovo published a security advisory[1]
References
[1] https://support.lenovo.com/us/en/product_security/LEN-29198