The first in a series of blogs from CEO, and former CISO, Guy Bejerano
Cybercriminals are running CISOs and security teams ragged. I know—before I founded SafeBreach, I was a CISO, working with my team to protect a global enterprise against breaches. A big part of my job was convincing business executives to invest more in security, rather than living with risk. But I also had to ensure my team was focusing on the right kind of defenses.
Fear as a weapon
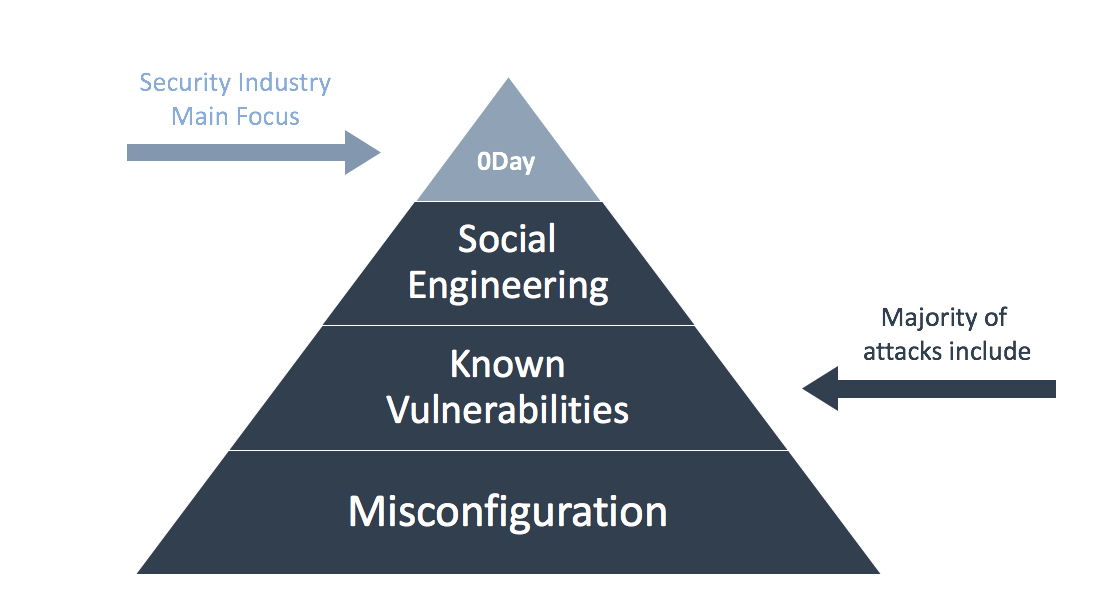
There’s a lot of buzz around advanced persistent threats (APTs) and zero-day threats (0days) in the cybersecurity space. Attending shows, or talking to peers, it’s easy to see that the entire industry is looking at ways to face these unique challenges. It’s hard to protect against the “new unknown” threat, but is this fear of the unknown driving more investment and activity than it might actually warrant?
Certainly, the fear is real. It drives us crazy! We set up traps, we analyze traffic patterns to find anomalies, we invest in new technologies that can’t really prove their effectiveness until an actual net-new attack occurs—all to calm our fear of the unknown. All in an attempt to stay ahead of a ghost; an imagined threat that we can’t name or identify until we see it. Now, this is important, but the problem is that this hunt is distracting us from protecting against the majority of successful attacks – those based on what has already been proven.
Facing our fears
So, what is the drive to search for the unknown? Let’s be honest: I think it often boils down to enthusiasm and interest, rather than pure logic.
- The sexiness factor: It’s often way more interesting and exciting to build traps and analyze new attacks than it is to make sure my 2factor authentication is working properly, or to sift through firewall rules to ensure I don’t have any FTP outbound connection that someone can use to exfiltrate my data.
- The “outsmarting” factor: Security-minded people tend to be smart. We are used to being able to win arguments, prove points, and arrive at smart conclusions. So when presented with a challenge like an APT or 0day, we can’t help but feel like we can think through the problem, and beat the bad guys! If we are in a search of the definite answer to ALL of our security problems, then why not start with the most difficult challenge? We have this belief that if we solve this high order problem, we will solve everything else.
Now, it’s always good to be smart. And it’s always good to be excited and motivated to solve problems. But if we only focus on the unknown, we risk losing sight of the biggest challenge, well, we risk losing sight of the more mundane attacks that are proven to breach networks and steal data.
This is our playground
Now, one truth of every single security team I’ve ever worked for, worked with, or even just heard about, is that we cannot simply “go after everything.“ We need to align our resources (money, people, and time) so that we aren’t spread too thin. However, if we only align around the 0day and unknown, then we expose ourselves to the vast majority of attackers—who will use any attack they can, whether new or old—to compromise our environments.
But 0days are not enough to complete a full attack. Each attack is composed of multiple logical steps that make up the kill chain. If we focus on breaking that kill chain, rather than just stopping 0days, we’ll still stop the overall attack – and likely many many more. And these kill chains can be broken with technology already in place—if only it is utilized in the right way.
Getting the most from what you have
Indeed, it’s often more effective to limit attackers’ moves by dealing with all the “known” breach methods first. In this way, certainly we can increase our chances to avoid the impact by eliminating all the “easy/known” attacks. We eliminate the vast majority of attacks, and now have only a small subset of “unknowns” to keep us up at night. And we can do this with more effective policy across the tools we already have.
But in order to improve our configuration to stop attacks, we have to ask ourselves, and our teams, some hard questions:
- Are we protected against known breaches? Apache Struts 2? WannaCry? Jaff? Etc.
- When was the last time we validated our controls against a known breach method? Regardless of whether it was a pen-test, red-team, hackers, breach and attack simulation or anything else—did those results go into a drawer over in operations?
- Do we know how our controls will act when a malicious actor strikes?
- Do we know what data is protected, and what’s vulnerable?
- Have we tested against inbound, lateral, and outbound attacks?
Start today, not 0day
Yes, fighting the 0day is important. But it’s more important not to let this chase to defocus us from the majority of gaps we (should) know how to face. Getting ahead of attacks means staying on top of proven methods, and making sure that our existing tools and processes work as anticipated. We can’t wait for a real attack to prove security – we need to be ready in advance. This is why I started SafeBreach – I believe that with focusing on the real problem we, as security professionals, can be more efficient and drive success rather than spending our efforts chasing after ghosts.