SafeBreach Labs has updated the Hacker’s Playbook™ with new simulations for IOCs described in US-CERT Continued Threat Actor Exploitation Post Pulse Secure VPN Patching (AA20-107A), as well as new findings from SafeBreach Labs. This alert warns of continued exposure and damage from the Pulse Secure VPN vulnerability CVE-2019-11510 that was reported in April, 2019.
The alert informs organizations which had CVE-2019-11510 exploited will continue to be attacked, because the unpatched initial attack allowed Active Directory credentials to be stolen. CISA identified the following malicious cyber actor actions occurring in a victim’s environment:
- Creating persistence via scheduled tasks/remote access trojans
- Amassing files for exfiltration
- Executing ransomware on the victim’s network environment
Those who carried out successful attacks prior to patching now have valid credentials, and as a result, antivirus and endpoint detection and response solutions will not detect their continued activity.
The alert provided mitigation efforts which include log monitoring of the Pulse Secure as well as running a detection tool CISA developed called check-your-pulse to hunt for the IOCs. If organizations detect evidence of CVE-2019-11510 exploitation, CISA recommends changing passwords for all Active Directory accounts, including administrators and services accounts.
New Findings from SafeBreach Labs
From the indicators supplied in this alert the SafeBreach Labs research team has uncovered another malware sample, Shelma, that was not reported as part of Alert (AA20-107A). SafeBreach Labs has validated that Shelma was used in at least one other instance in the wild, in February 2020. SafeBreach Labs warns that Shelma could be used by the same adversary to infect endpoints, without the Pulse Secure vulnerability addressed in the alert, from other VPN solutions by exploiting remote code execution.
Newly developed playbook methods related to AA20-107A:
- #4264 – Write ShelmaUSCERTAA20107Arelated malware to disk (Host-Level)
- #4265 – Transfer of ShelmaUSCERTAA20107Arelated malware over HTTP/S (Lateral Movement)
- #4266 – Transfer of ShelmaUSCERTAA20107Arelated malware over HTTP/S (Infiltration)
- #4267 – Email ShelmaUSCERTAA20107Arelated malware as a ZIP attachment (Lateral Movement)
- #4268 – Email ShelmaUSCERTAA20107Arelated malware as a ZIP attachment (Infiltration)
- #4269 – Communication with C&C using HTTPS (AA20-107A)
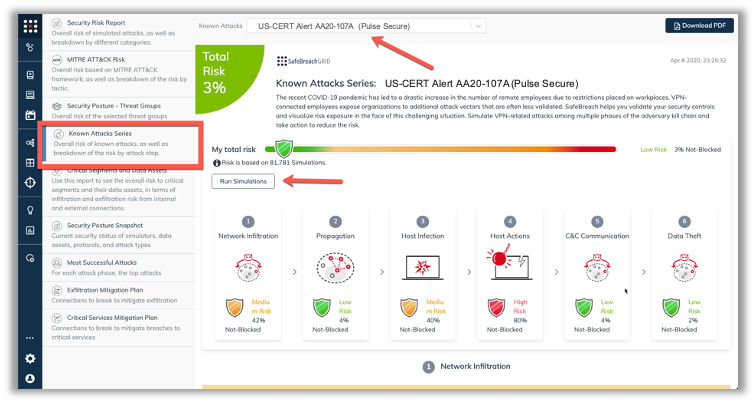
The new attack methods for US-CERT AA20-107A are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run just the specific attacks from this US-CERT alert. From the Known Attack Series report, select the US-CERT Alert AA20-107A (Pulse Secure) report and there is an option to Run Simulations which will run all the attack methods.