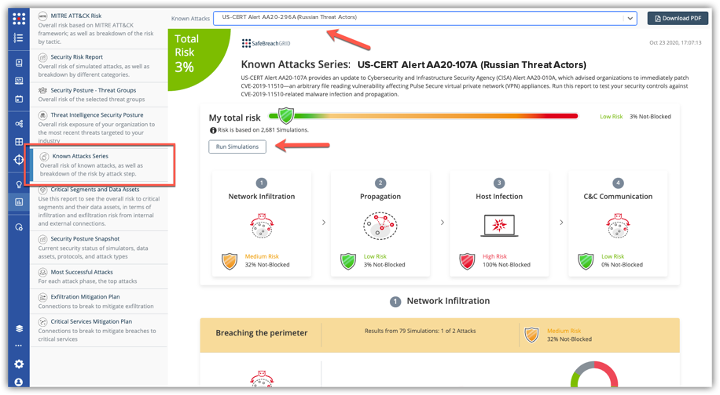
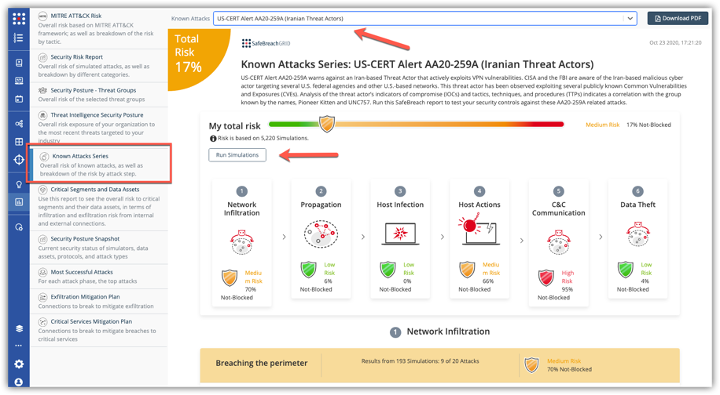
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have released two joint cybersecurity advisories on widespread advanced persistent threat (APT) activity in relation to their interference with the United States presidential elections. The SafeBreach Hacker’s Playbook™ already has coverage on attack methods detailed for both US-CERT alerts.
US CERT Alert (AA20-296A) details how Russian-sponsored APT actors obtain user and administrator credentials to establish initial access, enable lateral movement once inside the network, and locate high value assets in order to exfiltrate data.
US-CERT Alert (AA20-296B) Iranian APT actors use spear-phishing campaigns, website defacements, and disinformation campaigns to spread obtained U.S. voter-registration data, anti-American propaganda, and misinformation about voter suppression, voter fraud, and ballot fraud.
Listen below as Tomer Bar, Research Team Leader at SafeBreach, breaks down the techniques outlined in these CERT Alerts:
4 newly developed playbook methods related to AA20-296A:
Infiltration
- #5539 – Communication with Energetic_Bear using HTTP
- #5540 – Communication with a real malicious Energetic_Bear server using HTTP/S
- 5567 – Path Traversal of Fortigate VPN vulnerability CVE-2018-13379
- 5570 – Directory Traversal of Citrix ADC vulnerability CVE-2019-19781
10 existing playbook methods related to AA20-296A:
Infiltration
- 1306 – Brute force attack over the SMB protocol
- 1307 – Brute force attack over the SSH protocol
- 1309 – Brute force attack over the RDP protocol
- 1312 – MySQL Bruteforce Connection
- 1377 – Web app attack using SQL Injection
Lateral movement
- 172 – Brute force attack over SMB protocol
- 173 – Brute force attack over SSH protocol
- 192 – Brute force attack over RDP protocol
- 223 – Brute force attack based on MySQL
- 5487 – Exploit CVE-2020-1472 ZeroLogon
2 newly developed playbook methods related to AA20-296B:
Infiltration
- #5568 – Remote Exploitation of F5 VPN using CVE-2020-5902
- #5569 – Remote Exploitation of Telerik UI using CVE-2017-9248
What you should do now
The new attack methods for US-CERT AA20-296A and AA20-296B are already in the SafeBreach Hacker’s Playbook and ready to be run across your simulators. The Known Attack Series report is being updated so you can run the specific attacks from these US-CERT alerts. From the Known Attack Series report, select the US-CERT Alert AA20-296A (Russian Threat Actors) or AA20-296B (Iranian Threat Actors) report and select Run Simulations which will run all the attack methods.