Introduction
SafeBreach Labs discovered a new vulnerability in Forcepoint VPN Client software for Windows.
In this post, we describe the CVE-2019-6145 vulnerability we found in the Forcepoint VPN Client software. We then demonstrate how this vulnerability could have been exploited by an attacker during a post-exploitation phase in order to achieve privilege escalation, persistence and in some cases defense evasion by using the technique of implanting an arbitrary unsigned executable which is executed by a signed service that runs as NT AUTHORITY\SYSTEM.
Note: In order to exploit this vulnerability the attacker needs to have Administrator privileges.

Forcepoint VPN Client for Windows
The Forcepoint VPN Client, formerly known as Stonesoft VPN Client, provides a secure virtual private network (VPN) connection between end-user computers running on Microsoft Windows platforms and a Firewall/VPN gateway on Forcepoint Next Generation Firewall (Forcepoint NGFW).
Parts of the software run as a Windows service executed as “NT AUTHORITY\SYSTEM,” which provide it with very powerful permissions and capabilities.
Vulnerability
Discovery
In our initial exploration of the software, we targeted the “Forcepoint VPN Client Service” (sgvpn.exe), because:
- It runs as NT AUTHORITY\SYSTEM – the most privileged user account. This kind of service might be interesting when looking for privilege escalation to SYSTEM, which is very useful and powerful to an attacker.
- The executable of the service is signed by Forcepoint and if the hacker finds a way to be executed by it, it can be used as an application whitelisting bypass.
- This service automatically starts once the computer boots, which means that it’s a potential target for an attacker to be used as a persistence mechanism.
In our exploration, we found that after the Forcepoint VPN Client Service was started, the sgvpn.exe signed process was executed as NT AUTHORITY\SYSTEM.
We noticed an interesting behavior once the service’s process was executed:
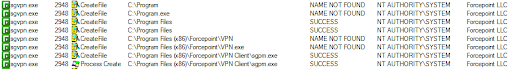
As it can be seen, the service was trying to look for multiple missing EXE files before it found and executed the real executable file (sgpm.exe):
- C:\Program.exe
- C:\Program Files (x86)\Forcepoint\VPN.exe
PoC Demonstration
In order to test this privilege escalation vulnerability, we compiled an EXE file (unsigned) which writes the following to the filename of a txt file:
- The name of the process which loaded it
- The username which executed it
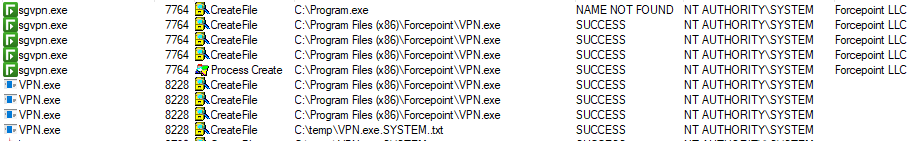
Our arbitrary unsigned EXE file was executed as NT AUTHORITY\SYSTEM by a legitimate process which is signed by Forcepoint LLC.
Root Cause Analysis
Once the sgvpn.exe is executed, it tries to execute the “sgpm.exe” file (according to the logs, it’s the Policy Manager of the software).
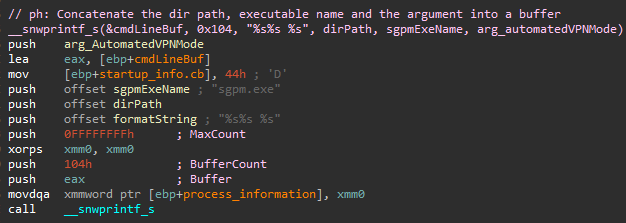
Using __snwprintf_s it assembles and writes to buffer the command line to be executed, using the following:
- The path of the directory which contains the executable (C:\Program Files (x86)\Forcepoint\VPN Client)
- “sgpm.exe”
- “-A” argument (Automated VPN Mode)
The call looks like this:
__snwprintf_s(&cmdLineBuf, 0x10, 0xFFFFFFFF, “%s%s %s”, dirPath, sgpmExeName, arg_automatedVPNMode);-
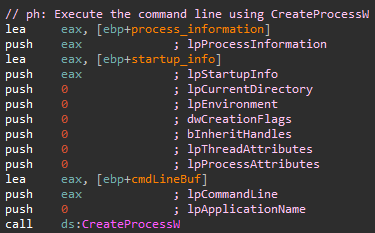
 Next, it executes the assembled command line using CreateProcessW.
Next, it executes the assembled command line using CreateProcessW.
The call looks like this:
CreateProcessW(NULL, &cmdLineBuf, NULL, NULL, 0, 0, NULL, NULL, &startupinfo, &processinformation);
Among the findings I’ve presented so far, there are two important things that lead to the root cause of this vulnerability:
- The first argument of the CreateProcessW function call is NULL.
- The command line buffer doesn’t contain any quoted string which separates the executable path from the argument.
**(A quick reminder: “%s%s %s”), which in our case turns to:
``C:\Program Files (x86)\Forcepoint\VPN Client\sgpm.exe -A”“**
According to the CreateProcessW function documentation in MSDN, we will see the following:
The lpApplicationName parameter can be NULL. In that case, the module name must be the first white space–delimited token in the lpCommandLine string.If you are using a long file name that contains a space, use quoted strings to indicate where the file name ends and the arguments begin; otherwise, the file name is ambiguous.
For example, consider the string "c:\program files\sub dir\program name". This string can be interpreted in a number of ways. The system tries to interpret the possibilities in the following order:
c:\program.exe c:\program files\sub.exe c:\program files\sub dir\program.exe c:\program files\sub dir\program name.exe
The root cause of this unquoted search path vulnerability happens because the command line doesn’t contain a quoted string between the path of the executable and the argument – so the CreateProcessW function tries to split it by itself each time it parses a space character:
“C:\Program.exe”“C:\Program Files (x86)\Forcepoint\VPN.exe”“C:\Program Files (x86)\Forcepoint\VPN Client\sgpm.exe -A”
Potential Malicious Uses and Impact.
Below we show three possible ways that an attacker could have leveraged the CVE-2019-6145 vulnerability we discovered and documented above.
Whitelisting Bypass
The vulnerability gives attackers the ability to be executed by a signed service. This ability might be abused by an attacker for different purposes such as execution and evasion, for example: Application Whitelisting Bypass.
Persistence Mechanism
The vulnerability gives attackers the ability to execute malicious payloads in a persistent way, each time the service is being loaded. That means that once the attacker drops a malicious EXE file in one of the paths we mentioned earlier, the service will load the malicious code each time it is restarted. This way it might not be detected by security products, because the service process which executes the attacker’s payload is signed, and executes it “natively.” No suspicious action is required by the attacker, it just executes the executable once it’s started
Privilege Escalation
The vulnerability provides an attacker with the ability to gain NT AUTHORITY\SYSTEM access as an Administrator.
Affected Versions
All Forcepoint VPN Client for Windows versions earlier than 6.6.1 are affected.
Timeline
Sep 5th, 2019 – Vulnerability Reported
Sep 5th, 2019 – Forcepoint has confirmed the vulnerability.
Sep 16th, 2019 – Forcepoint has issued CVE-2019-6145.
Sep 19th, 2019 – Forcepoint has patched and disclosed the vulnerability.
