
What is SafeBreach Labs?
SafeBreach Labs is the research and development arm of SafeBreach. SafeBreach Labs delivers cutting-edge vulnerability and cybersecurity research as well as novel product ideas. Real-world insights and observations of “in-the-wild” attacks, as well as in-depth and frequent conversations with the top cybersecurity researchers and CISOs worldwide, serve as the foundation for its research and product-related work.
Comprising of an elite team of white-hat hackers that work with the global cybersecurity community, the SafeBreach Labs team constantly monitors the threat landscape, sources intelligence feeds, and conducts original research to uncover novel threats. A key goal of the SafeBreach Labs team is to suggest specific and systemic ways to shore up global cybersecurity by identifying weaknesses in widely used software and networking products. These discoveries have allowed the team to consistently contribute to the industry-standard MITRE vulnerability database and push the envelope with new thinking around adversarial simulation.
SafeBreach understands the real-world impact of emerging threats on the enterprise. We also realize the importance of minimizing response time in the case of emerging threats. SafeBreach is currently the only BAS vendor in the market offering a 24-hour SLA for actionable, emerging threats highlighted in US-CERT Alerts and FBI Flash Alerts. The SafeBreach Labs team plays a pivotal role in enabling this 24-hour SLA. As soon as a new US-CERT Alert or FBI Flash Alert is announced, SafeBreach Labs’ researchers immediately begin analyzing the threat for actionable IOCs and TTPs that can be added to the SafeBreach platform. This enables SafeBreach customers to immediately and continuously validate their organizational security posture against the newly identified threats.
The Quest for Improving Global Cybersecurity: One CVE at a Time
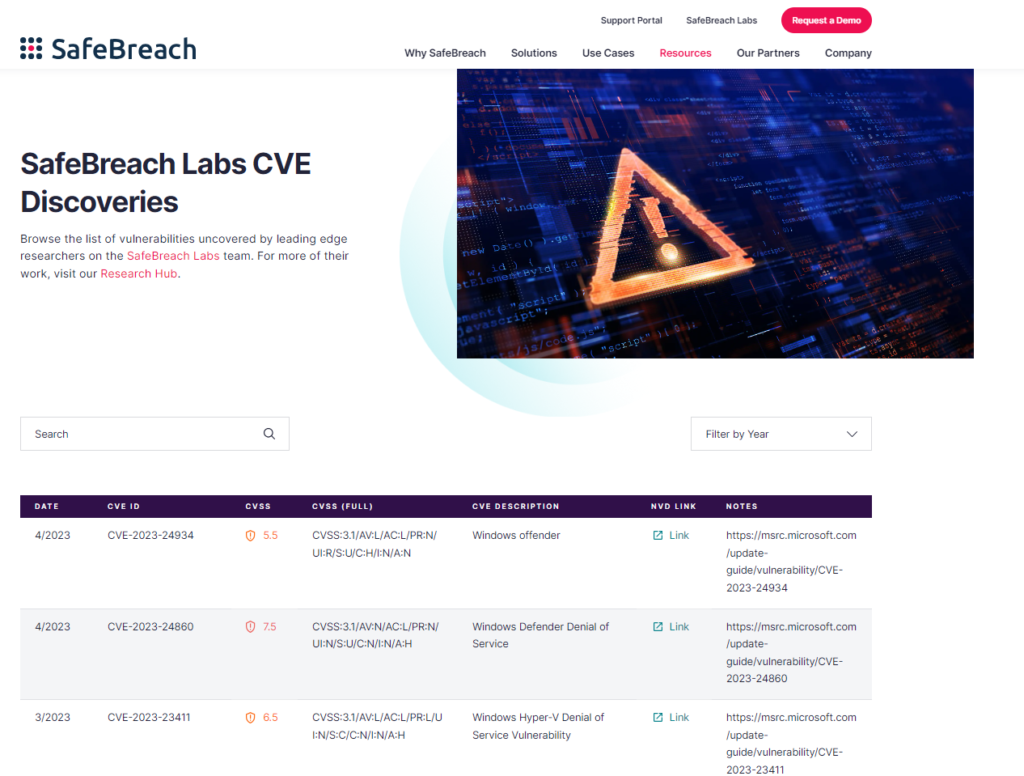
In April 2023, the SafeBreach Labs researchers identified and reported a new vulnerability in Microsoft Defender. The discovery of CVE-2023-24934, a Microsoft Defender Security Feature Bypass Vulnerability, makes it their 40th CVE discovery in the past 4 years. In addition to this discovery, the SafeBreach Labs team is also credited with the discovery of the following vulnerabilities. Full details can be found on this page: https://www.safebreach.com/cve-discoveries/
Who Are These Rockstars?

Tomer Bar: Tomer heads the SafeBreach Labs team. Tomer is a hands-on security researcher with over 20 years of unique cybersecurity experience. His main interests are vulnerability research, reverse engineering, and APT research. Among his recent discoveries are the PrintDemon vulnerabilities in the Windows Spooler mechanism, which were a candidate in the best privilege escalation of Pwnie awards and several research studies on Iranian APT campaigns. He has presented his research at DEF CON (28-30), BlackHat USA, ReCon, Sector, Confidence, Security Fest, HackCon, and Troopers conferences.
Upcoming Research Presentations –
- Black Hat 2023 – EDR = Erase Data Remotely, By Cooking An Unforgettable (Byte) Signature Dish
- Black Hat 2023 – Defender-Pretender: When Windows Defender Updates Become a Security Risk
- DEF CON 31 – Defender-Pretender: When Windows Defender Updates Become a Security Risk
Recent Original Research –
- OopSec – https://www.safebreach.com/resources/oopsec-mistakes-made-by-top-apts/
- Undetectable PowerShell – https://www.safebreach.com/resources/safebreach-labs-researchers-uncover-new-fully-undetectable-powershell-backdoor/
- CodeRAT – https://www.safebreach.com/resources/remote-access-trojan-coderat/
- Perfect Cyber Crime – https://www.safebreach.com/resources/the-perfect-cyber-crime/
- 2021 Our Journey Back To The Future Of Windows Vulnerabilities
Shmuel Cohen – Shmuel Cohen is a cybersecurity professional with a diverse background. After serving in the IDF (Israel Defense Force) for three years, he pursued a Bachelor of Science degree in Computer Science. He had the privilege of working at CheckPoint, where he spent 1.5 years developing software and another 1.5 years working as a malware security researcher. As his interest grew in vulnerability research, he made the decision to join SafeBreach, where he has been able to focus his energies on exploring and addressing vulnerabilities in cybersecurity.
Upcoming Research Presentations –
Omer Attias – Omer Attias is a security researcher with over 6 years of experience in cyber security. He started his professional career in the Ministry of Defense and then at the IDF. Most of his work is focused on network research, including Windows Internals and Linux kernel components.
Upcoming Presentations –
- Black Hat 2023 – Defender-Pretender: When Windows Defender Updates Become a Security Risk
- DEF CON 31 – Defender-Pretender: When Windows Defender Updates Become a Security Risk
Or Yair – Or Yair is a security researcher with over 5 years of experience in cyber security who started his professional career in the IDF. Most of his work is focused on platform research, including Linux kernel components and some Android as well. For the last two years, Or has been drawn into the Windows world and currently focuses on innovative vulnerability research of the operating system’s components. Or has already impacted threat mitigation by widely sharing his discoveries internationally at Black Hat Europe 2022, RSAC 2023, Security Fest 2023, and HackCon 2023.
Upcoming Research Presentations –
- Black Hat 2023 – One Drive, Double Agent: Clouded OneDrive Turns Sides
Recent Original Research–
- Aikido Wiper – https://www.safebreach.com/resources/safebreach-labs-researcher-discovers-multiple-zero-day-vulnerabilities/
- Unpatched Complex Active Directory Attacks – https://www.safebreach.com/resources/unpatched-complex-active-directory-attacks/
- Modern techniques used by Advanced Persistent Threat actors for discovering 0-day vulnerabilities – https://adversaryvillage.org/adversary-events/DEFCON-30/Or-Yair/
Eran Segal – Eran Segal is a research team leader, with more than 8 years of cybersecurity research experience. Over the last three years, he has been researching security projects in SafeBreach Labs, after serving in various security positions in the IDF. He specializes in research on Windows and embedded devices. Eran presented his research at BlackHat USA, DEF CON 28-29, and Sector conferences.
Recent Original Research –
- The COW (Container On Windows) Who Escaped the Silo
- 2021 Our Journey Back To The Future Of Windows Vulnerabilities
Alon Leviev – Alon Leviev is a security researcher with a diverse background. Alon started his professional career as a blue team operator, where he focused on the defensive side of cyber security. As his passion grew towards research, Alon joined SafeBreach as a threat security researcher. His main interests include operating system internals, reverse engineering, and vulnerability research.
Upcoming Research
Alon has completed his first research project and has shared the findings of his research with the concerned vendors. The results of this research will be published in the coming weeks.
Ariel Gamrian – Ariel Gamrian is a security researcher currently working with the Threat Security Research team at SafeBreach Labs. With a well-rounded background that includes serving as a Company Commander during his military tenure, over a year of experience in security research, and a strong foundation in software development, Ariel exhibits strong capabilities in his field. Ariel’s primary areas of focus include Windows internals and cloud research.
Upcoming Research
Ariel has identified and reported several vulnerabilities/issues with the concerned vendors and the results of his research will be published in the coming weeks.
Where Can I Learn More About Their Research
The SafeBreach Labs team is passionate about sharing their research with the global cybersecurity community. As part of this effort, they regularly present at prime cybersecurity conferences and publish their findings in a blog. For a full list of recently published original research as well as new attacks added to the SafeBreach platform by the SafeBreach Labs team, kindly check out our Inaugural Hacker’s Yearbook.

