The evaluation lab in Microsoft Defender for Endpoint makes it easy for organizations to build and run proofs of concept (PoCs) using real software and networking attack simulations in a safe and controlled way. SafeBreach was chosen by Microsoft to supply valuable attack simulations for users to effectively validate the security efficacy of their Microsoft Defender for Endpoint instance against several relevant and realistic advanced attacks. These built-in SafeBreach attacks markedly improve the capabilities of the lab; they enable PoCs to clearly demonstrate the effectiveness of various Microsoft Defender for Endpoint configurations and empower security teams to closely observe and review prevention, detection, and remediation features in action. These attacks and the reports they generate cover the full span of a real attack along the entire kill chain and provide users with valuable information including:
- Incidents that were triggered
- Generated alerts
- Assessments on exposure level
- Threat categories observed
- Detection sources
- Automated investigations
As the threat landscape continues to evolve, so do the attackers. The severity of these advanced threats is highlighted by the fact that Carbanak and FIN7 were chosen to be the subject of the 2020 MITRE ATT&CK Evaluations. The SolarWinds (Solorigate) Campaign was dubbed as “the largest and most sophisticated attack the world has ever seen”, leaving tens of thousands of organizations vulnerable.
“The addition of SafeBreach’s Carbanak+FIN7 and Solorigate attack simulations to our evaluation lab enables customers to test and improve their security posture against some of the most challenging threats facing companies today,” said Rob Lefferts, Corporate Vice President, Microsoft 365 Security. “Cyber-security is a team sport and partners like SafeBreach are critical to our efforts to continuously improve the ability of security teams to validate and optimize the efficacy of Microsoft Defender for Endpoint.”
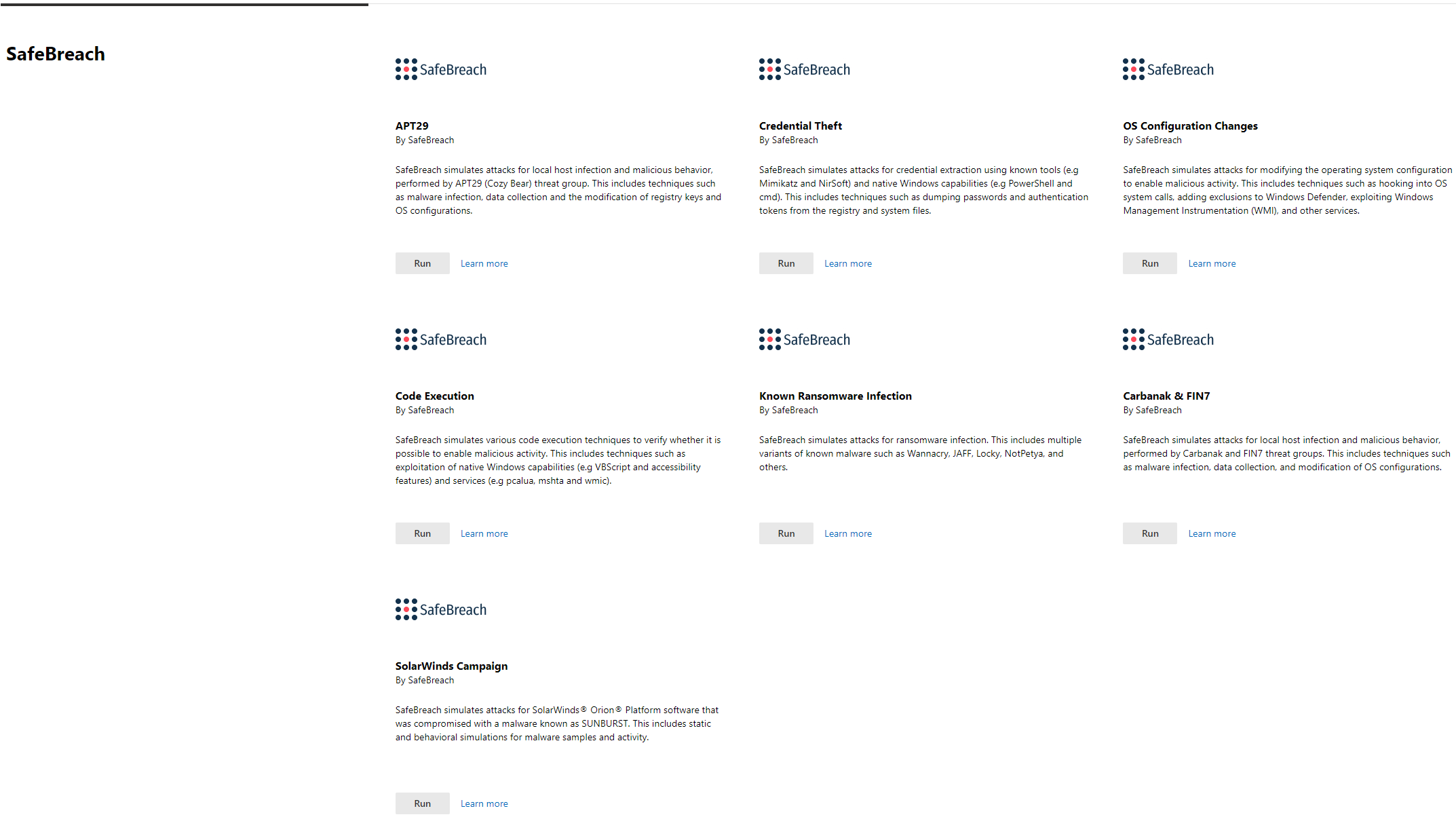
To improve the capabilities of the lab, SafeBreach is automatically deployed to run the Carbanak & FIN7, SolarWinds (Solorigate) Campaign Software Compromise, APT29, Credential Theft, OS Configuration Changes, Code Execution, and Known Ransomware Infection scenarios.
- (NEW) Carbanak+FIN7 Scenario – SafeBreach simulates attacks for localhost infection and malicious behavior, performed by Carbanak and FIN7 threat groups. This includes techniques such as malware infection, data collection, modification of OS configurations, and communication with C&C servers.
- (NEW) SolarWinds Campaign Scenario (Solorigate) – SafeBreach simulates attacks for SolarWinds Orion® Platform software that was compromised with malware known as SUNBURST. This includes static and behavioral simulations for malware samples and activity.
- APT29 Scenario – SafeBreach simulates attacks for localhost infection and malicious behavior, performed by the APT29 (Cozy Bear) threat group. This includes techniques such as malware infection, credential theft, data collection, and the modification of registry keys and OS configurations.
- Credential Theft Scenario – SafeBreach simulates attacks for credential extraction using known tools and native Windows capabilities. This includes techniques such as dumping passwords and authentication tokens from the registry and system files.
- OS Configuration Changes Scenario – SafeBreach simulates attacks for modifying the operating system configuration to enable malicious activity. This includes techniques such as hooking into OS system calls, adding exclusions to Windows Defender, exploiting Windows Management Instrumentation (WMI), and other services.
- Code Execution Scenario – SafeBreach simulates various code execution techniques to verify whether it is possible to enable malicious activity. This includes techniques such as exploitation of native Windows capabilities and services.
- Known Ransomware Infection Scenario – SafeBreach simulates attacks for ransomware infection. This includes multiple variants of known malware such as WannaCry, JAFF, Locky, NotPetya, and others.
Security teams using the evaluation lab do not need to make any code or configuration changes to run the new and existing SafeBreach attacks. Testers can simply select from one of the available scenarios in their evaluation lab control panel, immediately run the tests, and then receive the results for further validation and analysis.
Summary
The joint integration of SafeBreach, the market-leading security control validation solution, with the Microsoft Defender Evaluation Lab allows running a select group of highly relevant attacks against a fully configured Microsoft Defender for Endpoint instance. Incorporating SafeBreach’s simulated attacks into the validation process delivers a superior user experience for creating full-featured PoCs in the Microsoft Defender for Endpoint Evaluation Lab. This provides a risk-free way to evaluate and report on the performance of Microsoft Defender for Endpoint against advanced attacks.