
In this version of the Hacker’s Playbook Threat Coverage round-up, we are highlighting attack coverage for several new threats. SafeBreach customers can select and run these attacks and more from the SafeBreach Hacker’s Playbook™ to ensure coverage against these advanced threats. Additional details about the threats and our coverage can be seen below.
NEW Threat Group Scenarios
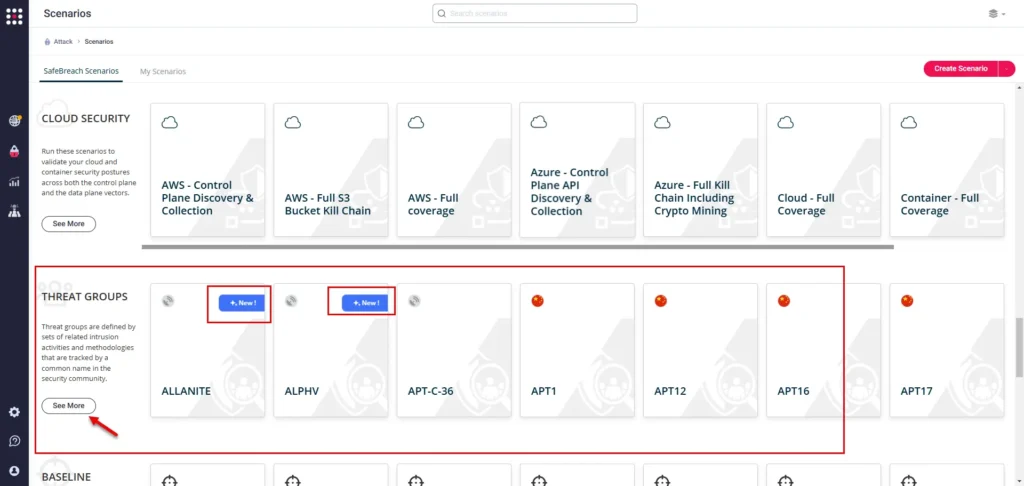
The SafeBreach platform now includes several NEW scenarios for MITRE ATT&CK recognized groups. This will allow enterprises to now run specific threat group focused scenarios to validate their organizational resilience against groups including:
- UNC1069
- TEMP Hermit
- Volt Typhoon
- Scattered Spider
- Cuboid Sandstorm
- CURIUM
- Confucius
- Lazarus Group
- Luminous Moth
- MoushtachedBouncer
- SideCopy
- UNC2970
- Mustard Tempest
- FIN13
- ToddyCat
- Aquatic Panda
- Malteiro
- ALPHV
- APT43
- ALLANITE
- Poseidon Group
To access these new scenarios, simply visit the Scenarios page and click on the “See More” button under Threat Groups. These new scenarios will have a NEW tag listed on them.
Bumblebee Malware – What you need to know
Threat researchers from Netskope labs have identified a new infection chain involving the use of Bumbleblee malware to deliver malicious payloads. It is believed that this is the first time this malware has been used since Europol ran Operation Endgame in May 2024 to disrupt several major botnets, including Bumblebee, IcedID, and Pikabot.
The researchers reveal that the infection begins via a phishing email that asks the targeted victim to download a ZIP file, extract its contents, and execute the file. The contents of this ZIP file are believed to be a LNK file titled “Report-41952.lnk” which once executed begins executing a chain of events that download and run the Bumblebee payload in the device memory. This is different as compared to previous infections where the Bumblebee payload required a DLL file to be written on the disk. Once opened, the LNK file executes a Powershell command to download an MSI file from a remote server, renames it as “%AppData%\y.msi”, and then executes/installs it using the Microsoft msiexec.exe tool.
The Bumblebee malware uses a clear-text hardcoded key as an RC4 key to decrypt the encrypted configuration. The decrypted port was 443 and the campaign ID was “msi” and “lnk001”.
SafeBreach Coverage of Bumblebee Malware
The following individual attacks were added to the Hacker’s Playbook and can be individually run to validate organizational controls:
- #10543 – Write Bumblebee ZIP file (de42fb) downloader to disk
- #10544 – Transfer of Bumblebee ZIP file (de42fb) downloader over HTTP/S
- #10545 – Transfer of Bumblebee ZIP file (de42fb) downloader over HTTP/S
- #10546 – Email Bumblebee ZIP file (de42fb) downloader as a compressed attachment
- #10547 – Email Bumblebee ZIP file (de42fb) downloader as a compressed attachment
- #10548 – Write Bumblebee MSI (6543f9) loader to disk
- #10549 – Transfer of Bumblebee MSI (6543f9) loader over HTTP/S
- #10550 – Transfer of Bumblebee MSI (6543f9) loader over HTTP/S
- #10551 – Email Bumblebee MSI (6543f9) loader as a compressed attachment
- #10552 – Email Bumblebee MSI (6543f9) loader as a compressed attachment
- #10553 – Write Bumblebee payload (00c115) loader to disk
- #10554 – Transfer of Bumblebee payload (00c115) loader over HTTP/S
- #10555 – Transfer of Bumblebee payload (00c115) loader over HTTP/S
- #10556 – Email Bumblebee payload (00c115) loader as a compressed attachment
- #10557 – Email Bumblebee payload (00c115) loader as a compressed attachment
Lynx Ransomware and INC Ransomware – What you need to know
Threat researchers from Unit42 have determined that the INC ransomware has a new successor that goes by Lynx ransomware. The group that has used these ransomware families has been observed actively targeting organizations across the retail, real estate, architecture, and financial and environmental sectors in the U.S. and UK.
While the Lynx ransomware shares source code similarities with the INC ransomware, the Lynx ransomware does not seem to currently have a Linux variant. It has only been targeting Windows machines, whereas INC ransomware had both Windows and Linux variants. Lynx ransomware threat actors leverage double extortion where they not only encrypt the victim machine, but the stolen data is also exfiltrated. If the victim refuses to pay ransom to decrypt the machine, the stolen data is often published on the dark web.
The Lynx ransomware can be delivered via –
- Phishing emails that deceive users into revealing sensitive information
- Malicious downloads that surreptitiously install the ransomware onto victims’ systems
- Hacking forums where cybercriminals share information and resources
The Lynx ransomware uses AES-128 in CTR mode and Curve25519 Donna encryption algorithms. All files are encrypted and have the .lynx extension appended to them. This malware version is designed for the Windows platform and is written in the C++ programming language. Its features include –
- Designating specific directories/files for encryption
- Terminating services/processes
- Encrypting network drives
- Mounting concealed disks
- Enabling or disabling background image alterations
- Printing all console logs
While the Lynx ransomware group is financially motivated, they claim to not target government entities, hospitals, or non-profit organizations.
SafeBreach Coverage of Lynx Ransomware & INC Ransomware
The following individual attacks were added to the Hacker’s Playbook and can be individually run to validate organizational controls:
- #10510 – Write LYNX (d6cf8b) ransomware to disk
- #10511 – Pre-execution phase of LYNX (d6cf8b) ransomware (Windows)
- #10512 – Transfer of LYNX (d6cf8b) ransomware over HTTP/S
- #10513 – Transfer of LYNX (d6cf8b) ransomware over HTTP/S
- #10514 – Email LYNX (d6cf8b) ransomware as a compressed attachment
- #10515 – Email LYNX (d6cf8b) ransomware as a compressed attachment
- #10516 – Write INC (5deced) ransomware to disk
- #10517 – Pre-execution phase of INC (5deced) ransomware (Windows)
- #10518 – Transfer of INC (5deced) ransomware over HTTP/S
- #10519 – Transfer of INC (5deced) ransomware over HTTP/S
- #10520 – Email INC (5deced) ransomware as a compressed attachment
- #10521 – Email INC (5deced) ransomware as a compressed attachment
Fire Chili Rootkit – What you need to know
Threat researchers from Hive Pro and Fortinet have observed Deep Panda, a Chinese APT group exploiting the Log4Shell vulnerability in VMware Horizon servers to deploy new root kit known as Fire Chili. This threat actor has targeted organizations including those in finance, travel, and education verticals.
These APT actors first exploit the Log4Shell (CVE-2021-44228) vulnerability in the vulnerable VMware Horizon servers launching a new PowerShell process that downloads and executes a series of scripts and installs the Milestone backdoor. This Milestone backdoor is leveraged to send complete user session information to the attacker’s remote servers. The Fire Chili rootkit is digitally signed with stolen certificates and its purpose is to hide the presence of malicious components on the compromised system.
SafeBreach Coverage of Fire Chili Rootkit
- #10522 – Write FireChili (acd87b) rootkit to disk (HOST_LEVEL)
- #10523 – Transfer of FireChili (acd87b) rootkit over HTTP/S (LATERAL_MOVEMENT)
- #10524 – Transfer of FireChili (acd87b) rootkit over HTTP/S (INFILTRATION)
- #10525 – Email FireChili (acd87b) rootkit as a compressed attachment (LATERAL_MOVEMENT)
- #10526 – Email FireChili (acd87b) rootkit as a compressed attachment (INFILTRATION)
EDRSilencer – What you need to know
According to TrendMicro researchers, EDRSilencer – a tool frequently used by red teamers has been observed being used to identify deployed security controls and mute their notifications and alerts to management consoles. EDRSilencer is an open-source tool inspired by MdSec NightHawk FireBlock, a proprietary pen-testing tool, which detects running EDR processes and uses Windows Filtering Platform (WFP) to monitor, block, or modify network traffic on IPv4 and IPv6 communication protocol.
In its latest version, EDRSilencer detects and blocks 16 modern EDR tools, including:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Secure Endpoint (formerly AMP)
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
EDRSilencer is designed to block network communication for processes associated with various EDR products. EDRSilencer gives attackers the option to add filters for specific processes by providing file paths, so it is possible to extend the list of targeted processes to cover various security tools. This allows malware or other malicious activities to potentially remain undetected.
SafeBreach Coverage of EDRSilencer
- #10558 – Write EDRSilencer (7888e7) hacktool to disk
- #10559 – Pre-execution phase of EDRSilencer (7888e7) hacktool (Windows)
- #10560 – Transfer of EDRSilencer (7888e7) hacktool over HTTP/S
- #10561 – Transfer of EDRSilencer (7888e7) hacktool over HTTP/S
- #10562 – Email EDRSilencer (7888e7) hacktool as a compressed attachment
- #10563 – Email EDRSilencer (7888e7) hacktool as a compressed
BeaverTail Infostealer and InvisibleFerret Backdoor – What you need to know
Threat researchers from Unit42 have tracked North Korean threat actors that have been masquerading as recruiters looking to install malware on devices associated with tech industry job seekers. The BeaverTail infostealer has been compiled using the Qt framework and is available in variants that can target Windows and MacOS platforms. The BeaverTail malware has also been used to deliver constant updates to the InvisibleFerret Backdoor.
The threat actors initiate contact with victims by inviting them to participate in an online interview where they try and convince the victim to download and install malware on their devices. After the technical interview is set up, the attacker asks the victim to execute malicious code which connects back to the attacker’s command and control (C2) server.
As the BeaverTail malware is coded in Qt, this allows the attackers to simultaneously create and compile applications for MacOS and Windows platforms. BeaverTail executes its malicious code in the background, collecting data and exfiltrating it from the victim’s host without any visible indicators. The Qt version of BeaverTail includes the following new features:
- Stealing browser passwords in macOS
- Stealing cryptocurrency wallets in both macOS and Windows
Additionally, the Qt version of BeaverTail targets 13 different cryptocurrency wallet browser extensions, compared to only nine wallets previously targeted by the JavaScript variant.
SafeBreach Coverage of BeaverTail Infostealer and InvisibleFerret Backdoor
- #10527 – Write BeaverTail_Mac (0b7132) infostealer to disk
#10542 – Email InvisibleFerret (9eb287) backdoor as a compressed attachment
#10528 – Transfer of BeaverTail_Mac (0b7132) infostealer over HTTP/S
#10529 – Transfer of BeaverTail_Mac (0b7132) infostealer over HTTP/S
#10530 – Email BeaverTail_Mac (0b7132) infostealer as a compressed attachment
#10531 – Email BeaverTail_Mac (0b7132) infostealer as a compressed attachment
#10532 – Write BeaverTail (deb3cd) infostealer to disk
#10533 – Pre-execution phase of BeaverTail (deb3cd) infostealer (Windows)
#10534 – Transfer of BeaverTail (deb3cd) infostealer over HTTP/S
#10535 – Transfer of BeaverTail (deb3cd) infostealer over HTTP/S
#10536 – Email BeaverTail (deb3cd) infostealer as a compressed attachment
#10537 – Email BeaverTail (deb3cd) infostealer as a compressed attachment
#10538 – Write InvisibleFerret (9eb287) backdoor to disk
#10539 – Transfer of InvisibleFerret (9eb287) backdoor over HTTP/S
#10540 – Transfer of InvisibleFerret (9eb287) backdoor over HTTP/S
#10541 – Email InvisibleFerret (9eb287) backdoor as a compressed attachment

