
Interactive, hands-on keyboard attack campaigns are employed by today’s most proficient threat actors to penetrate organizational defenses. The network perimeter is typically the initial line of defense against unauthorized access to an organization’s network and the sensitive data it contains. After infiltration, attackers establish command-and-control (C&C) and data exfiltration channels to receive malicious payloads and export stolen data. In the event that an adversary establishes a presence in your environment, an optimal network perimeter can minimize the business impact. Security teams can quickly recognize and terminate communication channels set up by threat actors by optimizing data egress filtering policies, thereby disrupting the export of any stolen data.
Below, we’ll discuss the state of network perimeters today and how security teams can benefit from regularly testing them. We’ll also explore where testing should occur and what should be tested. Next, we’ll discuss how implementation of a “Zero Trust” approach can be beneficial and how breach and attack simulation (BAS) can help. Finally, we will outline how SafeBreach Scenarios within the SafeBreach platform can be used to establish a security baseline and gain the level of continuous visibility needed to achieve a hardened security posture.
Is the network perimeter really dead?
Network perimeters are defined as the boundary between a secure internal network and the external world (i.e., the Internet). In recent years, organizations have increasingly transitioned to the cloud, implemented bring-your-own-device (BYOD) policies, and relied on Software-as-a-Service (SaaS) platforms. The traditional castle-and-moat approach, which involves hardening exterior defenses and blindly trusting everything inside the network, is no longer relevant or sufficient to safeguard an organization against advanced threats that can easily access the network through a vulnerable device or an employee, as a result of this shift. The approach is now obsolete or irrelevant due to the evolving threat landscape of today.
Advanced threat actors can rapidly circumvent conventional network security and establish communication channels to transmit malicious commands and payloads from outside the network, as well as to exfiltrate stolen data outside the network. An attacker can avoid defenses in one environment and obtain access to others due to the fact that today’s networks are essentially flat (i.e., minimal to no network segmentation). It is imperative that security teams conduct attack testing of the network perimeter (the initial line of defense) in all of their environments, including the cloud, data centers, sites, and zones, to identify the weak points where an adversary could potentially establish inbound and outbound communication channels and exploit the organization.
Where should security teams test?
An adversary can exploit any device with Internet access to establish communication channels for C&C and to exfiltrate stolen data. Devices that are Internet-enabled and can be exploited by a motivated threat actor to obtain access to your network—including workstations, servers, IoT devices, and even OT devices—should be evaluated regularly by security teams. Testing should encompass as many sites/business units as is feasible, including your cloud deployments. Special consideration should be given to critical business processes, as their exploitation has the potential to result in financial and reputational harm.
There are numerous industries that have stringent regulations (e.g., GDPR, HIPAA, PCI-DSS) that mandate organizations safeguard personal and financial data. Regular testing is essential for preventing substantial penalties and ensuring compliance with these laws.
Furthermore, the potential for anomalous or suspicious traffic patterns to be revealed through extensive testing across all of your deployments may suggest security incidents. By ensuring the early detection of any anomalies, security teams can respond more quickly, thereby minimizing damage and preventing further exploitation.
What should security teams test for?
Ingress Testing
Security teams should simulate attacks that threat actors may employ to breach network perimeters in order to validate them against unauthorized access attempts from external networks. These may encompass phishing, the exploitation of exposed services, port/protocol abuse, attempts to establish C&C channels, and more.
Teams can measure and improve the efficacy of their firewalls, intrusion detection/prevention systems (IDS/IPS), and SIEM tools by validating all deployed network tools against inbound threats. Furthermore, this serves to validate the principle of least privilege (Zero Trust), allowing you to ascertain whether an attacker can move laterally within your network or if your access controls will restrict this movement.
Egress Testing
Exfiltration, which involves the transfer of stolen data outside the network by attackers, is equally alarming, despite the importance of infiltration protection. Typically, the attacker establishes communication with external systems and moves data out, or downloads malicious payloads from external servers after infiltrating the network.
Egress testing replicates these activities to guarantee that malicious attempts are identified and prevented. Security teams can ensure that intruders are prevented from communicating with external C&C servers and from exfiltrating data out of the network by implementing a robust egress filtering policy. It is crucial to bear in mind that security teams are required to monitor for anomalous data activity in both covert and overt communication channels.
How does establishing a “Zero Trust” approach help?
The “Zero Trust” approach operates on the principle of “never trust, always verify.” With this approach, every request regardless of whether it comes from inside or outside the network is treated as if it comes from an untrusted source. Key principles of Zero Trust include:
- Principle of Least Privilege: Users and systems are given the lowest level of access needed to perform their tasks, thereby reducing the risk of unauthorized access.
- Ongoing, Continuous Verification: Each and every attempt to access resources inside the network is constantly monitored and verified, regardless of whether it was previously authenticated.
- Micro-Segmentation: Each network gets divided into smaller segments and access to each segment/zone is controlled, thereby reducing the risk of lateral propagation in the event of a breach.
- Analytics: User behavior and device activity are continually monitored to identify any anomalous traffic patterns that could reveal the presence of a threat inside the network.
Implementation of the Zero Trust approach across inbound and outbound traffic can help organizational security teams protect the organization against today’s advanced threat actors.
How can BAS tools help establish a Zero-Trust approach?
Zero-Trust for Inbound Traffic
For inbound traffic, every entity requesting access is considered malicious until authenticated. BAS tools can help security teams validate the effectiveness of their network security controls by simulating realistic attacks to identify gaps in your network defenses. BAS does this in a wide variety of ways, including:
- Simulating phishing attacks to validate detection and prevention of phishing attempts.
- Simulating vulnerability exploitation to identify ways a threat actor can gain access to the network.
- Simulating inbound attacks from unusual ports to ensure that network controls can detect and block them.
By ensuring a granular level of access control, continuous threat monitoring, and hardened organizational network defenses, security teams can reduce the impact of external threats via unauthorized access.
Zero-Trust for Outbound Traffic
Just like inbound traffic, every outbound traffic request needs to be authenticated and verified to ensure it is not malicious. BAS tools can help continuously validate the effectiveness of your network tools by simulating things like data exfiltration attempts and C&C communication to identify gaps in these outbound defenses. BAS does so by:
- Simulating data exfiltration over encrypted channels using HTTP/FTP or sending attachments via email.
- Simulating attempts to communicate with external C&C servers to identify whether firewalls and existing egress filtering rules can effectively detect and block them.
How can SafeBreach Scenarios be used to establish a security readiness baseline?
SafeBreach Scenarios enable security teams to easily find and execute attacks that help them reach the level of continuous visibility needed to achieve a hardened security posture. Each SafeBreach Scenario covers a use case from the real world that is organized into a sequence of steps, mimicking the threat’s progression. This enables organizations to validate their protection against those threats more realistically.
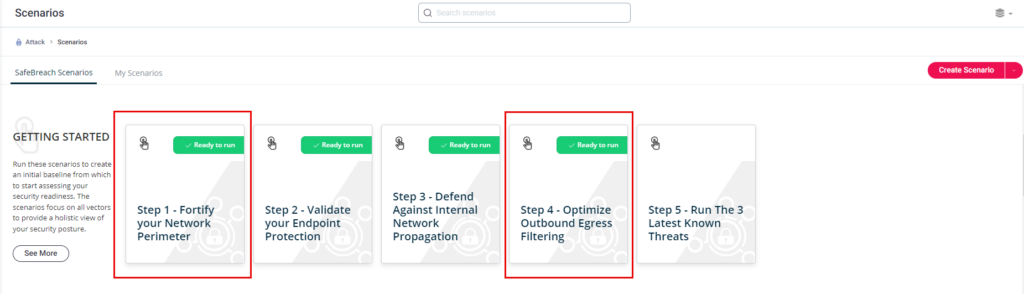
By providing pre-defined attack stories, SafeBreach makes it quicker and easier to leverage the various attack capabilities and understand which attack methods need to be tested. When first getting started with SafeBreach, we recommend running the Getting Started scenarios. These scenarios provide a benchmark of expected security posture for various activity types within your environment.
To set up a baseline for your inbound traffic, SafeBreach offers the Fortify your Network Perimeter scenario, which will run infiltration attacks against your perimeter defenses with a variety of threats that are expected to be blocked by the network perimeter. This scenario will help you identify gaps in your first line of defense and remediate them.
To optimize your outbound filtering policy, SafeBreach’s Optimize Outbound Egress Filtering scenario will replicate various malicious behaviors and activities around communication channels and exfiltration of sensitive data. This scenario will help identify areas where protocol adherence and enforcement can help reduce the risk of attacks.
SafeBreach security experts recently demonstrated how the SafeBreach platform can help you visualize, assess, and harden your perimeter defenses, ensuring security standards are set across all environments, including the cloud, data centers, sites, and zones. This assessment demonstration included:
- Running infiltration simulations against perimeter defenses to identify gaps in the network perimeter
- Testing network egress filtering policy by performing malicious behaviors and activities around exfiltration of sensitive data
- Highlighting ways of optimizing network protection and data egress policies to harden the organizational security posture
View the complete discussion below to ensure your organization can protect itself from today’s malicious threats and their impact on your organizational posture and reputation. Schedule a consultation with a SafeBreach team member to learn more about this capability. If you are an existing SafeBreach customer and would like to leverage these capabilities in your organization, please reach out to your customer success representative.

