On December 5th, the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory that confirmed the exploitation of CVE-2023-26360 at a Federal Civilian Executive Branch (FCEB) agency by unknown threat actors. Exploiting this vulnerability allowed threat actors to gain access to the FCEB agency network on two separate occasions in June 2023. This vulnerability affects Adobe ColdFusion versions 2018 Update 15 (and earlier) and 2021 Update 5 (and earlier) as well as earlier installations of the software that Adobe no longer supports. Detailed information is listed in US-CERT Alert AA23-339A – Threat Actors Exploit Adobe ColdFusion CVE-2023-26360 for Initial Access to Government Servers.
Adobe ColdFusion is a commercial application server used for rapid web application development. ColdFusion supports proprietary markup languages for building web applications and integrates external components like databases and other third-party libraries. ColdFusion uses a proprietary language, ColdFusion Markup Language (CFML), for development but the application itself is built using JAVA.
Technical Details
The FCEB agency conducted a thorough investigation of these incidents which revealed that in June 2023 unidentified threat actors were able to exploit CVE-2023-26360 and gain an initial foothold on two agency servers on two separate occasions. The investigation also revealed that Microsoft Defender for Endpoint (MDE) altered security teams of potential exploitation of the vulnerability on the public-facing web servers in their pre-production environment. The investigation also revealed that both servers were running outdated versions of the Adobe software which made them vulnerable to various exploits. It is believed that exploiting the vulnerability allowed the threat actors to drop malware using the HTTP POST command to conduct reconnaissance and map the overall network.
During the first incident (around June 26th, 2023), threat actors were able to exploit CVE-2023-26360 and gain initial access to a public-facing web server that was running Adobe ColdFusion v2016.0.0.3. After gaining access, they immediately began gathering information about all the currently active processes running on the web server and tested their network connectivity. Threat actors were observed traversing the filesystem and uploading various artifacts to the web server. Their activities included deleting files used in the attack to hide their presence and creating files in the C:\IBM directory to facilitate malicious operations undetected. The malicious code found on the system during this incident contained code that, when executed, would attempt to decrypt passwords for ColdFusion data sources. As the agency servers were running a newer version during the compromise, the malicious code failed to decrypt the passwords.
During the second incident that occurred on June 2nd, 2023, threat actors successfully exploited CVE-2023-26360 on a web server running Adobe ColdFusion v2021.0.0.2 to gain initial access. They were then able to enumerate domain trusts to identify potential lateral movement opportunities. Additionally, they were able to gather information about local and domain admin accounts by using commands like localgroup, net user, net user /domain, and ID. They continued performing recon to discover the overall network configuration, time logs, and query user information. The attackers also gathered user account information before dropping a text file that decoded as a remote access trojan (d.jsp). They then attempted to exfiltrate Registry files and security account manager (SAM) information.
The investigation concluded that in both cases these attacks were detected and blocked before the attackers were able to exfiltrate any valuable data or move laterally within the agency network. Security teams were also able to remove the compromised assets within 24 hours.
Important Note for SafeBreach Customers – Coverage for AA23-339A (Adobe ColdFusion Vulnerability)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers were already protected against some of the behavioral attacks identified in the advisory. Please run/ re-run the attacks listed below to ensure your environments are protected against this malware variant.
NEW Behavioral Attacks Related to CERT Alert
- (T1190) – Exploit Public-Facing Application
- #9394 – Remote exploitation of Adobe ColdFusion vulnerability CVE-2023-26360 (WAF)
NEW IOC-Based Attacks Related to CERT Alert
- ForkDump
- #9388 – Write ForkDump (73c864) hacktool to disk
- #9389 – Pre-execution phase of ForkDump (73c864) hacktool (Windows)
- #9390 – Transfer of ForkDump (73c864) hacktool over HTTP/S
- #9391 – Transfer of ForkDump (73c864) hacktool over HTTP/S
- #9392 – Email ForkDump (73c864) hacktool as a compressed attachment
- #9393 – Email ForkDump (73c864) hacktool as a compressed attachment
Existing Behavioral Attacks Mapped to the CERT Alert
- (T1003.001) – Credential Dumping: LSASS Memory
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32,
- (T1003.002) – Credential Dumping: Security Account Manager
- #7169 – Dump the SAM database from the registry (Windows)
- (T1564.001) – Hide Artifacts: Hidden Files and Directories
- #2124 – Hide a file – Windows
- (T1482) – Domain Trust Discovery
- #2306 – Domain Trust Discovery
- (T1087.001) – Local Account
- #2174 – Extract users and groups using net.exe (Windows)
- (T1518) – Software Discovery
- #2188 – Extract Process List using Windows Commands
- (T1046) – Network Service Scanning
- #8020 – Port scanning of local subnet network
What You Should Do Now
The playbook has been updated with new attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
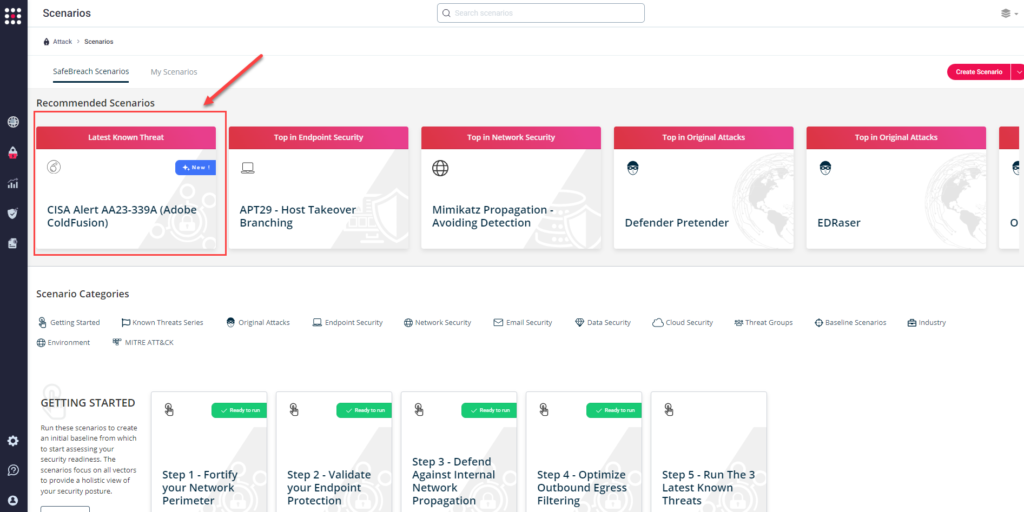
Method 1 – You can go to the “SafeBreach Scenarios” page and choose the AA23-339A (Adobe ColdFusion) scenario from the list of available scenarios.
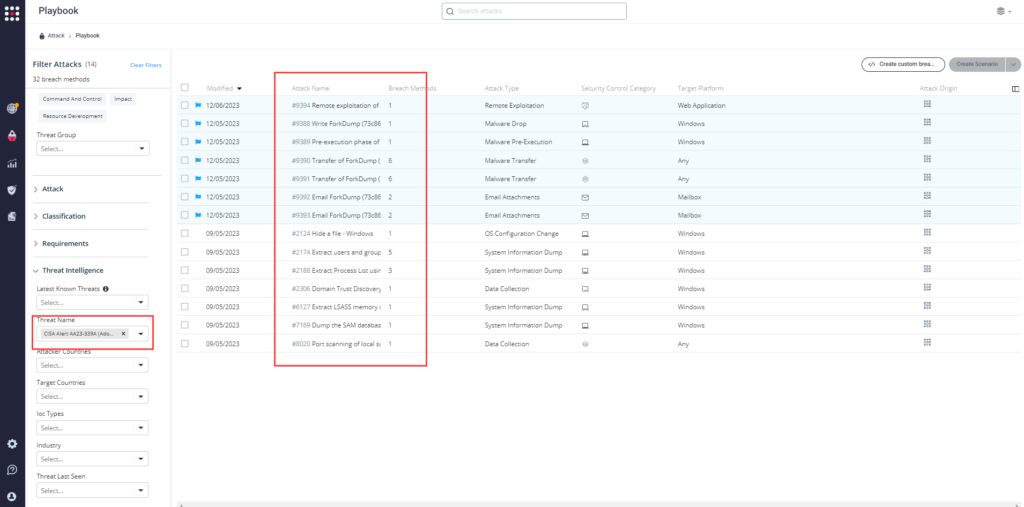
Method 2 – From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-339A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
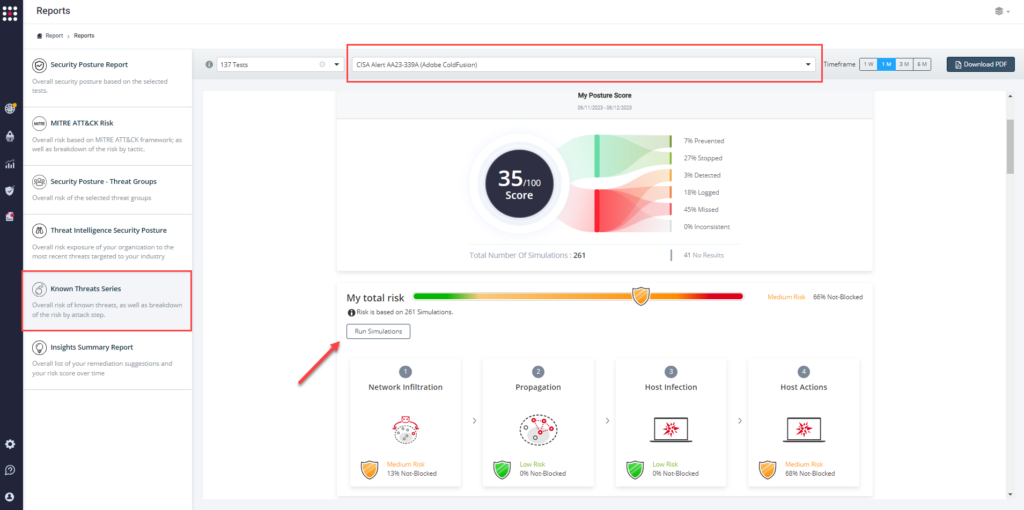
Method 3 – From the Known Attack Series report, select the AA23-339A (Adobe ColdFusion) report and select Run Simulations which will run all attack methods.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Prioritize remediating known exploited vulnerabilities.
- Employ proper network segmentation.
- Enable multifactor authentication (MFA) for all services to the extent possible, particularly for webmail, VPN, and accounts that access critical systems.
- For detailed information about mitigations and incident response, please refer to the full advisory

