The Cybersecurity and Infrastructure Security Agency (CISA) shared the findings of an investigation by numerous cybersecurity agencies worldwide on May 9th, exposing the malicious cyberespionage operations carried out by the Russian FSB utilizing the “Snake” malware. The US-CERT Alert (AA23-129A) Hunting Russian Intelligence “Snake” Malware provided information about this investigation and takedown (along with attacker TTPs and IOCs).
According to the advisory, the Snake implant is considered the most sophisticated cyber espionage tool designed and used by Center 16 of Russia’s Federal Security Service (FSB) for long-term intelligence collection on sensitive targets. To facilitate the collection of intelligence, the FSB created a covert peer-to-peer (P2P) network of numerous Snake-infected computers worldwide. Many systems in this P2P network serve as relay nodes that route disguised operational traffic to and from Snake implants on the FSB’s ultimate targets.
According to CISA, Snake infrastructure has been identified in over 50 countries across North America, South America, Europe, Africa, Asia, and Australia, including the United States and Russia itself. FSB has been using Snake malware to gather sensitive information from tactical targets including high-priority targets, such as government networks, research facilities, and journalists. In one instance the Snake malware was even observed exfiltrating sensitive international relations documents, as well as other diplomatic communications, from a victim in a North Atlantic Treaty Organization (NATO) country. Within the United States, the FSB has victimized industries including education, small businesses, and media organizations, as well as critical infrastructure sectors including government facilities, financial services, critical manufacturing, and communications.
Technical Details about Snake Malware
The FSB began first began developing Snake in late 2003 and continued to improve and enhance its capabilities over the years. CISA has determined that Snake is the most sophisticated cyber espionage tool in the FSB’s arsenal. Snake employs means to achieve a rare level of stealth in its host components and network communications. Snake’s internal technical architecture allows for the easy incorporation of new or replacement components. This design also facilitates the development and interoperability of Snake instances running on different host operating systems. Snake demonstrates careful software engineering design and implementation, with the implant containing surprisingly few bugs given its complexity.
Additionally, it is also revealed that FSB has been actively implementing new techniques to evade detection given the global, open-source efforts to reveal Snake’s existing TTPs. These modifications make it more challenging to identify and collect Snake-related artifacts, thereby hampering detection efforts by the host- and network-based defensive tools.
The FSB typically deploys Snake to external-facing infrastructure nodes on a network, and from there use other tools and TTPs on the internal network to conduct additional exploitation operations. Upon gaining and cementing ingress into a target network, the FSB typically enumerates the network and works to obtain administrator credentials and access domain controllers. FSB employs a wide array of mechanisms to gather user and administrator credentials in order to expand laterally across the network, including keyloggers, network sniffers, and open-source tools.
Snake’s modern architectural design allows it to use multiple different components for the same purpose, choosing the specific component based on its victim’s environmental considerations. Each layer of the Snake network protocol stack solely implements a specified interface for operability with the two adjacent layers. The encryption layer and underlying transport layer thus function independently, so any custom Snake network protocol can employ an encryption overlay without any change to the encryption layer code. This modularity allows Snake operators to choose the most logical network transport for the given environment without affecting Snake’s other functionality.
Important Note for SafeBreach Customers – Coverage for AA23-129A (Snake Malware)
As soon as details were made available, the SafeBreach Labs teams modified, mapped, and updated existing Hacker’s Playbook attacks to this threat immediately. SafeBreach customers can run/ re-run the attacks listed below to ensure their environments are protected against this nation-state threat.
Existing Behavioral Attacks Related to US-CERT Alert AA23-129A:
- #100 – Covert data asset exfiltration over TCP (Data) (exfiltration)
- #101 – Covert data assets exfiltration over UDP (exfiltration)
- #105 – Covert data asset exfiltration using HTTP/S (URI) (exfiltration)
- #106 – Covert data exfiltration using HTTP (GET) (exfiltration)
- #109 – Covert data asset exfiltration using HTTP/s GET (exfiltration)
- #110 – Covert data asset exfiltration using HTTPS POST (exfiltration)
- #112 – Covert data asset exfiltration over ICMP ping back (exfiltration)
- #1263 – Data asset exfiltration over TCP (exfiltration)
- #131 – Data asset exfiltration over UDP (exfiltration)
- #1900 – Capture network packets using Libpcap (Linux) (host level)
- #1901 – Capture network packets using WinPcap (Windows) (host level)
- #2124 – Hide a file – Windows (host level)
- #2175 – Discover Linux user configurations using Bash (Linux) (host level)
- #2192 – Collect Data from Local Shared Drives using System Commands (host level)
- #2199 – Space after Filename (Linux, macOS) (host level)
- #2246 – Hooking of GetSystemTime function using mavinject.exe with a custom DLL (host level)
- #2248 – Masquerading (host level)
- #2293 – Create and Start a Service (host level)
- #2306 – Domain Trust Discovery (host level)
- #6127 – Extract LSASS memory dump using PowerShell and Rundll32 (host level)
- #6799 – Domain Controller discovery using interactive session token (host level)
- #6800 – Domain Controller discovery using user credentials (host level)
- #6806 – Write data into a resource fork of a file (host level)
- #905 – Start the remote registry service (host level)
- #6809 – Execute DLL by signed executable (igfxtray.exe) (host level)
- #7046 – Communication via TOR (Windows) (host level)
- #7142 – Samba network share discovery and collection (lateral movement)
- #7167 – Covert data asset exfiltration over TOR (Windows) (exfiltration)
- #7168 – Enable a default account and add it to a Localgroup (Windows) (host level)
- #7219 – Collection – Keylogger (Windows) (host level)
- #803 – Enable Administrator Shares (host level)
- #806 – Collect Files using ZIP (host level)
- #8304 – Pack executable using Kiteshield packer and execute it (infiltration)
- #8305 – Pack Trickbot trojan using Kiteshield packer and drop to disk (lateral movement)
- #8306 – Pack executable using Midgetpack packer and execute it (infiltration)
- #8328 – Rename System Utilities (Linux) (host level)
- #8362 – Dynamic API resolution (host level)
- #904 – Start the secondary logon service (host level)
Existing IOC-Based Attacks Related to US-CERT Alert AA23-129A:
- #8802 – Write Snake ransomware to disk
- #8803 – Pre-execution phase of Snake ransomware (Windows)
- #8804 – Transfer of Snake ransomware over HTTP/S
- #8805 – Transfer of Snake ransomware over HTTP/S
- #8806 – Email Snake ransomware as a ZIP attachment
- #8807 – Email Snake ransomware as a ZIP attachment
- #8808 – Write Snake (EKANS) ransomware to disk
- #8809 – Pre-execution phase of Snake (EKANS) ransomware (Windows)
- #8810 – Transfer of Snake (EKANS) ransomware over HTTP/S
- #8811 – Transfer of Snake (EKANS) ransomware over HTTP/S
- #4998 – Pre-execution phase of Ekans Ransomware (3d1cc4)
- #4999 – Write Ekans Ransomware (3d1cc4) to disk
- #5000 – Transfer of Ekans Ransomware (3d1cc4) over HTTP/S
- #5001 – Transfer of Ekans Ransomware (3d1cc4) over HTTP/S
- #5002 – Email Ekans Ransomware (3d1cc4) as a ZIP attachment
- #5003 – Email Ekans Ransomware (3d1cc4) as a ZIP attachment
What You Should Do Now
Several attack methods related to this US-CERT Alert were already present in the SafeBreach Hacker’s Playbook™. The playbook has been updated with attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
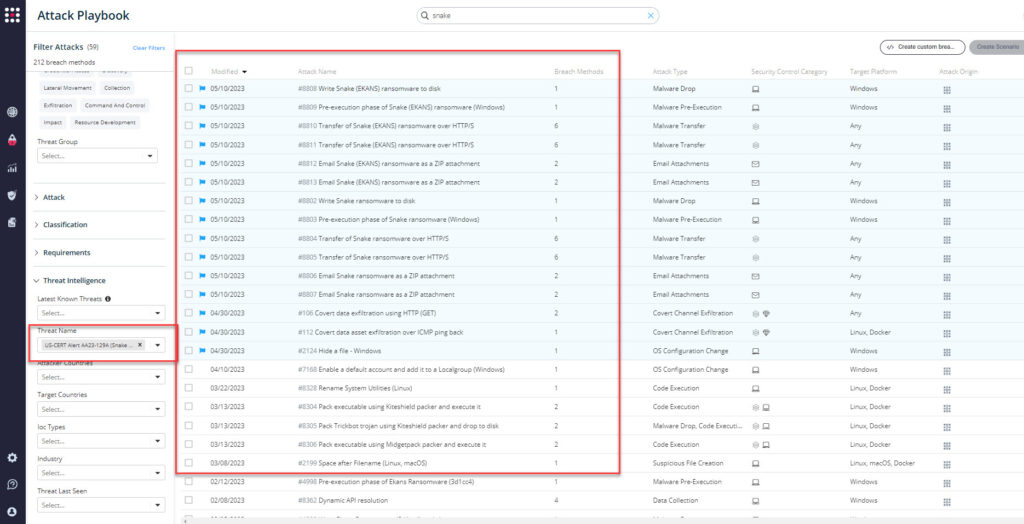
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-129A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
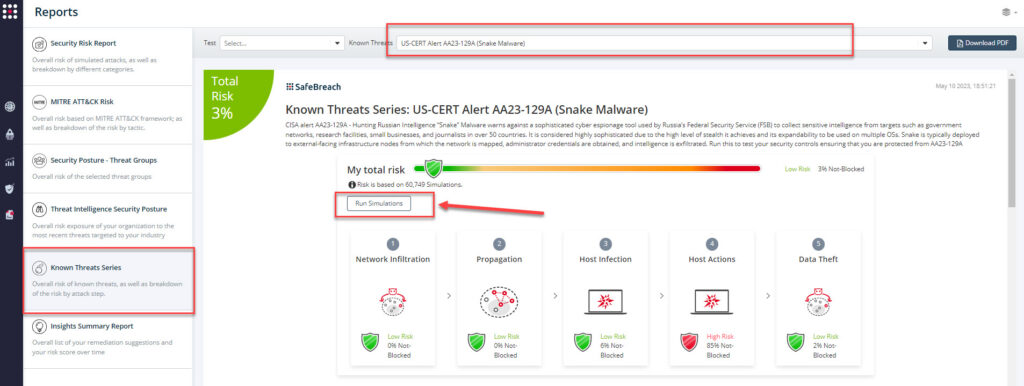
From the Known Attack Series report, select the AA23-129A (Snake Malware) report and select Run Simulations which will run all attack methods.
You can also go to “SafeBreach Scenarios” page and choose the AA23-129A (Snake Malware) scenario from the list of available scenarios.

NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats.
- Leverage Network Intrusion Detection Systems (NIDS) to feasibly identify some of the more recent variants of Snake and its custom network protocols listed in the advisory
- Leverage host-based detection to identify Snake malware’s host-based artifacts
- Perform memory analysis to gain visibility into Snake’s behaviors and artifacts
- Change credentials and apply regular updates
- Execute organizational incident response plan
- For detailed information about mitigations, please refer to the full advisory

